
DEPARTMENT OF THE AIR FORCE
Headquarters US Air Force
Washington, DC 20330-1030
CFETP 1D7XX/X
Parts I and II
31 July 2023
AFSC 1D7XX/X
CYBER DEFENSE
OPERATIONS
CAREER FIELD EDUCATION
AND TRAINING PLAN
ACCESSIBILITY: Publications and forms are available on the e-publishing website at
www.e-publishing.af.mil or Q-Flight at https://usaf.dps.mil/teams/10445/.
RELEASABILITY: There are no releasability restrictions on this publication.
BASIC
SENIOR MASTER
This CFETP was developed in accordance with DAFMAN 36-2689, Training Program

2
CYBER DEFENSE
OPERATIONS AFSC 1D7XX/X
CAREER FIELD EDUCATION AND TRAINING PLAN
TABLE OF CONTENTS
PART I
Preface ............................................................................................................................................. 4
Abbreviations/Terms Explained ..................................................................................................... 5
Section A - General Information ................................................................................................... 15
Purpose of the CFETP
Use of the CFETP
Coordination and Approval of the CFETP
Section B - Career Field Progression and Information ................................................................. 17
Specialty Description
Air Force Career Field Manager (AFCFM) for the Cyber Defense Operations Career Field
MAJCOM Functional Manager (MFM) for the Cyber Defense Operations Career Field
Skill/Career Progression
1D7XX/X Career Path
Chart Training Decisions
Community College of the Air Force Academic Programs
CCAF Instructor Certifications
General Education Mobile/Air University Associate-to-Baccalaureate Cooperative
Air Force Credentialing Opportunities On-Line (COOL)
Career Field Path
Education and Training Path Table
Section C - Skill Level Training Requirements ............................................................................ 22
Purpose
Specialty Qualification Requirements
Apprentice (3-Level) Training
Journeyman (5-Level) Training
Craftsman (7-Level) Training
Superintendent (9-Level) Training
Occupational Badge
Section D - Resource Constraints ................................................................................................. 25
Purpose
Apprentice (3-Level) Training
Journeyman (5-Level) Training
Craftsman (7-Level) Training
Section E - Transition Training Guide .......................................................................................... 25

3
PART II
Section A - Specialty Training Standard (STS) ............................................................................ 26
Qualitative Requirements ................................................................................................... Atch 1
1D7XX STS ....................................................................................................................... Atch 2
1D7X1P STS ...................................................................................................................... Atch 3
1D7X1Q STS ..................................................................................................................... Atch 4
1D7X1M STS .................................................................................................................... Atch 5
1D7X1W STS .................................................................................................................... Atch 6
1D7XX/X Legacy STS ..................................................................................................... Atch 7
Section B - Course Objective List ................................................................................................. 30
Section C - Support Materials ....................................................................................................... 30
Air Force Job Qualification Standards and Air Force Qualification Training Packages
Section D - Training Course Index ............................................................................................... 30
Purpose
Air Force In-Residence Courses
Air University Courses
Exportable Courses
Section E – MAJCOM-Unique Requirements .............................................................................. 30
OPR: AF A2/6FC
Certified By: CMSgt Victor Cordero Jr., AF A2/6FC
Supersedes: 1D7XX/X CFETP, 13 April 2022; 3DXXX CFETP, 27 December 2020; 3D1X4
CFETP, 30 November 2015; and 3D1X7 CFETP, 29 October 2019
Pages: 33
4
PART I
Preface
1.
The dynamic nature of the Cyberspace landscape necessitates foresight, readiness,
and vigilance to ensure that Airmen possess the required expertise, skillset, and
resources to deliver vital cyberspace capabilities for today's Air Force mission while
preparing for the challenges of tomorrow's highly competitive arena. The growing focus
on Joint All Domain Command and Control (JADC2) and Information Operations
aligns with the rapid pace of change. This transition from functionally stove-piped
AFSCs to a consolidated mission-driven capability model fosters greater synergy and
effectiveness. This Cyber Defense Operations Career Field Education and Training Plan
(CFETP) outlines the foundational life cycle education and training requirements,
resources, and core tasks for each specialization within this new framework. The
CFETP offers Airmen a well-defined career trajectory, instilling rigor in all facets of
career field training. As a talent management instrument, the CFETP ensures the
effective development and administration of Airmen required for high-end combat
scenarios. By promoting collaboration across the newly consolidated cyber career
fields, the CFETP encourages Airmen to hone their skills, adapt, and expedite change to
optimally serve the Air Force, Combatant Commanders, and our nation.
Note: Civilians occupying associated positions will use Part II to support duty
position qualification training.
2.
There are two parts of the Cyber Defense Operations CFETP. Part I describes the
overall Air Force Specialty (AFS) management and description of the career path. Part
II provides core tasks and reference materials.
2.1.
Part I provides information for the management of the specialty family. Section A:
explains how Cyber Defense Operations Airmen and their supervisors will use the plan;
Section B: identifies career field progression, duties, responsibilities, training strategies, and
career field paths; Section C: associates each level with specialty qualifications (knowledge,
education, experience, training, and other); Section D: indicates resource constraints (e.g.,
funds, manpower, equipment, facilities); and Section E: identifies transition training guide
requirements for SSgt through MSgt.
2.2.
Part II includes the following: Section A: identifies the Specialty Training Standards
(STS), the duties, tasks, and Training References (TRs) to support core task training such as
Air Education Training Command (AETC) training, wartime course and correspondence
course requirements; Section B: contains the Course Objectives List (COL) and training
standards supervisors will use to determine if Cyber Defense Operations Airmen have
satisfied training requirements; Section C: identifies support materials, e.g., Qualification
Training Package (QTP); Section D: identifies a training course index which includes both
mandatory and optional courses; and Section E: identifies MAJCOM-unique training
requirements supervisors can use to determine additional training required for the associated
qualification needs. At the unit level, supervisors and trainers will use Part II to identify,
plan, and conduct training commensurate with the overall mission goals.
3.
The CFETP is the overarching guide for the 1D7XX/X career field and provides the
foundation for effective and efficient training for Cyber Defense Operations Airmen in
each 1D7XX/X shred at the appropriate points in their careers. This plan enables the Air
Force to train today's work force for tomorrow's technology.
5
Abbreviations/Terms Explained
This section provides a common understanding of the terms that apply to the 1D7XX/X CFETP.
Air Education and Training Command (AETC). Major Command (MAJCOM) responsible for the
recruiting, training, and education of Air Force personnel. AETC also provides pre-commissioning,
professional military, and continuing education.
AETC Training Manager (TM). An instructional systems specialist who serves as the liaison between
the schoolhouse, training pipeline managers, training requirements quota managers, Numbered Air
Force, and MAJCOM training functions. Manages training resources and student production.
Air Force Career Field Manager (AFCFM). The career field manager is appointed by the functional
manager. Enlisted career field managers are E-9s. Focal point for the designated career field within a
functional community. Serves as the primary advocate for the career field, addressing issues and
coordinating functional concerns across various staffs. Responsible for the career field policy and
guidance (DAFMAN 36-2689, Training Program)
Air Force Enlisted Classification Directory (AFECD). The official directory for all military enlisted
classification descriptions, codes, and identifiers. Establishes the occupational structure of the Air Force
enlisted force. The occupational structure is flexible to permit enlisted personnel to specialize and
develop their skills and abilities while allowing the Air Force to meet changing mission requirements.
Individual enlisted personnel have a joint responsibility with commanders and supervisors at all levels
to fully develop their abilities consistent with Air Force needs and within the established patterns of
specialization.
Air Force Job Qualification Standard (AFJQS). A comprehensive task list that describes a particular
job type or duty position. Supervisors use the AFJQS to document task qualification. The tasks on
AFJQSs are common to all persons serving in the described duty position.
Air Force Manpower Analysis Agency (AFMAA). AFMAA is organized to support the Air Force,
MAJCOMs, and Commanders through the employment of management consultant services. AFMAA
provides specialized management engineering services for the proper determination of manpower
resources across the Air Force enterprise and the Department of Defense. Additionally, AFMAA
collaborates with the Under Secretary of the Air Force, Management (SAF/MG), to engage with Air
Force customers to promote the Air Force’s Continuous Process Improvement program and assist
commanders in achieving operational excellence.
Air Force Manpower Document (AFMD). AFMDs are a special publication type and provide the
missions for the Air Force’s major subdivisions who report directly to Headquarters Air Force (Major
Commands, Direct Reporting Units and Field Operating Agencies). Headquarters Air Force offices of
primary responsibility use these guidelines to develop AFMDs for each Major Command, Direct
Reporting Unit, and Field Operating Agency. The Vice Chief of Staff of the Air Force approves
AFMDs for Major Commands and Direct Reporting Units. The appropriate Headquarters Air Force
two-digit official (e.g., SAF/IG, AF/A3) approves AFMDs for their field operating agencies.
Air Force Qualification Training Package (AFQTP). An instructional course designed for use at the
unit to qualify or aid qualification in a duty position, program, or on a piece of equipment. It may be
printed, computer-based, or other audio-visual media.

6
Air Force Specialty (AFS). A group of positions (with the same title and code) that require common
qualifications.
Air University/Air Force Career Development Academy (AFCDA). An organization of Air Force
Institute for Advanced Distributed Learning (AFIADL); provides access to the Extension Course
Institute.
Career Field Education and Training Plan (CFETP). A comprehensive core training document that
identifies: life-cycle education and training requirements, training support resources, and minimum core
task requirements for a specialty. The CFETP aims to give personnel a clear path and instill a sense of
industry in career field training. CFETPs are officially posted at https://www.e-publishing.af.mil/
Certification. A formal indication of an individual’s ability to perform a task to required standards.
Certifying Official. A person assigned by the commander to determine an individual’s ability to
perform a task to required standards.
Chemical, Biological, Radiological, Nuclear, and High-Yield Explosive (CBRNE) Task
Qualification Training (TQT). CBRNE TQT ensures personnel maintain proficiency in performing
mission-critical tasks in a CBRNE environment. See AFI 10-2501, Air Force Emergency Management
(EM) Program Planning and Operations, and AFI 10-2607, Chemical, Biological, Radiological and
Nuclear Survivability for additional information/requirements. See Part II, Section A, Note 12 for
implementation guidance.
Cloud Computing. The use of computing resources (hardware and software) delivered as a service
over a network (typically the Internet).
Collaboration. Collaboration is the interaction among two or more individuals encompassing a variety
of behaviors, including communication, information sharing, coordination, cooperation, problem-
solving, and negotiation.
Collaborative Tools. Collaborative tools consist of various web-based technologies including advanced
white boarding, groupware, and facilitation. Collaborative capabilities assist significantly with
managing information throughout its life cycle and enable Air Force members to perform most office-
oriented and operational communication tasks from their desktops.
Command, Control, Communications, Computer, Intelligence, Surveillance, and Reconnaissance
(C4ISR). Integrated systems of doctrine, procedures, organizational structures, personnel, equipment,
facilities, and communications designed to support a commander’s exercise of command and control
through all phases of the operational continuum. C4 systems include base visual information support
systems.
Communications-Computer Systems (C-CS). The facilities, equipment, communications, procedures,
and personnel essential to a commander for planning, directing, and controlling operations of assigned
forces pursuant to the missions assigned.
Computer Based Training (CBT). A forum for training in which the student learns via a computer
terminal. It is an especially effective training tool that allows the students to practice applications while
they learn.
7
Content Management. A set of processes and technologies supporting the evolutionary life cycle of
digital information. This digital information is often referred to as content or, to be precise, digital
content. Digital content may take the form of text, such as documents; multimedia files, such as audio or
video files; or any other file type that follows a content life cycle that requires management.
Continuation Training. Advanced and qualification training that develops in-depth expertise within a
specialty, broadens knowledge to new specialties, introduces new technologies and systems, develops
analytical skills, or increases understanding of the relationship between cyber specialties.
Core Competency. An integrated bundle of expert knowledge and organizational skills inherent to a
particular career field(s) which makes a disproportionate contribution to the success of providing the
right skills needed for military operations, anywhere and anytime. It cannot be duplicated by any other
organization and is critical for the future.
Core Tasks. Tasks that AFCFMs identify as a minimum qualification requirement for everyone within
an AFSC, regardless of duty position. Core tasks may be specified for a particular skill level or in
general across the AFSC. Guidance for using core tasks can be found in the applicable CFETP narrative.
Course Objective List (COL). A publication derived from initial/advanced skills Course Training
Standard (CTS), identifying the tasks and knowledge requirements and respective standards provided to
achieve a 3-skill level in this career field. Supervisors use the COL to assist in conducting graduate
evaluations in accordance with DAFMAN 36-2689.
Course Resource Estimate (CRE). Well-developed, initial estimated costs associated with training.
Course Training Standard (CTS). A standard developed for all courses not governed by an STS,
including specialized training packages and computer-based training courses.
Critical Tasks. Critical Tasks are tasks requiring specific training and certification above and beyond
other tasks. Tasks may be defined as critical either through AFIs, Technical Orders, higher
headquarters, or at any level in the unit. A task when not accomplished to the specified standard results
in a serious adverse effect upon mission accomplishment, survivability or safety.
Cross Utilization Training. Provides units flexibility to train individuals to perform tasks not in their
Primary AFSC to offset low skill level manning and enhance combat capability.
Cyber Fundamentals (CF). The Initial Skill Training course, comprised of six instructional blocks,
covers a range of topics: network fundamentals, routing and switching, server appliances, client
systems, cyber security, and culminates in a capstone event. In Fiscal Year 2021, the Cyber
Fundamentals course was introduced as a replacement for the Information Technology Fundamentals
course.
Cyberspace. A global domain within the information environment consisting of the interdependent
network of information technology infrastructures, including the Internet, telecommunications
networks, computer systems, and embedded processors and controllers.
Cyberspace Operations (CO). The employment of cyber capabilities where the primary purpose is to
achieve objectives in or through cyberspace. Such operations include all applicable statuses, but
specifically offense and defensive cyber operations, and all actions taken to configure, secure, operate,
maintain, and sustain the Department of Defense Information Networks (DoDIN).

8
Data Management. The process of planning, coordinating, sharing, and controlling
organizations’ data resources (AFPD 33-3, Information Management).
Direct Reporting Unit (DRU). Air Force subdivisions directly subordinate to the CSAF.
A DRU performs a mission that does not fit into any of the MAJCOMs. A DRU has many
of the same administrative and organizational responsibilities as a MAJCOM (Example of
a DRU: USAF Academy).
Document Management. The process of managing documents through their life cycle, from inception
through creation, review, storage, dissemination, and archival or deletion. Document management can
also be a database system to organize stored documents, or a search mechanism to quickly find specific
documents. (AFPD 33-3)
DoD Cyber Workforce Framework (DCWF). DCWF is derived from the National
Initiative for Cybersecurity Education (NICE) Workforce Framework and Joint Cyberspace
Training & Certification Standards. It provides a mechanism to categorize, organize, and
describe cyber work and reflects collaborative efforts among government, private industry,
and academia. It establishes a standard lexicon of cyber work roles, classifies the duties and
skill requirements of Department cyber work force (military, civilian, and contractors), and
is the foundation for developing qualification requirements. More info can be found at the
following link: https://cyber.mil/cw/dcwf/
The DoD Directive 8140.01 “Cyberspace Workforce Management.” Reissues,
renumbers, and cancels DoD Directive (DoDD) 8570.01 to update and expand established
policies and assigned responsibilities for managing the DoD cyberspace workforce. The
DoD 8570.01-M governing the IA workforce certification program still in effect. It
authorizes establishment of a DoD Cyberspace Workforce Management Board (CWMB) as
the governing body to ensure that the requirements of this issuance are met. Establishes the
DoD Cyberspace Workforce Framework (DCWF) as the authoritative reference for the
identification, tracking, and reporting of DoD cyberspace positions and foundation for
developing enterprise baseline cyberspace workforce qualifications. Unifies the overall
cyberspace workforce and establishes specific workforce elements (e.g., information
technology (IT), cybersecurity, cyberspace effects, intelligence, and enablers) to align and
manage the cyberspace workforce under the CWMB. In light of the issuance of DoD
Directive 8140.01, there are ongoing changes to the qualification manuals for the cyber
workforce. More info can be found at the following link: https://public.cyber.mil/wid/
DoD 8570.01-M “Information Assurance Training, Certification, and Workforce
Management.” Provides guidance and procedures for the training, certification, and
management of the DoD Workforce conducting Information Assurance (IA) functions in
assigned duty positions.
DoD Information Network (DoDIN). The globally interconnected, end-to-end set of
information capabilities, associated processes, and personnel for collecting, processing,
storing, disseminating, and managing information on demand to warfighters, policy makers,
and support personnel. The DoDIN includes all owned and leased communications and
computing systems and services, software (including applications), data, security services,
and other associated services necessary to achieve Information Superiority. The DoDIN
supports all Department of Defense, National Security, and related Intelligence Community
missions and functions (strategic, operational, tactical, and business), in war and in peace.
The DoDIN provides capabilities from all operating locations (bases, posts, camps, stations,

9
facilities, mobile platforms, and deployed sites). The DoDIN provides interfaces to
coalition, allied, and non- DOD users and systems.
Duty Position Tasks. The tasks assigned to an individual for the position currently held.
These include, as a minimum, all core tasks that correspond to the duty position as directed
by the AFCFM or MFM, and tasks assigned by the supervisor. (DAFMAN 36-2689)
Education and Training Course Announcement (ETCA). ETCA contains specific
MAJCOM procedures, fund cite instructions, reporting instructions, and listings for those
formal courses the MAJCOMs or FOAs conduct or manage. ETCA also contains courses
the Air Force and reserve forces conduct or administer and serves as a reference for the Air
Force, DoD, other military services, government agencies, and security assistance
programs. Located at https://usaf.dps.mil/teams/app10-etca/SitePages/home.aspx
Education with Industry (EWI). The EWI Program is a highly selective, competitive,
career development program designed to improve the technical, professional, and
management competencies of participating students by partnering with top tier public and
private sector companies.
Enlisted Cyber Education Opportunities (ECEO). This program provides training to
further develop NCOs technical education and skills to enhance mission capability for
diverse career fields with positions requiring a higher degree of education. Courses can be
found on MyVector.
Enlisted Specialty Training (EST). A mix of formal training (technical school) and
informal training (on-the-job) to qualify and upgrade Airmen in each skill level of a
specialty.
Enlisted Talent Marketplace (eTM). A platform that streamlines the assignment process
for Total Force enlisted personnel by increasing transparency and providing more control for
Airmen and their supervisors. ETM matches Airmen with positions based on individual
preferences, qualifications, and the needs of the unit.
Enterprise. The entire range of communications/networking within garrison and tactical
realms to include voice, video, data, imagery, and sensor.
Enterprise Information Management (EIM). Encompasses a set of strategies for
organizational management of all aspects of enterprise data as information assets. The
proper models, data architecture, application architecture, and integration vision enables
using the “enterprise information asset” for strategic analysis, customer-centricity,
performance and productivity analytics, and personalization, eventually providing a means
for transitioning from an operational, line-of-business oriented application environment to
an intelligent, learning, and agile organization.
Enterprise Information System (EIS). A portfolio of services that bring about Enterprise
Information Management (EIM) capabilities.
Enterprise Information Technology. This includes all applicable statutes, specifically
related to the designing, building, and provisioning of IT systems within the
Department of the Air Force.
Exportable Training. Additional training via computer assisted, paper text, interactive
video, or other necessary means to supplement training.
Field Operating Agency (FOA). FOAs are subdivisions of the Air Force directly
10
subordinate to a headquarters US Air Force functional manager. An FOA performs field
activities beyond the scope of any of the MAJCOMs. The activities are specialized or
associated with an Air Force-wide mission (An example of a FOA is the Air Force Weather
Agency).
Functional Authority (FA). Designated General Officers and members of the Senior
Executive Service serving as Deputy Chiefs of Staff or Assistant Secretaries appointed
by the Secretary of the Air Force to provide oversight and functional advisory services
related to functional communities. Provide strategic oversight of force development to
include determination and prioritization of functional community requirements to meet
mission needs. (T-1). (DAFMAN 36-2689)
Field Training. Technical, operator, and other training that either a field training detachment
or field training team conducts at operational locations on specific systems and associated
direct- support equipment for maintenance and aircrew personnel.
Functional Area Manager (FAM). The individual accountable for the management and
oversight of all personnel and equipment within a specific functional area to support the
operational planning and execution. Responsibilities include, but are not limited to;
developing and reviewing policy; developing, managing, and maintaining Unit Type Codes
(UTC); developing criteria for and monitoring readiness reporting; force posturing; and
analysis. At each level of responsibility (Headquarters Air Force, MAJCOM, Air
Component, FOA, DRU, and Unit), the FAM should be the most knowledgeable and
experienced person within the functional area and have the widest range of visibility over
functional area readiness and capability issues.
Functional Manager (FM). RegAF general officer or senior executive service
members, designated by the appropriate functional authorities, who provide day-to-day
management over specific functional communities. While functional managers should
maintain an institutional focus with regard to resource development and distribution,
they are responsible for ensuring their specialties are equipped, developed, and sustained
to provide Air Force capabilities. (DAFMAN 36-2689)
Global Combat Support System - Air Force (GCSS-AF). An enterprise infrastructure
program established to develop, integrate, and deploy combat support information
capabilities. The mission of GCSS-AF is to provide timely, accurate, and trusted Agile
Combat Support (ACS) information to Joint and Air Force commanders, their staffs, and
ACS personnel at all ranks and echelons, with the appropriate level of security needed to
execute the Air Force mission throughout the spectrum of military operations. GCSS-AF is
the means by which ACS functional systems will be modernized and integrated to improve
business processes supported on a single robust network-centric infrastructure. In addition
to integrating combat support applications, GCSS-AF also provides core enterprise services
such as a common user presentation through the AF Portal, Enterprise Information
Management (Workflow, Records Management, Document Management, Knowledge
Management, and Collaboration), and an enterprise data warehouse.
Go/No-Go. The “Go” is the stage at which a trainee has gained enough skill, knowledge,
and experience to perform the tasks without supervision; meets the task standard. “No-Go”
is the stage at which the trainee has not gained enough skill, knowledge, and experience to
perform task without supervision; does not meet task standard.
High Performance Team (HPT). Consists of SMEs nominated by MFMs. They are
responsible for innovating force development requirements for Total Force Cyber Airmen.
11
The teams are charged with organizing, capturing, and creating viable learning resources
including traditional text material, distance learning courses, instructional videos, and
simulation programs. The HPTs also correlate to further the development of the Agile
Airman Model (AAM).
Individual Training Plan (ITP). Used in myTraining to document training. The ITP
reflects past and current qualifications and is used to determine training requirements. It
is intended to be a complete history of past training and current qualifications.
Supervisors will ensure all documentation is accurate and comprehensive.
Information Life Cycle. Typically characterized as creation or collection, processing,
dissemination, use, storage, protection, and disposition. (DoDD 8000.01, Management of
the Department of Defense Information Enterprise).
Information Management (IM). The planning, budgeting, manipulating, and controlling of
information throughout its life cycle. Joint Publication 3-0, Joint Operations, further defines
IM as the function of managing an organization’s information resources by the handling of
knowledge acquired by one or many different individuals and organizations in a way that
optimizes access by all who have a share in that knowledge or a right to that knowledge.
Information Systems (IS). Set of information resources organized for the collection,
storage, processing, maintenance, use, sharing, dissemination, disposition, display, or
transmission of information. (DoDI 8500.01, Cybersecurity)
Information Technology/National Security Systems (IT/NSS). Any equipment, or
interconnected system or subsystem of equipment, that is used in the automatic acquisition,
storage, manipulation, management, movement, control, display, switching, interchange,
transmission, or reception of data or information by the Executive Agency. This includes
equipment used by a DoD Component directly, or by use under contract with a DoD
Component, to the extent of such equipment is used in the performance of a service or
furnishing of a product. The term "IT" also includes computers, ancillary equipment,
software, firmware, and similar procedures, services (including support services), and related
resources. Notwithstanding the above, the term "IT" does not include any equipment acquired
by a federal contractor incidental to a federal contract. The term "IT" includes National
Security Systems (NSS).
Initial Qualification Training (IQT). IQT is training needed to qualify personnel for basic
duties in an assigned position for a specific Mission Defined Service, weapons system,
function or activity, with-out regard for a unit's specific mission. Qualification evaluations
consist of two structured phases, knowledge and task. The knowledge phase includes a series
of examinations and the task phase includes a hands-on evaluation of job performance.
Initial Skills Training (IST). A formal school’s course that results in an AFSC 3-skill
level award for enlisted or mandatory upgrade training to qualified officers. (DAFMAN
36-2689)
Instructional System Design (ISD). A deliberate and orderly (but flexible) process for
planning, developing, implementing, and managing instructional systems. It ensures
personnel are taught in a cost-efficient way to become educated on the knowledge, skills, and
abilities essential for successful job performance.

12
Integrated Maintenance Data System (IMDS). Is the standard Air Force system for
maintenance information. All maintenance information should be accessible for collection,
storage, and dissemination of critical data for repair and improvement of Air Force weapons
systems and equipment.
Knowledge. Information from multiple domains being synthesized, through inference or
deduction, into meaning or understanding not previously known. This includes: explicit
knowledge, which can be easily articulated, codified, and stored; and tacit knowledge,
which is based on personal experience, expertise, and judgment. Tacit knowledge is more
challenging to capture and share than explicit knowledge.
Knowledge Management (KM). Handling, directing, governing, or controlling of
natural knowledge processes within an organization in order to achieve the goals and
objectives of the organization.
Knowledge Operations (KO). Application and adaptation of Knowledge Management
(KM) into daily AF operations to enable information/decision superiority. KO leverages
the interaction of people, processes, and EIS technologies to capture, store, organize,
share, and control tacit and explicit knowledge, ensuring all mission execution processes
have access to relevant cross-functional information in a collaborative, timely, and
contextual manner.
Knowledge Training. Training used to provide a base of knowledge for task
performance. Learning gained through knowledge rather than hands-on experience. It
may also be used in lieu of task performance when the training capability does not exist.
(DAFMAN 36-2689)
Learning Program (LP). Learning Programs are developed to help support OJT and upgrade
training as part of the AFSC’s CFETP. LPs are published to provide the information
necessary to satisfy the career knowledge component of OJT. These programs/courses are
developed from references identified in the CFETP, by the Learning Program Manager
(LPM), and by the AFSC’s High Performance Team (HPT). LPs must contain informat i o n o n
basic principles, techniques, and procedures common to an AFSC. They do not contain
information on specific equipment or tasks unless best illustrating a procedure or technique
having utility to the entire AFSC. If available, supervisors will use LPs to satisfy career
knowledge requirements for UGT. When LPs are not available, trainees will study the
applicable technical references identified by the supervisor and/or CFETP. Also see High
Performance Team (HPT) and Learning Program Manager (LPM).
Learning Program Manager (LPM). Formerly known as CDC Writers, LPMs are
responsible for the development of their assigned AFSC shred Learning Programs (LPs).
They not only write and update Learning Programs, but also work directly with the
AFCFMs on several lines of effort to drive cyber workforce training into the next era.
They serve as the chairperson for their AFSC's High Performance Team (HPT) and use the
data gathered during STRTs, Training Planning Teams, and UT&Ws to modernize the
CFETP and associated AFJQS/AFQTPs.
Major Command (MAJCOM). A MAJCOM represents a major Air Force subdivision
having a specific portion of the Air Force mission. Each MAJCOM is directly subordinate
to HQ USAF. MAJCOMs are interrelated and complementary, providing offensive,
defensive, and support elements.
13
MAJCOM Functional Managers (MFM). Advises the MAJCOM directorates and staff
on 1D7XX/X utilization and training issues. Serves as the MAJCOM voting
representative during career field Utilization and Training Workshops. Assists in
gathering inputs and data to complete enlisted grade allocation for Career Progression
Group (CPG) reviews. Provides guidance to field units on 1D7XX/X personnel issues.
Assists with the dissemination of information regarding Air Force and career field
policies, plans, programs, and procedures to field units.
Master Task Listing (MTL). A comprehensive list (100%) of all tasks performed within
a work center and consisting of the current CFETP or AFJQS and locally developed AF
Forms 797 (as a minimum). Should include tasks required for deployment and/or UTC
requirements.
milSuite. The purpose of milSuite is to provide a collection of social business tools for
Department of Defense (DoD) personnel that facilitates professional networking,
learning, and innovation through knowledge sharing and collaboration.
Mission Qualification Training (MQT). MQT follows IQT and is training needed to
qualify personnel to perform their specific unit mission in an assigned position.
Completion of Specialty Training Standard task and knowledge training requirements
may be accomplished concurrently with MQT.
Mission Readiness Training (MRT). Is specialized training to ensure an organization's
ability to understand, plan, program, and fulfill core mission responsibilities, even and
especially in the face of emerging threats and other major changes in circumstance.
Occupational Analysis Report (OAR). A detailed report showing the results of an
occupational survey of tasks performed within a particular AFSC. This data is used
to provide personnel and training decision-makers with factual and objective job
information which enables them to justify and/or change personnel utilization
policies and programs, refine and maintain occupational structures, and establish,
validate, and adjust testing and training programs.
On-the-Job Training (OJT). Hands-on, over-the-shoulder training conducted to
certify personnel in both upgrade (skill level award) and job qualification (duty
position) training.
Personally Identifiable Information (PII). Information about an individual that
identifies, links, relates, or is unique to, or describes the individual, e.g.: SSN, age,
military rank, civilian grade, marital status, race, salary, home/office phone numbers, or
other demographic, biometric, personnel, medical, and financial information, etc.
Proficiency Training. Additional training, either in-residence or exportable advanced
training courses, or on-the-job training, provided to personnel to increase their skills and
knowledge beyond the minimum required for upgrade.
Qualification Training. Hands-on, task performance-based training designed to qualify
Airmen in a specific duty position. This training program occurs both during and after the
upgrade training process and is designed to provide skills training required to do the job.
Quality Assurance (QA). The Quality Assurance program ensures programs, functions,
process, equipment, systems, end item or service are of the type and quality to meet/or
exceed mission requirements. The QA program enhances mission accomplishment within
14
the confines of public law, DoD/AF policy and guidance or technical orders. QA
empowers commanders to actively manage mission risk at the appropriate level.
Quality Assurance Representative (QAR). A QAR is a member of the unit, not
permanently assigned to a QA program. QARs should be highly qualified persons
identified by skill and experience, motivation, and knowledge of evaluation, analysis, and
support duties. QARs are often used in small units or detachments where a full QA
program does not exist, or when mission needs dictate a smaller permanent QA presence
and still needs to complete inspections. When a military member is assigned as a QAR
they must possess a minimum 5-skill level (PAFSC).
Quality Training Flight (Q-Flight). As part of the 81st Training Support Squadron at
Keesler AFB, the primary mission of the Q-Flight is to develop on-the-job training tools
used by trainers to train and qualify Airmen in position specific duties. The flight
produces AFJQS’s, AFQTP’s, and handbooks for the following career fields: 1D7XX -
Cyber Defense Operations and 3FXXX - Personnel/Administration. Additionally, Q-
Flight assists with the development, standardization and publishing of all 1D7 Career
Field Education and Training Plans (CFETP).
Records Management. The planning, controlling, directing, organizing, training,
promoting, and other managerial activities involved in records creation, maintenance and
use, and disposition in order to achieve adequate and proper documentation of the policies
and transactions of the Federal Government and effective and economical management of
agency operations. (AFPD 33-3, Information Management)
Resource Constraints. Resource deficiencies (such as money, facilities, time, manpower,
and equipment) that preclude desired training from being delivered.
Senior Enlisted Leader (SEL). Senior Enlisted Leaders jobs are special positions awarded
to senior NCOs based on their grade, an installation’s needs and how well someone might
perform in the job. They take on management duties, mentorship and career counseling, and
other personnel and logistics issues within a unit. Some managerial duties and
responsibilities common to all SELs are: managing and directing personnel resource
activities, interpreting and enforcing policy and applicable directives, establishing control
procedures to meet work goals and standards, recommending or initiating actions to
improve functional operation efficiency, planning and programming work commitments and
schedules, and developing plans regarding facilities, supplies, and equipment procurement
and maintenance.
Service Oriented Architecture (SOA). A services-oriented architecture (SOA) environment
makes it easier and faster to build and deploy information capabilities that directly serve the
needs of the Air Force. SOA is an information technology environment where the following
occur: Mission and business processes are supported by information assets. Information
assets are delivered to consumers through content delivery services. Content delivery
services and other services interact to support process threads or to deliver information
assets. Core services, such as infrastructure and presentation services, are independent of the
content delivery services. Net-centric protocols and services allow federating and re-using
both content delivery and core services for multiple users, domains, and information sources.
Shred-outs (Shreds). Shreds are the alphabetical suffix that identifies specialization in a
specific career path. For example, 1D7X1P is the Data Operations shred-out of Cyber
15
Defense Operations.
Specialized Training Package (STP) and COMSEC Qualification Training Package
(QTP). A composite of lesson plans, test material, instructions, policy, doctrine, and
procedures necessary to conduct training. These packages are prepared by AETC, validated
by Cyberspace Capabilities Center (CCC), and administered by qualified communications
security (COMSEC) maintenance personnel.
Specialty Training Requirements Team (STRT). A meeting chaired by the AFCFM
with MAJCOM FMs, AETC Training Managers, Subject Matter Experts (SME) and HQ
AETC Occupational Analysis Division (OAD) in attendance. Typically held annually to
finalize any CFETP changes or enlisted classification directory descriptions.
Specialty Training Standard (STS). An Air Force publication describing an Air Force
specialty in terms of tasks and knowledge for Airman in a specialty may be expected to
perform or to know on the job. It also identifies the training provided to achieve a 3-, 5-, 7-,
or 9-skill level within an enlisted AFS. It further serves as a contract between AETC and the
functional user to show which of the overall training requirements for an Air Force Specialty
Code (AFSC) are taught in formal schools and correspondence courses.
Standard. An exact value, a physical entity, or an abstract concept established and defined
by authority, custom, or common consent to serve as a reference, model, or rule in measuring
quantities or qualities, establishing practices or procedures, or evaluating results. It is a fixed
quantity or quality.
Standardization and Evaluation (Stan Eval). The purpose of the Cybercrew Stan/Eval
program is to provide commanders a tool to validate readiness and the effectiveness of unit
operations, including documentation of individual member qualifications and certifications.
System Training Plan (STP). A living document explaining the training needed for a
system and how to obtain the training.
Task Module (TM). A group of tasks performed together within an AFS requiring common knowledge,
skills, and abilities. TMs are identified by an identification code and a statement.
Total Force. All collective components (active, reserve, guard, and civilian elements) of the
United States Air Force.
Training Capability. The ability of a unit or base to provide training. Authorities consider
the availability of equipment, qualified trainers, study reference materials, and other factors
in determining a unit's training capability.
Training Planning Team (TPT). Comprised of the same personnel as a STRT, TPTs are more
intimately involved in training development and the range of issues examined is greater than in the
STRT forum.
Training Requirements Analysis (TRA). A detailed analysis of tasks for a particular
AFSC to be included in the training decision process.
Training Setting. The type of forum in which training is provided (formal resident school,
on- the-job, field training, mobile training team, self-study, etc.).
Unit Type Code (UTC). A five-character alphanumeric code identifying a specific force
package of personnel and/or equipment. The UTC is the means for linking logistics and

16
manpower details within a unit type and is used to communicate force data. The UTC
represents a wartime capability designed to fill a valid contingency requirement.
Upgrade Training (UGT). Training that leads to the award of a higher skill level.
Utilization and Training Pattern. A depiction of the training provided to and the jobs
performed by personnel throughout their tenure within a career field or AFS. There are two
types of patterns: 1) Current pattern, which is based on the training provided to incumbents
and the jobs to which they have been and are assigned; and 2) Alternate pattern, which
considers proposed changes in manpower, personnel, and training policies.
Warfighter Communications. This includes all applicable statutes but specifically those
systems designed to be employed in austere, mobile, and/or expeditionary environments, to
provide command and control in support of Air or Space Force missions.
Wartime Tasks. Those tasks which must be taught when courses are accelerated in a
wartime environment. In response to a wartime scenario, these tasks will be taught in the 3-
level course in a streamlined training environment. These tasks are only for those career
fields still needing them applied to their schoolhouse tasks.
Workflow. A series of steps necessary for the initiation, tracking, and delivery of services
or outputs with the capability to cut across existing or future organizational boundaries.
Furthermore, web-based workflow products allow electronic coordination, staffing, and task
management of documents and files.
Section A - General Information
1.
Purpose. This CFETP provides the information necessary for AFCFM, MFMs,
commanders, training managers, supervisors and trainers to plan, develop, manage, and
conduct an effective and efficient career field training program. The plan outlines the Air
Force Specialty (AFS) training individuals should receive to develop and progress throughout
their career. This plan identifies AFSC requirements for Apprentice (3-skill level),
Journeyman (5-skill level) and Craftsman (7-skill level). Normally AETC conducts AFSC-
specific initial skills training upon an individual’s entry into the Air Force or upon retraining
into this specialty. After successful completion, the Airmen is awarded the Apprentice 3-skill
level. Upgrade training identifies the mandatory courses, task qualification requirements, and
correspondence course completion requirements for award of the 3-, 5-, 7-, 9-skill levels.
Qualification training is actual hands-on task performance training designed to qualify an
Airman in a specific duty position. This training occurs during and after the upgrade training
process. It is designed to provide the performance skills and knowledge required to do the job.
Advanced training is formal specialty training used for selected Airmen. Proficiency training
is additional training, either in-residence or exportable advanced training courses, or on-the-
job training provided to personnel to increase their skills and knowledge beyond the minimum
required for upgrade. The CFETP also:
1.1.
Serves as a management tool to plan, manage, conduct, and evaluate a career field-
training program. Also, it is used to help supervisors identify training at the appropriate
point in an individual’s career.
1.2.
Identifies task and knowledge training requirements for each AFS skill level and
recommends education and training throughout each phase of an individual’s career.
1.3.
Lists training courses available in the specialty, identifies sources of training, and the

17
training delivery method.
1.4.
Identifies major resource constraints that impact full implementation of the desired
career field training process
.
2.
Use of the CFETP. The plan is used by CFMs, MFMs, and supervisors at all levels to
ensure comprehensive and cohesive training programs are available for each individual in the
specialty.
2.1.
AETC training personnel develop or revise formal resident, nonresident, field and
exportable training based upon requirements established by the users and documented in
Part 2 of the career field education and training plan. They also work with the Lead
MAJCOMs in coordination with the AFCFMs to develop acquisition strategies for
obtaining resources needed to provide the identified training.
2.2.
MFMs ensure the CFETP mandatory requirements are incorporated as part of
MAJCOM-specific functional training programs. On-the-job Training, resident training,
and contract training or exportable courses can satisfy identified requirements. Ensure
Major Command-developed and resource training to support this AFSC is identified for
inclusion into the plan.
2.3.
81st TRSS/TSQ Qualification Training Flight (Q-Flight) personnel develop training
packages (AFJQSs/AFQTPs) based on requests submitted by the MAJCOMs and
according to the priorities assigned by the AFCFMs/MFMs.
2.4.
Cyber Defense Operations Airmen complete the mandatory training requirements
specified in this plan. The list of courses in Part 2 is used as a reference to support
training.
2.5.
MFMs submit recommended CFETP modifications to the 81st TRSS Q- Flight
Customer Service Desk at 81st TRSS/TSQS, 601 D Street, Keesler AFB MS 39534- 2235
or call DSN 597-3343 commercial 228-377-3343. To contact electronically send email to:
3.
Coordination and Approval of the CFETP. The AFCFM develops the CFETP, the
Functional Manager reviews and forwards the CFETP for Functional Authority approval.
The AFCFM will initiate an annual review of this document to ensure currency and
accuracy. MAJCOM representatives and AETC training personnel will identify and
coordinate on the career field training requirements. Using the list of courses in Part 2,
ensures elimination of duplicate training.
Section B - Career Field Progression and Information
4.
Specialty Descriptions. This information supplements the AFECD. AFSC specific
descriptions can be found in the AFECD. Duties and Responsibilities:
4.1.
Enterprise Operations delivers enduring cyber mission capabilities. Enterprise Operations
includes all applicable statutes, but specifically the designing, building, provisioning,
maintaining, and sustaining information systems, including warfighter communications, within

18
the Department of the Air Force (DAF). The Department of Defense Information Network
(DoDIN) operations mission includes operational actions taken to secure, configure, operate,
extend, maintain, and sustain DoD cyberspace and to create and preserve the confidentiality,
availability, and integrity of the DoDIN
4.2.
Mission Defense Activities conducts targeted defense of the DoDIN and other DoD
systems to execute DAF operations. Operations focus on identifying, locating, and defeating
specific threats that compromise the security of the communications, information,
electromagnetic environment, or industrial systems through defensive and protective measures
within a specified operational area. Operations in contested, degraded, and denied environments
to include but not limited to DoD networks, airborne platforms, austere environments,
AOC/JOCs (Air & Space Operations Center/Joint Operations Center), Weapons Systems, ICS
(Industrial Control Systems) & SCADA (Supervisory Control and Data Acquisition) systems,
and other interconnected devices that play a role in mission effectiveness
4.3.
Data Operations enables data driven decisions through delivering the employment of
information operations and software development methodologies. Operations modernizes and
enhances warfighter and weapon system/platform capabilities through the rapid design,
development, testing, delivery, and integration of reliable, secure mission-enabling systems.
Provides automated solutions for Commanders requiring real-time, data-driven decisions.
4.4.
Expeditionary Communications delivers cyber capabilities in austere and mobile
environments. Expeditionary Communications includes all applicable statutes, but specifically
datalinks, the building, operating, maintaining, securing, and sustaining of tactical and
communications networks when needed to support warfighter requirements, systems employed
in austere, mobile, and/or expeditionary environments, to provide command and control in
support of Air and Space Force missions.
5.
Skills and Career Progression. Adequate training is essential to timely progression of
personnel from 3-level to 9-level and plays an important role in the Air Force’s ability to
accomplish its mission. Everyone involved in training must do their part to plan, manage, and
conduct effective training programs. The guidance provided in this part of the CFETP and the
1D7XX/X Cyber Defense Operations Career Field Path table will ensure individuals receive
viable training at appropriate points in their careers. Mandatory requirements for upgrade training
to each skill level are covered in Section C.

19
6.
Training Decisions. This CFETP was developed to encapsulate an entire spectrum of
training requirements for the Cyber Defense Operations career field family using a building
block approach (simple to complex). Included in this spectrum is the strategy of when,
where, and how to meet the training requirements. The strategy must be clear and
affordable to reduce duplication of training and eliminate a disjointed approach to training.
6.1.
81st TRSS/TSQ (Q-Flight). Develops AFJQSs/AFQTPs to support tasks relating to Cyber
Defense Operations and Systems, functions, and duties. Completion of AFJQSs/AFQTPs is
mandatory by duty position for personnel in upgrade or qualification training.
6.2.
Learning Programs. Mandatory requirements for upgrade training to each skill level
are covered in Section C.
7.
Community College of the Air Force (CCAF) Academic Programs. Enrollment in CCAF
occurs upon completion of basic military training. CCAF provides the opportunity for all enlisted
members to obtain an Associate in Applied Science degree. In order to be awarded the degree, it
must be completed before the student separates from the Air Force, retires, or is commissioned as
an officer. Degree programs and requirements applicable to the 1D7XX/X career field family can
be found in the CCAF general catalog. In addition to its associate degree program, CCAF offers
the following:
7.1.
CCAF Instructor Certification (CIC) Program. The College offers the CCAF Instructor
Certification to instructors teaching full time in a CCAF affiliated school. The program is a
three-level program (CIC-I, CIC-II and CIC-III). Each level consists of increased or advanced
requirements and achievements. The program provides CCAF instructors a structured
professional development track. To obtain more information and program procedures, refer to
the CCAF Campus Affiliations Policies, Procedures and Guidelines (PPG).

20
7.2.
General Education Mobile (GEM) / Air University Associate-to-Baccalaureate
Cooperative (AU-ABC). The GEM program connects CCAF students with online general
education courses offered by regionally accredited colleges and universities. The AU-ABC
program connects CCAF graduates with online 4-year degree programs. The AU-ABC program
includes postsecondary schools with regional accreditation and national accreditation through the
Distance Education and Training Council.
7.3.
Air Force Credentialing Opportunities On-Line (COOL). The AF COOL program
provides a one-stop location for Airmen to explore credentials recognized by the civilian
community that can enhance current performance in their AF job. Credentialing has two
purposes. First, it continues to professionalize the enlisted force by providing up-to-date industry-
recognized credentials in an Airman’s AF job. Second, it provides a way for Airmen to prepare
for civilian life by ensuring that they are ready for work in the civilian sector. There are many
aspects to credentialing including certifications and licenses, and a variety of agencies provide
credentialing. Some are at the national level while others are state or industry driven. To obtain
more information, refer to the Air Force Virtual Education Center (AFVEC) AF COOL website.
8.
Career Field Path. The following summarizes career progression and personnel
allocations across the career ladder. When an Airman is awarded a 5-lvl, the SEL is
responsible for submitting an AF Form 2096 to update the Airman’s AFS shred to
match the billet they have been assigned and trained for. 1D7XX/X personnel
maintain their individual AFS shreds through the rank of MSgt. Upon promotion to
SMSgt, all 1D7XX/X AFSC shreds merge to become a 1D791. 1D791s compete for
the rank of CMSgt to become a 1D700.

21
1D7XX/X CYBER DEFENSE OPERATIONS CAREER PATH
Education and Training Requirements
Rank
Basic Military Training
Apprentice Technical School (3-Skill Level) Amn
Up
g
rade To Journe
y
man (5-Skill Level)
MANDATORY
-
No minimum required time-in-training Maximum time-in training is 24
months for AD, ANG, AFRC, & retrainees.
-
Completion of 1D7XX/X Learning Programs.
- (X) in the 1D7XX/X Learning Program task title indicates a
requirement
-
Completion of 1D7XX/X CFETP requirements for 5-Skill Level,
Identified by an X in the Core & Wartime Column and an identifier
in the 5-Skill Level proficiency Code column
-
Completion of applicable core AFJQSs/AFQTPs as identified in Part II,
Section C - Support Materials Supplement for specific duty position,
equipment, and systems at assigned location.
OPTIONAL
-
AETC Supplemental trainin
g
courses as determined b
y
MAJCOM.
A1C
SrA
Up
g
rade To Craftsman (7-Skill Level) SSgt
MANDATORY
-
Minimum rank of SSgt.
-
No minimum required time-in-training. Maximum time-in training is 24
months for AD, ANG, AFRC, & retrainees.
-
Completion of 1D7XX/X CFETP requirements for 7-Skill Level.
Identified by an X in the Core & Wartime Column and an identifier
in the 7-Skill Level proficiency Code column
-
Completion of 7-level Learning Program, if available.
- (X) in the 1D7XX/X Learning Program task title indicates a
requirement.
-
Completion of applicable core AFJQSs/AFQTPs as identified in Part II,
Section C - Support Materials Supplement for specific duty position,
equipment, and s
y
stems at assi
g
ne
d
location.
See
https://mypers.af.mil/
statistics for average
promotion sew- on
and DAFI 36-2502
for enlisted Airman
Promotion
/Demotion
Programs.
OPTIONAL
AETC Supplemental training courses as determined by MAJCOM.

22
1D7XX/X CYBER DEFENSE OPERATIONS CAREER PATH
Education and Training Requirements
Rank
Eligibility and Prerequisite Requirements for Enlisted Professional
Military Education (EPME i.e. ALS, NCOA, SNCOA) can be found at
myPers.
Airmen will be scheduled for resident EPME based on rank and time-in-
grade. Review the Resident EPME Eligibility Chart for additional guidance.
TSgt
MSgt
Up
g
rade To Superintendent (9-Skill Level)
MANDATORY
-
Minimum rank of SMSgt.
-
Completion of applicable core AFJQSs/AFQTPs as identified in Part II,
Section C - Support Materials Supplement for specific duty position,
equipment, and systems at assigned location.
SMSgt
Chief Enlisted Manager (CEM)
- CMSgt Leadership Course (CLC)
CMSgt
Note 1: See Part II, Sections C and D for a list of AFJQSs/AFQTPs and AETC supplemental
training.
Note 2: All core position tasks must be completed prior to upgrade. This includes all tasks outlined
in CFETP 1D7XX/X.

23
Section C - Skill Level Training Requirements
9.
Purpose. Skill level training requirements in this specialty are defined in terms of
tasks and knowledge requirements. This section outlines the specialty qualification
requirements for each skill level in broad, general terms and establishes the mandatory
requirements for entry, award, and retention of each skill level. The specific task and
knowledge training requirements are identified in the Specialty Training Standard at
Part 2, Section A and B of this CFETP.
10.
Specialty Qualification Requirements. This information supplements the AFECD.
AFSC-specific specialty qualifications can be found in the AFECD.
10.1.
Apprentice (3-Level) Training. The AFSC-specific Apprentice Course serves as the
initial skills course and must be completed to be awarded a 1D7XX/X AFSC.
KNOWLEDGE None required.
EDUCATION Completion of high school is mandatory.
TRAINING
Completion of the career field-specific Apprentice course. See Part II,
Section B for Course Objective List.
EXPERIENCE None required.
OTHER For award and retention of this AFSC, individual must maintain local
network access IAW AFI 17-130, Cybersecurity Program
Management and AFMAN 17-1301, Computer Security
(COMPUSEC).
Eligibility for a security clearance according DoD Manual
5200.02_AFMAN 16-1405, Air Force Personnel Security
Pro
g
ram, is mandator
y
for awar
d
an
d
retention of this skill level.
IMPLEMENTATION Attendance at the career field-specific Apprentice course is
mandatory for award of the 3-skill level unless waived by the
1D7 AFCFM.

24
10.2.
Journeyman (5-Level) Training.
KNOWLEDGE
Completion of the 1D7 Initial Skills Training Course and 1D75X
5-Level Learning Pr
ograms.
TRAINING
No mandatory AETC training courses are required for upgrade.
EXPERIENCE
Qualification in
and possession of AFSC 1D7XX/X.
Experience performing functions specific to your career field.
Completion of all 1D7XX/X STS core tasks.
Completion of applicable AFJQSs/AFQTPs.
Completion of all local tasks assigned for the duty position.
OTHER For award and retention of this AFSC, individual must maintain local
network access IAW AFI 17-130, Cybersecurity Program
Management and AFMAN 17-1301, Computer Security
(COMPUSEC).
IMPLEMENTATION Entry into formal journeyman upgrade training is accomplished once
individuals are assigned to their first duty station. Qualification
training is initiated any time individuals are assigned duties for
which they are not qualified. Use LPs, CBTs and AFJQSs/AFQTPs
concurrently to obtain the necessary qualification for refresher and
cross-utilization training.
10.3.
Craftsman (7-Level) Training.
KNOWLEDGE All 1D75X knowledge qualifications apply to the 1D77X
requirements. Completion of 1D7XX/X 7-level Learning
Program, if available.
TRAINING
C
ompletion of applicable AFJQSs/AFQTPs.
EXPERIENCE Qualification in and possession of AFSC 1D75X.
Experience performing or supervising one of the functions of
1D7XX/X. Completion of all STS core tasks.
Completion of all local tasks assigned for the duty position.
OTHER For award and retention of this AFSC, individual must maintain local
network access IAW AFI 17-130, Cybersecurity Program
Management and 17-1301, Computer Security (COMPUSEC).
IMPLEMENTATION Entry into OJT is initiated when individuals obtain the necessary rank
and skill level. Qualification training is initiated any time an
individual is assigned duties for which they are not qualified. Use the
Learning Program and AFJQSs/AFQTPs concurrently to obtain the
necessary qualification for refresher and cross-utilization training.

25
10.4.
Superintendent (9-Level) Training. Upgrade training consists of: (1) Qualification
Training is required prior to upgrade to 9-level for SMSgts and CMSgts. Wear the badge as
prescribed by AFI 36-2903, Dress and Personal Appearance of Air Force Personnel paras
9.1 and 9.1.3.
KNOWLEDGE
Mandatory: Techniques and Procedures of Systems Analysis and
Design; Project Management, Communications-Computer
Processing; System Operation and Maintenance; System and
Equipment Capability, Capacity, and Logic; Personnel and
Equipment Performance Measurement; Awards Programs and
Manpower and Organization; Security, Administrative Contract,
Training, Resource, Records, Publications, Deployment, Logistics,
and Base/Unit Functional Management.
EXPERIENCE
Qualification in and possession of AFSC 1D77X is
mandatory.
Directing functions such as installing, maintaining, operating,
repairing, or modifying the various cyberspace systems, software
development, cyber security, or resource management as related to
the feeder specialties.
OTHER
For award and retention of this AFSC, individual must maintain local
network access IAW AFI 17-130, Cybersecurity Program
Management and AFMAN 17-1301, Computer Security
(COMPUSEC).
IMPLEMENTATION Entry into OJT is initiated when individuals are selected for the rank
of SMSgt. Qualification training is initiated any time individuals are
assigned duties for which they are not qualified.
10.5.
Training Sources.
10.5.1.
Career field-specific and 1D7XX/X Learning Programs are available via Percipio.
A complete description and listing of LPs offered by AFCDA is available via
Air University.
10.5.2.
AFJQSs/AFQTPs are Air Force publications and are mandatory for use by personnel in
upgrade or qualification training. They are developed by the 81st TRSS/TSQ (Q-Flight),
Keesler AFB, MS and may be downloaded from the Q-Flight SharePoint site. Procedures for
requesting development of AFJQSs/AFQTPs are contained in AFMAN 17-204, Air Force On-
the- Job Training Products for Cyber Defense Operations Enlisted Specialty Training.
26
11.
Occupational Badges. The Cyber Defense Operations badge has the same eligibility
criteria as other occupational badges. Enlisted Cyber Defense Operations personnel may wear
the basic badge after finishing technical school. Enlisted Cyber Defense Operations personnel
earn the right to wear the senior badge after being awarded the 7-skill level. Master badges
are awarded to Cyber Defense Operations Master Sergeants who have at least five years of
experience in the specialty at the 7-skill level or higher. Chief Master Sergeants who have
cross-flowed into the career field earn the basic badge when they are awarded the CEM code,
moving up to the senior badge after a year of service and to the master level after five years.
Section D - Resource Constraints
12.
Purpose. This section identifies known resource constraints that preclude optimal and
desired training from being developed or conducted, including information such as cost and
manpower. Narrative explanations of each resource constraint and an impact statement
describing what effect each constraint has on training are included. Also included in this
section are actions required, OPR and target completion dates. Resource constraints will be,
at a minimum, reviewed and updated annually.
Apprentice (3-Level) Training. The 1D7XX/X STSs may contain two proficiency codes
in the 3-level course column to indicate the desired level of instruction versus the actual
level of instruction due to resource constraints. Example: 2b / 1a. A STS waiver may be
issued for the STS elements not taught to the desired proficiency code.
Section E - Transition Training Guide
There are currently no transition training requirements. This area is reserved.

27
PART II
Section A - Specialty Training Standards
1.
Implementation. AFSC-Specific STSs are located in the Attachments Section of this
CFETP. See AFSC-specific STS for 3-Level course start date.
2.
Purpose. As prescribed in DAFMAN 36-2689, this CFETP:
2.1.
Lists in column 1 (Task, Knowledge, and Technical Reference) the most common tasks,
knowledge, and technical references (TR) necessary for Airmen to perform duties in the 3-, 5-,
and 7-skill level. Column 2 (Core Tasks) identifies, by 5, or 7, specialty-wide training
requirements. Note: Core tasks are minimum task training requirements for upgrade to the 5-
skill level.
2.2.
Provides certification for OJT. Column 3 is used to record completion of tasks and
knowledge training requirements. Use automated training management systems to document
technician qualifications, if available. For initial certification or transcribing documentation
complete the columns in accordance with DAFMAN 36-2689.
2.3.
Shows, in column 4, formal training and correspondence course requirements by listing the
proficiency to be demonstrated on the job by the graduate as a result of training on the task and
the career knowledge provided by the corresponding course. Learning Programs are available
via Percipio.
2.4.
Qualitative Requirements. Attachment 1 contains the tasks, knowledge and proficiency
levels referenced in paragraph 2. Columns are marked with a proficiency code to indicate
subjects taught. An X in the proficiency code column indicates a lack of student man-years and
instructor resources. Trainees without prerequisites specified in Education and Training Course
Announcement (ETCA) cannot be expected to meet proficiency levels indicated.
2.5.
Becomes a job qualification standard (JQS) for on-the-job training when placed in AF
Form 623, Individual Training Record folder, and used according to DAFMAN 36-2689.
2.6.
Is a guide for development of promotion tests used in the Weighted Airman
Promotion System. Specialty Knowledge Tests are developed at the AETC Airman
Advancement Division, by senior Noncommissioned Officers with extensive practical
experience in their career fields. Specialty Knowledge Tests are developed by subject
matter experts who authenticate Weighted Airman Promotion System material and
reference AF Specialty-specific occupational analysis data. Questions are based upon
study references listed in the Enlisted Promotions References and Requirements
Catalog. Individual responsibilities are in Chapter 4, paragraph 4.2.15 of DAFMAN
36- 2664, Personnel Assessment Program. Weighted Airman Promotion System is not
applicable to the ANG or ARC.
3.
Recommendations. Comments and recommendations are invited concerning the quality of
AETC training. A Customer Service Information Line (CSIL) has been installed for the
supervisors’ convenience. For a quick response to concerns, call our CSIL at DSN 312-597-
5250, 228-377-5250, or e-mail us at [email protected]. Reference this STS
and identify the specific area of concern (paragraph, training standard element, etc.).

28
BY ORDER OF THE SECRETARY OF THE AIR FORCE
OFFICIAL LEAH G. LAUDERBACK, Lt Gen, USAF
DCS for Intelligence, Surveillance, Reconnaissance
and Cyber Effects Operations
Attachments:
1. Qualitative Requirements
2. Specialty Training Standard (STS) 1D7XX
3. Specialty Training Standard (STS) 1D7X1P
4. Specialty Training Standard (STS) 1D7X1Q
5. Specialty Training Standard (STS) 1D7X1M
6. Specialty Training Standard (STS) 1D7X1W
7. Specialty Training Standard (STS) 1D7XX/X Legacy

29
PREFACE
Note 1: Users are responsible for annotating technical references to identify current
references pending STS revision. Locate current Air Force publications at:
DOD Issuances and OSD Administrative Instructions https://www.esd.whs.mil/dd/
Air Force Publications https://www.e-publishing.af.mil/
Air Force Communications Security (COMSEC)
Collaborative Environment (CE)
https://usaf.dps.mil/teams/13312/default.aspx
Air Force Information Assurance Collaborative
Environment (IACE)
https://usaf.dps.mil/teams/IACE/default.aspx
DISA Circulars and Instructions https://www.disa.mil/About/DISA-Issuances
Technical Orders (TO) https://www.my.af.mil/etims/ETIMS/index.jsp
Percipio https://usaf.percipio.com/
Note 2: Knowledge and/or performance tasks are defined in the AFJQS. AFJQS items set
the standard for qualification and certification and are mandatory for use in conjunction
with this STS when applicable to the duty position.
Note 3: All objectives are trained during wartime.
Note 4: Track and manage training for TSgts and below and MSgt/SMSgt retrainees
using an automated training system (e.g., myTraining).
Note 5: When an AFJQS is loaded into an automated training system, AFJQS task
numbering will vary from the STS. The numbering scheme is defined by your work
center specific training plan.
Note 6: Third person certification is not required for Cyber Defense Operations Specialist
personnel. However, members (to include civilians and contractors) assigned to crew
positions are still required position certification in accordance with Stan/Eval procedures.
Note 7: In the event of data network or computer system failure, courses are authorized
to use alternative methods of instruction to fulfill this STS element.
Note 8: Unless otherwise stated in the objective, the student may be allowed two assists
from the instructor and still successfully achieve the proper level of proficiency. An
instructor assist is defined as anytime an instructor must intervene to provide guidance to a
student which leads to a satisfactory completion of the objective or to prevent a student from
continuing in a manner which will lead to an unsatisfactory conclusion, safety violation, or
damage to the equipment. Successful students have performed the task to the satisfaction of
the course; however, they may not be capable of meeting the field requirements for speed or
accuracy.
Note 9: All equipment related objectives are performed by following procedures from
technical orders, technical manuals, or student instructional material developed by the
training facility.

30
Note 10: Senior NCOs in the 1D7XX/X AFSCs are not required to have an Individual
Training Plan (ITP) with the following exceptions: personnel in upgrade training status or
performing equipment maintenance as part of primary duties. Unit Commanders can require
Senior NCOs with UTC tasks to have an ITP.
Note 11: The 1D7XX/X STS consists of tasks that are applicable to all 1D7XX/X AFSCs.
This STS will be used as core requirement for 1D75X/X along with a member’s respective
shred STS. The 1D7X1 STS consists of tasks which are shared by shreds. 1D7X2F and
1D7X3C will only adhere to the requirements outlined in the trainee’s AFSC-specific STS.
Note 12: Certification of CBRN Task Qualification Training (TQT) requirements is outlined
in DAFMAN 36-2689 and AFI 10-2501. Any core 5 and 7 level tasks are appropriate for
evaluation under TQT; supervisors must tailor task selection based on the Airman’s assigned
UTC, MAJCOM-specific or locally directed requirements. Work centers will identify
additional TQT tasks as required.
Note 13: Security+ tasks will be taught IAW CompTIA Security+ Certification CTS.
Note 14: Attachment 7 is retained to include 3-lvl core tasks from 1D7 shreds that existed prior to the
new Mission-Capable force design. The column that denotes an XA, XB, XC, etc.. outlines the core
task and shred this is a core 3-lvl task for.
Section B - Course Objective List
4.
There is currently no advanced course. This area is reserved.
Section C - Support Materials
5.
The following list of support materials is not all-inclusive; however, it covers the most
frequently referenced areas. The most current products can be found at the 81 TRSS/TSQ web
page, and are available for download from the web site at
https://usaf.dps.mil/teams/10445/default.aspx, https://lms-jets.cce.af.mil/moodle/, and
https://www.youtube.com/channel/UCp7lrge1aHDA6wnEaXrdm5Q. Procedures for requesting
product development are found in AFMAN 17-204.
6.
Generic AFJQSs/AFQTPs applicable to AFSC 1D7XX/X family is available
at
https://usaf.dps.mil/teams/10445/default.aspx?RootFolder=%2Fteams%2F10445
%2FDocuments%2FCFETP%2F1D7XX%20%2D%20CYBER%20DEFENSE%
20OPERATIONS&FolderCTID=0x010100A06BF221F643144E807354644DE7
FCF3&View=%7B215A7876%2D5A74%2D4A5C%2DA4F0%2D1FCE911765
A1%7D
Section D - Training Course Index
7.
Purpose. This section of the CFETP identifies training courses available for continuation/
supplemental training. For information on all formal courses, refer to the Air Force Education
and Training Course Announcements (ETCA) database, at https://usaf.dps.mil/teams/app10-

31
etca/SitePages/home.aspx or the Cyberspace Capabilities Center (CCC) SharePoint page at
https://usaf.dps.mil/teams/ccc/SitePages/Home.aspx
8.
Air Force In-Residence Courses. The following list of formal courses is not all-inclusive;
however, it covers courses applicable to the 1D7XX/X family. The most current list can be
found at the 81 TRSS/TSQ web page at
https://usaf.dps.mil/teams/10445/default.aspx?RootFolder=%2Fteams%2F10445%2FDocumen
ts%2FCFETP%2F1D7XX%20%2D%20CYBER%20DEFENSE%20OPERATIONS&FolderC
TID=0x010100A06BF221F643144E807354644DE7FCF3&View=%7B215A7876%2D5A74
%2D4A5C%2DA4F0%2D1FCE911765A1%7D or the Cyberspace Capabilities Center (CCC)
SharePoint page at https://usaf.dps.mil/teams/ccc/SitePages/Home.aspx
9.
Air University Courses.
For a current listing of Air University courses go to https://www.airuniversity.af.mil/Barnes/
Section E - MAJCOM Unique Requirements
10.
MAJCOM unique requirements will be identified and listed on a
secondary document located on Q-Flight’s SharePoint page at
https://usaf.dps.mil/teams/10445/default.aspx?RootFolder=%2Fteams%2F104
45%2FDocuments%2FCFETP%2F1D7XX%20%2D%20CYBER%20DEFE
NSE%20OPERATIONS&FolderCTID=0x010100A06BF221F643144E80735
4644DE7FCF3&View=%7B215A7876%2D5A74%2D4A5C%2DA4F0%2D
1FCE911765A1%7D

1
Attachment 1
Qualitative Requirements
THIS BLOCK IS FOR IDENTIFICATION PURPOSES ONLY
Personal Data - Privacy Act of 1974
PRINTED NAME OF TRAINEE (Last, First, Middle Initial) INITIALS (Written) EDIPI
PRINTED NAME OF TRAINER AND CERTIFYING OFFICIAL AND WRITTEN INITIALS
N/I N/I
N/I N/I
N/I N/I
N/I N/I
N/I N/I
N/I N/I

2
Attachment 1
Qualitative Requirements
PROFICIENCY CODE KEY
SCALE
V
ALUE
DEFINITION: The individual
Task
Performa
nce
levels
1
Can do simple parts of the task. Needs to be told or shown how to do most of the task. (EXTREMELY LIMITED)
2
Can do most parts of the task. Needs help only on hardest parts. (PARTIALLY PROFICIENT)
3
Can do all parts of the task. Needs only a spot check of completed work. (COMPETENT)
4
Can do the complete task quickly and accurately. Can tell or show others how to do the task. (HIGHLY PROFICIENT)
*Task
Knowled
ge
levels
a
Can name parts, tools, and simple facts about the task. (NOMENCLATURE)
b
Can determine step by step procedures for doing the task. (PROCEDURES)
c
Can identify why and when the task must be done and why each step is needed. (OPERATING PRINCIPLES)
d
Can predict, isolate, and resolve problems about the task. (ADVANCED THEORY)
**Subje
ct
Knowled
A
Can identify basic facts and terms about the subject. (FACTS)
B
Can identify relationship of basic facts and state general principles about the subject. (PRINCIPLES)
C
Can analyze facts and principles and draw conclusions about the subject. (ANALYSIS)
D
Can evaluate conditions and make proper decisions about the subject. (EVALUATION)
Explanations
*
A task knowledge scale value may be used alone or with a task per
formance scale value to define a level of knowledge for a
specific ta
sk. (Example: b and 1b)
** A subject knowledge scale value is used alone to define a level of knowledge for a subject not directly related to any specific task, or
for a subject common to several tasks. This mark is used alone instead of a scale value to show that no proficiency training is
provided in the course or Learning Program.
(-) This mark is used alone in the Proficiency Codes Course columns to show no proficiency training is provided in the
applicable course. Training is satisfied through OJT, CBTs, Learning Programs, or a combination.
(X) This mark is used alone in the
Proficiency Codes Course columns to show training is required but not given due to limitatio
ns
in
resources or is a future requirement. Training is satisfied through OJT, CBTs, Learning Programs, or a combination.
NOTE: All tasks and knowledge items shown with a proficiency code are trained during wartime.
(X) When this code is used in the Core & Wartime
Tasks Column it indicates the CFM has mandated this task as a core requirement to
the
level identified in
the Task Knowledge Levels Column. The training to satisfy this requirement is either provided through OJT, CB
Ts,
Learning Pro
grams, or a combination.
(*) When this code is used in the Core & Wartime Tasks Column it indicates the CFM has mandated this task as a
wartime/deployment requirement.
(^) When this code is used in the Core & Wartime Tasks Column it indicates the CFM has mandated this task require(s) third person
certification.
CFETP versus AFJQS task coding. AFJQSs/AFQTPs annotated in the CFETP with a skill
level denotes the AFJQS is mandatory.

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1.1.1. Participate in Airmen
Vectoring Process
2b---
1.2.1. Cyber Operations Roles and
Responsibilities
5/7/9 AAAC
1.2.2. Concepts of FMA / OCO /
DCO / DoDIN Ops
5/7/9 AAAC
1.2.3. Qualifications
5/7 -AA-
1.2.4. Progression within AFSC
5/7 -AB-
1.2.5. Read CFETP 1D7XX, Part I
5/7 -AA-
1.3. Cyber Policy, Doctrine, and
Guidance
--BD
1.4.1. Weapons System
Designation
-ABC
1.4.2. Weapons System
Requirements
-ABC
1.4.3. Air Force Cyber Weapons
Systems
AABC
1.4.4. Roles of Cyber Weapons
Systems
AABD
1.4.5. Weapons System Authorities
-ABC
2.1. Publications
5/7 AAB -
2.2. Technical Orders (TO)
5/7 AAA -
2.3. Locate Applicable Publications
5/7 -2b2b-
2.4. Use Publications / Technical
Orders When Performing Work
5/7 2b b b -
3.1. Joint mission planning process
AB - -
3.2. ME3C-(PC)2 / SMEAC
AA - -
3.3. Plan Brief Execute Debrief
AB - -
3. JOINT MISSION PLANNING
TR: 1D7X1M Learning Program (Percipio)
1. CYBER DEFENSE OPERATIONS
TR: 1D7XX Learning Program (Percipio); AFMAN 36-2100; AFPD 172; 1D7XX CFETP; AFECD; JPs 3-12, 3-13, 3-13.1, and 3-13.2
1.1. Airmen Vectoring
1.2. Introduction to Cyber
1.4. Weapons Systems
2. PUBLICATIONS AND DIRECTIVES
TR: 1D7XX Learning Program (Percipio), AFI 33-360, TO 00-5-1, https://dtic.mil
1. Implementation. This STS will be used for technical training provided by AETC for the 3-level course.
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
1D7XX STS
1
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
3.4. Perform Plan Brief Execute
Debrief
2b 2b - -
3.4.1. Military Planning Process
AAB -
4.1. Anti-Piracy
AA - -
4.2. Ethics
AABD
4.3. US Codes
-ABC
4.4. US Telecommunications Laws
--AB
4.5. International Laws Affecting
Electronic Communications
--AB
4.6. LOAC Considerations When
Planning / Conducting Cyber
Operations
--AB
4.7. Rules of Engagement (ROE)
5/7/9 ABBB
4.8. Cyber Tasking Order (CTO)
5/7/9 -ABC
5.1. Structure
- ABB
5.2. Missions
-A- -
5.3. Offensive Cyberwarfare
Operations
-ABC
5.4. Defensive Cyberwarfare
Operations
-ABC
5.5. Exploitation
-AA-
5.6. Effects on Adversary Decision
Makers
5/7/9 -BBC
5.7.1. Joint, DOD, and Combined
Units
5/7 -AB-
5.7.2. Air Force Units
5/7 -AB-
5.7.3. Air Force Network Operations
(AFNetOps)
5/7 -BB-
5.7.4. Cyber Organizations(JCSE,
WHCA, DISA, etc.)
AAB -
4. CYBER AUTHORITY AND USER RESPONSIBILITIES
TR: 1D7XX Learning Program (Percipio); AFDP 3-13 https://www.doctrine.af.mil/Doctrine-Annexes/Annex-3-13-Information-Ops/; JP 3-13; USC Titles 10, 18, 50;
http://iase.disa.mil/eta/Pages/index.aspx
5. CYBER ENCLAVE
TR: 1D7XX Learning Program (Percipio), AFPD 17-2, AFI 17-201, JP 3-12, http://www.afcyber.af.mil
5.7. Units
6. ENTERPRISE SYSTEMS / PROGRAMS
TR: 1D7XX Learning Program (Percipio); AFI 13-Series; Joint Pub 6-0; CJCSIs 3231.01C, 6211.02D
1D7XX STS
2
Atch 2
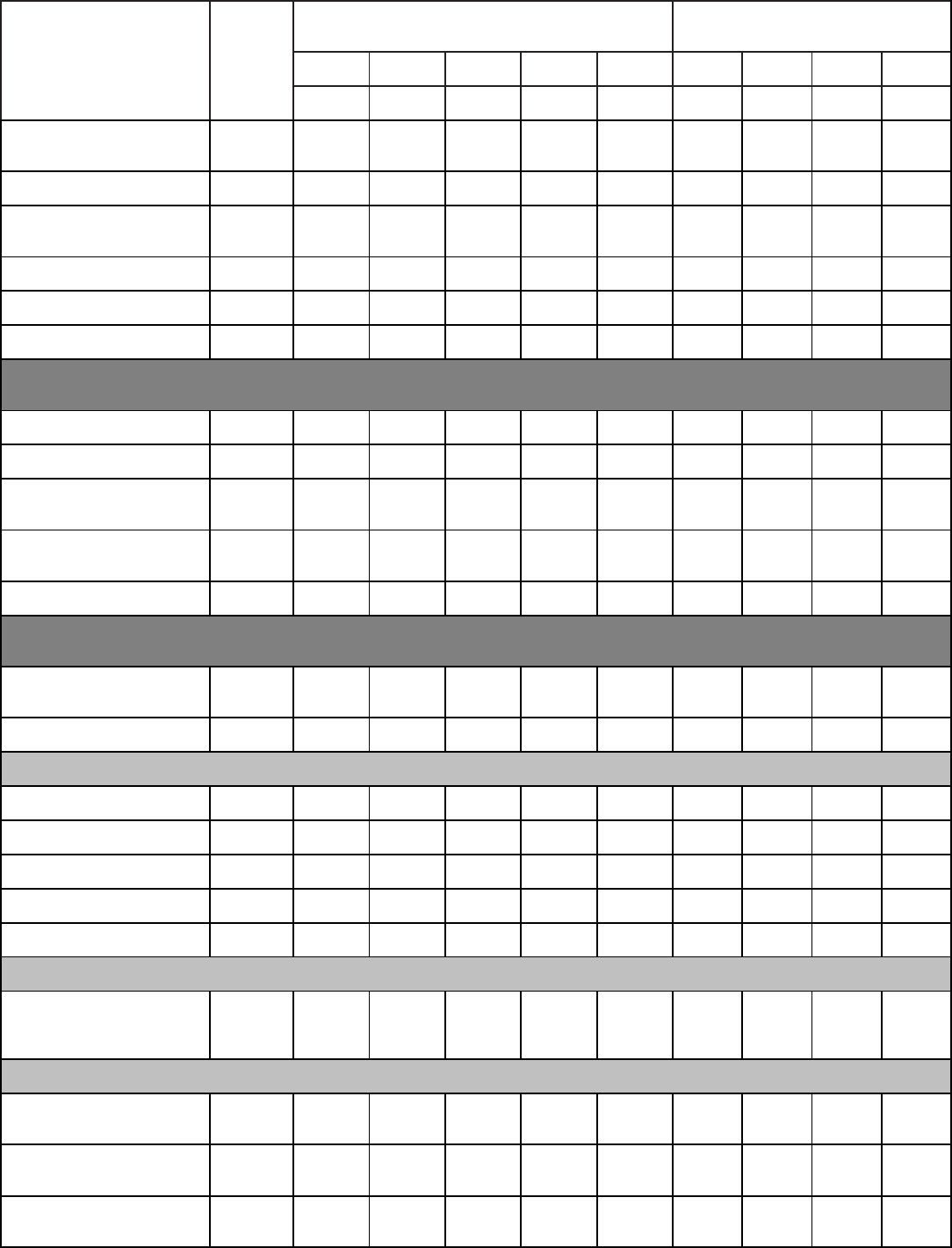
ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
6.1. Define Non-Secure Networks
5 AA - -
6.2. Define Secure Networks
5 AA - -
6.3. Nuclear Command, Control,
and Communications Systems
5 -A- -
6.4. Space Systems
5 -A- -
6.5. Airborne Networks
5/7 -AA-
6.6. Battlefield Networks
5/7 -AA-
7.1. Safety
5 -B- -
7.2. RM
5/7 -AB-
7.3. Work Center Safety Program
Management
5/7 -AA-
7.4. Characteristics of Personal and
Equipment Protection
5 -A- -
7.5. Practice Safety Precautions
2b---
8.1. Risk, Threats, and
Vulnerabilities
5/7/9 AABC
8.2. Network Security
5/7 BAB -
8.3.1. Concepts
5 AA - -
8.3.2. Configure
----
8.3.3. Troubleshoot
----
8.4. Security Zones
-A- -
8.5. Incident Response
5 AA - -
8.6.1. Acceptable Use / Behavior for
Information Technology
5 AA - -
8.7.1. Fundamentals of IT
Documentation
BB - -
8.7.2. Information Protection (IP)
Operations
5 -A- -
8.7.3. Operations Security (OPSEC)
7 A-A-
7. SAFETY / RISK MANAGEMENT (RM)
TR: 1D7XX Learning Program (Percipio); AFIs 32-1065, 90-802, 91-202; AFMAN 91-203; AFPAM 90-803; AFPD 91-2; MIL-STD 188-124B
8. CYBER SECURITY
TR: 1D7XX Learning Program (Percipio); AFIs 10-701, 17-130, 16-1404; AFPD 10-7; AFMAN 17-1301
8.3. Firewalls
8.6. Cyber Hygiene
8.7. Security Programs
1D7XX STS
3
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
8.7.4. Information Security
(INFOSEC)
A---
8.7.5. Information Access Programs
A---
8.7.6. Controlled Unclassified
Information (CUI)
A---
8.7.7. Information Assurance (IA)
A---
8.7.8. Computer Security
(COMPUSEC)
A---
8.7.9. TEMPEST Program
5 AA - -
8.7.10. TEMPEST Suppression
Techniques
-B- -
8.7.11. Negligent Discharge of
Classified Information (NDCI)
5 AB - -
8.7.12. Communications Security
(COMSEC)
5 AA - -
8.7.13. Confidentiality, Integrity, and
Availability (CIA)
5 AB - -
8.7.14. Classified Material Control
A---
8.7.15. Authentication,
Authorization, and Accounting
(AAA)
5 AB - -
8.8. Physical Security
A---
8.9.1. STIG Fundamentals
A---
8.9.2. STIG Principles
A---
8.9.3. Use STIG Viewer
2b---
8.9.4. Apply STIGs
2b---
9.1. IP Addressing Concepts
5 AB - -
9.2. OSI / TCP / IP Models
5/7 BBB
9.3. Network Devices
5/7 AAA -
9.4. Communications Mediums
5/7 AAA -
9.5. LAN Architecture
5/7 AAA -
9.6. Ports, Protocols, and Services
(PPS)
5/7 BBB -
9.7. Apply IP Address
2b---
9.8. Network Types
5/7 ABB -
8.9. Security Technical Implementation Guides (STIGs)
9. NETWORK FUNDAMENTALS
TR: 1D7XX Learning Program (Percipio)
1D7XX STS
4
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
9.9. Networks Layers
5 AA - -
9.10. Subnetting
A---
9.11.1. Application
BC - -
9.11.2. Configure
2b b - -
9.12.1. Topologies Fundamentals
5/7 ABB -
9.12.2. Develop Logical Diagram
2b---
9.12.3. Develop Physical Diagram
2b---
9.12.4. Develop Data Flow Diagram
2b---
9.13. Network Monitoring
5 AB - -
9.14. Wireless Networking (WLAN)
5/7 BBB -
9.15. Backup and Restore Device
Documentation
5 AA - -
9.16. Troubleshooting Methodology
5 BB - -
9.17.1. Cable Types and Handling
5 BB - -
9.17.2. Test Cable
2b---
9.18. Specialized Tools
5 AA - -
10.1.1. LAN Technologies
5 BB - -
10.1.2. Configure Switches
2b---
10.2.1. VLAN Fundamentals
5 BB - -
10.2.2. Configure VLANs
2b---
10.3. Configure Logical Security for
Network Equipment
2b---
10.4.1. Routing Fundamentals
5/7 BBB -
10.4.2. Configure Routers
2b---
10. SWITCHING AND ROUTING
TR: 1D7XX Learning Program (Percipio)
10.1. Switching
10.2. Virtual Local Area Network (VLAN)
10.4. Routing
9.11. Enterprise Logical Security
9.12. Network Topologies
9.17. Cable Management
1D7XX STS
5
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
10.4.3. Implement Logical Security
2b---
10.5. Troubleshoot Network Devices
2b---
11.1. Server Types
5 AA - -
11.2. Virtualization
5 BB - -
11.3.1. Concepts
5 BB - -
11.3.2. Configure
2b---
11.3.3. Troubleshooting
2b---
11.4.1. Concepts
5 BB - -
11.4.2. Configure
2b---
11.4.3. Troubleshooting
2b---
11.5.1. Concepts
5 BB - -
11.5.2. Configure
2b---
11.5.3. Troubleshooting
2b---
12.1.1. Services Concepts
5 BB - -
12.1.2. Start / Stop Services
1b---
12.2.1. Processes Concepts
5 BB - -
12.2.2. Start / Stop Processes
1b---
12.4. Definition
A---
12.4.1. Characteristics
AB - -
12.4.2. Service Model Types
AB - -
12.4.3. Deployment Models Types
AB - -
12.4.4. Benefits
AB - -
12.4.5. Implementation
Considerations
-A- -
12.2. Processes
12.3. Cloud Computing
11.3. Active Directory
11.4. Domain Name System (DNS)
11.5. Dynamic Host Configuration Protocol (DHCP)
12. SERVICES AND PROCESSES
TR: 1D7XX Learning Program (Percipio)
12.1. Services
11. APPLIANCES (SERVERS)
TR: 1D7XX Learning Program (Percipio)
1D7XX STS
6
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
13.1. End User Devices /
Components
5/7 BBB -
13.2.1. Operating System (OS)
5 AB - -
13.2.2. Mobile Device Operating
System
5 AA - -
13.2.3. Software Management
Policies
5 AA - -
13.2.4. Install
5 2b A - -
13.2.5. Configure
2b---
13.2.6. Troubleshoot
2b---
13.3.1. Infectious and Malicious
Software
5/7 ABB -
13.3.2. Apply Logical Security
2b---
13.4.1. Conditional Primitives
5 BB - -
13.4.2. Iterative Primitives
5 BB - -
13.4.3. Data Manipulation
5 BB - -
13.5. Perform Basic Scripting
5 2b b - -
13.6.1. Transport Layer Security
5 -B- -
13.6.2. Encoding
5 -B- -
13.6.3. Tunneling
AB - -
13.7.1. Data Validation
5 2b b
13.7.2. Sanitization
5 2b b
13.7.3. SQL Injection
5 -B
13.7.4. Code Injection
5 -B
13.7.5. Cross Site Scripting
5 -B
13.8.1. SSH
5 AB - -
13.8.2. SSL / TLS
5 AB - -
13.8.3. Secure FTP Versions
5 AB - -
13.4. Scripting
13.6. Transport Security
13.7. Input Validation
13.8. Common Protocols (e.g. Handshake, State, OSI Layer, Header Standard Port #)
13. CLIENT SYSTEMS
TR: 1D7XX Learning Program (Percipio)
13.2. Client Software
13.3. Security
1D7XX STS
7
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
13.8.4. HTTP(S)
5 AB - -
13.8.5. SNMP
5 AB - -
13.9.1. Ping
5 AB - -
13.9.2. Tracer / Traceroute
5 AB - -
13.9.3. Ipconfig / Ifconfig
5 AB - -
13.9.4. Netstat
5 AB - -
14.1.1. Purpose
5 AB - -
14.2.1. Best Practice Identification /
Sharing
5 AB - -
14.2.2. Change Management
5 AB - -
14.2.3. Knowledge Capture
5/7 ABB -
14.2.4. Lessons Learned
5 AB - -
15.1. Joint Task Force (JTF)
Organizational Structure
-ABC
15.2. Concepts of Aerospace
Expeditionary Force (AEF)
Employment
5/7 -AA-
15.3. UTC Management
7 - -B-
15.4. Readiness Status Reporting
7/9 --AB
15.5. Mission Essential Tasks
(METS)
7/9 --AC
15.6. Air Force Force Generation
(AFFORGEN)
5/7/9 -ABC
15.7. Agile Combat Employment
(ACE)
5/7/9 -ABC
15.8. Military Planning Process
--BC
15.9. Force Module
Communications Support Concept
7 - -A-
14. DATA ANALYST CORE COMPETENCIES
TR: 1D7X1K Learning Program (Percipio), AFMAN 33-396
14.1. Operationalized Knowledge Management
14.2. Agile Learning
15. EXPEDITIONARY COMMUNICATIONS
TR: 1D7XX Learning Program (Percipio); AFIs 10-401, 10-403; AFMAN 171302-O; https://jkodirect.jten.mil/Atlas2/page/login/Login.jsf;
https://aefonline.afpc.randolph.af.mil/default.aspx; AMC myLearning Gateway (AF Fundamentals of Expeditionary Mobility Operations); Deployable Comms CONOPS
(Uploaded)
16. WORK CENTER MANAGEMENT
TR: 1D7XX Learning Program (Percipio); AFIs 10-201, 21-103, 146352; DODI 1400.25V610_AFI36-807; TO 00-33A-1001; AFJQS XXXXX-212S
13.9. Command Line Network Utilities
1D7XX STS
8
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
16.1. Management Policies
5/7 -AA-
16.2.1. Base / Unit Roles and
Responsibilities
5/7 -AB-
16.2.2. Supervisor / Trainer Roles
and Responsibilities
5/7 -AB-
16.2.3. Task Certifier Roles and
Responsibilities
5/7 -AB-
16.2.4. Trainee Responsibilities
5 -A- -
16.2.5.1. Common Cyber Training
Sources
5/7 -AB-
16.2.5.2. 1D7XX and AFS-Specific
Learning Programs
5/7 -AB-
16.3.1. Air Force and Cyber
Inspections
5/7/9 - ABB
16.3.2. Self Assessment Program
5/7/9 - ABB
16.4.1. Job Data / Configuration
Management Documentation
(e.g.IMDS, Remedy, CIPS, IAO
Express)
5/7 -AB-
16.4.2. Training Record
Management (e.g. TBA, AFTR,
Patriot Excalibur)
7 - -B-
16.5.1. Asset / Property
Management (e.g. DPAS, CACRL)
----
17.1.1. Unit Training Planning
--BC
17.1.2. Formal Training
-ABC
17.1.3. Additional Training Sources
- ABB
17.2.1. Roles and Responsibilities
--AB
17.2.2. Awards and Recognition
--AB
17. UNIT LEVEL MANAGEMENT
17.1. Training
17.2. SEL Duties
16.2. Training
16.2.5. Training Resources
16.3. Inspection and Evaluation Programs
16.4. Automated Information Systems (AIS)
16.5. Equipment and Records Management
1D7XX STS
9
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
18.1. Career Field Functional
Management
5/7/9 -ABC
18.2. MAJCOM Functional
Management
5/7/9 -ABC
18.3. Base Functional Management
5/7/9 -ABC
18.4. Force Development /
Management
5/7/9 -ABC
19.1. Financial Management
5/7/9 -ABC
19.2. Funded Requirements
5/7/9 -ABC
19.3. Unfunded Requirements
5/7/9 -ABC
19.4. Resolve Capstone Scenario
Involving Resource Management
9 ---3c
20.1. Manpower Requirements
--BC
20.2. Air Force Manpower Standard
(AFMS) Application
--AB
20.3. Manpower Studies
--AB
20.4. Manpower Products
7/9 --BD
20.5. Allocating Personnel
7/9 --BD
20.6. Total Force Management
7/9 --BC
20.7. Resolve Capstone Scenario
Involving Manpower and
Organizational Changes
9 ---3c
21.1. Principles of Project
Management
5/7/9 -ABC
21.2. Resolve Capstone Scenario
Involving Project Management
9 ---3c
22.1. Purpose of DoDD 8140
----
22.2. Understand AF Preferred
Certifications
----
20. MANPOWER AND ORGANIZATION
TR: 1D7XX Learning Program (Percipio), AFPD 38-1, AFIs 38-101
21. PROJECTS AND REQUIREMENTS FUNCTION
TR: 1D7XX Learning Program (Percipio)
22. DODD 8140 SUPPORT
TR: AFMAN 17-1303, https://public.cyber.mil/cw/cwmp/dod-approved-8570-baseline-certifications, https://cwip.cce.af.mil/cyss/
certifiedworkforce/
18. FUNCTIONAL MANAGEMENT
TR: 1D7XX Learning Program (Percipio); AFECD; AFI 36-2651; AFPDs 36-28, 38-101; AFMAN 33-396; AFQTP 1D7XX-225E; 1D7XX CFETP
19. RESOURCE MANAGEMENT
TR: 1D7XX Learning Program (Percipio); AFPDs 10-6, 65-6; AFIs 10-601, 65601 V(1) and V(2)
1D7XX STS
10
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
23.1. Stress, Nutrition, and Fitness
BBBC
23.2. Conduct Effective Feedback
2b B C C
23.3. Demonstrate Critical Thinking
Principles
2b B C C
24.1. Air Force Job Qualification
Standards (JQS) and Qualification
Training Packages (QTP)
TR:
https://usaf.dps.mil/teams/10445/def
ault.aspx,
https://www.youtube.com/@qualifica
tiontrainingfligh1134/, https://lms-
jets.cce.af.mil/moodle/course/index.
php?categoryid=5
----
24.2. Formal Training Courses
TR: 1D7XX CFETP Section D,
Training Course Index;
https://usaf.dps.mil/teams/10445/def
ault.aspx
----
23. HUMAN PERFORMANCE
24. SECONDARY TRAINING DOCUMENTS
1D7XX STS
11
Atch 2

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1.1. Duties of the AFSC
5/7 ABB -
2.1.1.1. Evaluate User
Requirements
5 BB - -
2.1.2. Solutions Design,
Development, Testing, and
Deployment
5/7 ABB -
2.1.3. User Documentation
5 AB - -
2.2.1. Change Management
5/7 AAB -
2.2.2. Critical Thinking
5/7 BBB -
2.2.3. Knowledge Capture
5/7 AAB -
2.2.4. Lessons Learned
5 AB - -
2.3.1. Analytics
-B- -
2.3.2. Expertise Tracking /
Marketing
-B- -
2.3.3. Innovation Management
-B- -
2.3.4. Operational Assessments
-bb-
2.3.5. Knowledge Engineering
-B- -
2.3.6. Metrics and Measurement
-B- -
2.3.7. Project Management
-A- -
2.3.8. Roles / Responsibility
Capture (RACI Matrix)
-bb-
2.3.9. Task Tracking Methodologies
-B- -
2.3.10. Work Methodologies (Agile,
Kanban, Capture)
-BB-
2.4.1. Brainstorming Methods
5/7 ABB -
2.4.2. Collaboration Tools and
Environments
5/7 BBB -
2.4.3. Communication Plans
-b- -
2.4. Shared Understanding
1. DATA OPERATIONS
TR: 1D7X1P Learning Program (Percipio), AFMAN 33-396, AFH 36-2618, AFECD
2.1. Operationalized Data Operations
2. DATA OPERATIONS CORE COMPETENCIES
TR: 1D7X1P Learning Program (Percipio), AFMAN 33-396
2.1.1. Elicit User Requirements
2.2. Agile Learning
2.3. Enhance Performance
1. Implementation. This STS will be used for technical training provided by AETC for the 3-level course.
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
1D7X1P STS
1
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
2.4.4. Communication Skills
5/7 ABB -
2.4.5. Content Management
-BB-
2.4.6. Dashboards
-B- -
2.4.7. Enterprise Knowledge
Dissemination
5 AB - -
2.4.8. Visualization of Information
-BB-
3.1. Theory and Analysis
5 AB - -
3.2. Collect and Manage
5 AB - -
3.3. Reporting and Presentation
5 AB - -
4.1.1. Information Concepts
5 BB - -
4.1.2. Types of Services
5 BB - -
4.1.3. Standards
5 BB - -
4.2.1. Policy
5/7 AAB -
4.2.2. Roles and Responsibilities
5 AB - -
4.2.3. Site Structure
5 AB - -
4.2.4. Identify Storage Parameters
-B- -
4.2.5.1. Types
5 BB - -
4.2.5.2. Purpose
5 BB - -
4.2.5.3. Create Sites
5 2b b - -
4.2.5.4. Delete Sites
5 2b b - -
4.2.5.5. Reset Site
5 2b b - -
4.2.5.6. Manage Site Layout
5 2b b - -
4.2.5.7. Create / Use Dashboards
5 2b b - -
4.2.6.1. View Web Analytics
5 2b b - -
4.2.6.2. Activate Site Features
5 2b b - -
4.2.6. Site Actions
3. DATA LITERACY
TR: 1D7X1P Learning Program (Percipio)
4. ENTERPRISE INFORMATION SERVICES (EIS)
TR: 1D7X1P Learning Program (Percipio); AFMAN 33-396; https://www.milsuite.mil/; https://www.usability.gov/about-us/index.html; AF e-Learning: SharePoint 2013
ISBN #9781118510711, SharePoint 2010 ISBN #9781118105054; AFJQS1D7XX-225S
4.1. Overview
4.2. Content Management Systems (CMS)
4.2.5. Sites / Pages
1D7X1P STS
2
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
4.2.6.3. Activate Site Collection
Features
5 2b b - -
4.2.6.4. Site Collection Audit
5 2b b - -
4.2.6.5. Create Customized
Navigation
5 2b b - -
4.2.7.1. Establish Site Columns
5 2b b - -
4.2.7.2. Add Site Content Type
5 2b b - -
4.2.7.3. Manage Site Settings
5 2b b - -
4.2.7.4. Organize
5 2b b - -
4.2.8.1. Create Hierarchy
5 2b b - -
4.2.8.2. Create / Manage Users
5 2b b - -
4.2.8.3. Create / Manage Groups
5 2b b - -
4.2.9.1. Create Custom Content
Types
5 2b b - -
4.2.9.2. Add
5 2b b - -
4.2.9.3. Move
5 2b b - -
4.2.9.4. Delete
5 2b b - -
4.2.10.1. Manage Templates
5 2b b - -
4.2.10.2. Create a List
5 2b b - -
4.2.10.3. Modify Columns
5 2b b - -
4.2.10.4. Export
5 2b b - -
4.2.10.5. Modify Form View
5 2b b - -
4.2.11.1. Manage Templates
5 2b b - -
4.2.11.2. Create a Document
Library
5 2b b - -
4.2.11.3. Force Check In / Check
Out a Document
5 2b b - -
4.2.11.4. Manage Version Control
5 2b b - -
4.2.11.5. Set Alerts
5 2b b - -
4.2.10. Lists
4.2.11. Library
4.2.12. Views
4.2.7. Galleries
4.2.9. Content (files, graphics, Excel files, links, graphics, calendars, etc.)
4.2.8. Permissions
1D7X1P STS
3
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
4.2.12.1. Manage
5 2b b - -
4.2.12.2. Create a Standard
5 2b b - -
4.2.12.3. Create a Data Sheet
5 2b b - -
4.2.12.4. Create / Manage Filters
5 2b b - -
4.2.12.5. Use Conditional
Statements
5 2b b - -
4.2.13.1. Purposes
5 BB - -
4.2.13.2. Managing Web / App
Parts
5 2b b - -
4.2.14.1. Recover From Recycle Bin
5 2b b - -
4.2.14.2. Recover From Site
Collection Recycle Bin
5 B B - -
5.1.1. Goals and Principles
5 AB - -
5.1.2. Use Software Development /
Engineering Tools
5 2b b - -
5.1.3. Compiling
5 Bb - -
5.2.1. Define Problem
5 3b c - -
5.2.2. Create Problem Solution
Statements
5 3b c - -
5.2.3. Develop Problem Solution
5 3b c - -
6.1.1. Software Quality Metrics
5 AB - -
6.1.2. Extreme Programming
5 BB - -
6.1.3. Lifecycle Methodologies
5 AB - -
6.1.4. Test Driven Development
5 2b b - -
6.1.5. Iterative Development
5 AB - -
6.1.6. Continuous Integration /
Continuous Deployment (CI / CD)
5 AB - -
4.2.13. Web Parts / App Parts
4.2.14. Item Recovery
6. SOFTWARE ENGINEERING
TR: 1D7X1P Learning Program (Percipio)
5. SOFTWARE DEVELOPMENT FUNDAMENTALS
TR: 1D7X1P Learning Program (Percipio)
5.1. Software Engineering
5.2. Problem Solving
6.1. Technical Design Considerations
1D7X1P STS
4
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
6.2.1. Software System
Documentation
5 AB - -
6.3.1. Concepts
5 AB - -
6.3.2. Design
5 AB - -
6.3.3. Programming
2b B - -
6.4.1. Government Cloud Providers
-B- -
6.4.2. Commercial Cloud Providers
-B- -
6.5.1. Reasoning / Purpose
5 AB - -
6.5.2.1. JSON
5 AB - -
6.5.2.2. XML
5 AB - -
6.7. Develop User Stories
5 2b b - -
6.8. Feasibility Studies
-B- -
7.1. Overview
5 AB - -
7.2.1. Purpose
5 AB - -
7.2.2. Repositories
5 BB - -
7.2.3. Lock Modify Unlock Model
5 BB - -
7.2.4. Copy Modify Merge Model
5 BB - -
7.2.4.1. Issue Generation
5 BB
7.2.4.2. Pull Requests
5 BB
7.2.5. Utilize Source Control Tools
5 2b c - -
7.2.6.1. Version Number Scheme
AB - -
7.2.6.2. Release Baselines
-B- -
7.2.6.3. Concurrent Release
-B- -
6.3. Object Oriented and Functional Software Engineering
6.5.2. Types
6.6. Persistent Storage Functions
7. SOFTWARE CONFIGURATION MANAGEMENT
TR: 1D7X1P Learning Program (Percipio)
7.2. Source Control
7.2.6. Versioning
6.4. Cloud Providers
6.5. Serialization
6.2. Create / Update Software Documentation
1D7X1P STS
5
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
7.3.1. Development of Library
Modules
-B- -
7.3.2. Use
2b b - -
7.3.3. Maintain
-B- -
8.1.1. General Overflow Attacks
5 BB - -
8.1.2. Format String Attack
5 BB - -
8.1.3. Fuzzing
-B- -
8.1.4. Safe Functions
5 -B- -
8.1.5. Memory Leaks
5 BB - -
8.1.6. Root Kits
-B- -
8.1.7. Privilege Escalation / Lateral
-B- -
8.1.8. Check Return Values
-B- -
8.1.9. Shellcode
-B- -
8.2.1. Session Hijacking
-B- -
8.2.2. Integrity / Checksum Check
-B- -
8.2.3. Cross Site Request Forgery
-B- -
8.3.1. Block
-A- -
8.3.2. Stream
-A- -
8.3.3. Securely Stored Tokens /
Keys / Certificates
-A- -
8.3.4. End to End Encryption
-A- -
8.3.5. RSA
-A- -
8.3.6. Public Key Infrastructure
(PKI)
-A- -
8.3.7.1. Certificate Trust Chain
-A- -
8.3.7.2. Certificate Revocation List
-A- -
8. SOFTWARE SECURITY
TR: 1D7X1P Learning Program (Percipio)
8.1. System Security
8.2. Transport Security
8.3. Encryption
8.3.7. Certificates
7.3. Software Support Libraries
1D7X1P STS
6
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
8.3.7.3.1. OpenSSL
-A- -
8.3.7.4. Authentication Levels
-A- -
8.4.1. Strings (Tools)
-A- -
8.4.2. Virus Total (Tool)
-A- -
8.4.3. Advanced Static Analysis
-A- -
8.4.4. Advanced Dynamic Analysis
-A- -
8.4.5. Wireshark (Tool)
-A- -
8.4.6. Imports / Exports
-A- -
8.4.7. Isolate in Virtual Machine
-A- -
8.5. Common Vulnerabilities and
Exposures (CVE)
-A- -
8.6. Information Assurance
Vulnerability Alert (IAVA)
-A- -
8.7. Auditing
-B- -
9.1.1. Test Plans
A---
9.1.2.1. Format
2b b - -
9.1.2.2. Positive Testing
2b b - -
9.1.2.3. Negative Testing
2b b - -
9.1.3. Bug Reporting
5 AB - -
9.2.1. Black / White Box Testing
A---
9.2.2.1. Unit Testing
5 AB - -
9.2.2.2. Integration Testing
5 AB - -
9.2.2.3. System / Regression
Testing
5 AB - -
9.2.2.4. Acceptance Testing
5 AB - -
9.2.3. Performance Testing
5 AB - -
9.2.4. End to End Testing
5 AB - -
9.2. Testing Types
9.2.2. Functional Testing
9. SOFTWARE TESTING
TR: 1D7X1P Learning Program (Percipio)
8.3.7.3. Certificate Generation
8.4. Malware Reverse Engineering
9.1. Documentation
9.1.2. Test Cases
1D7X1P STS
7
Atch 3
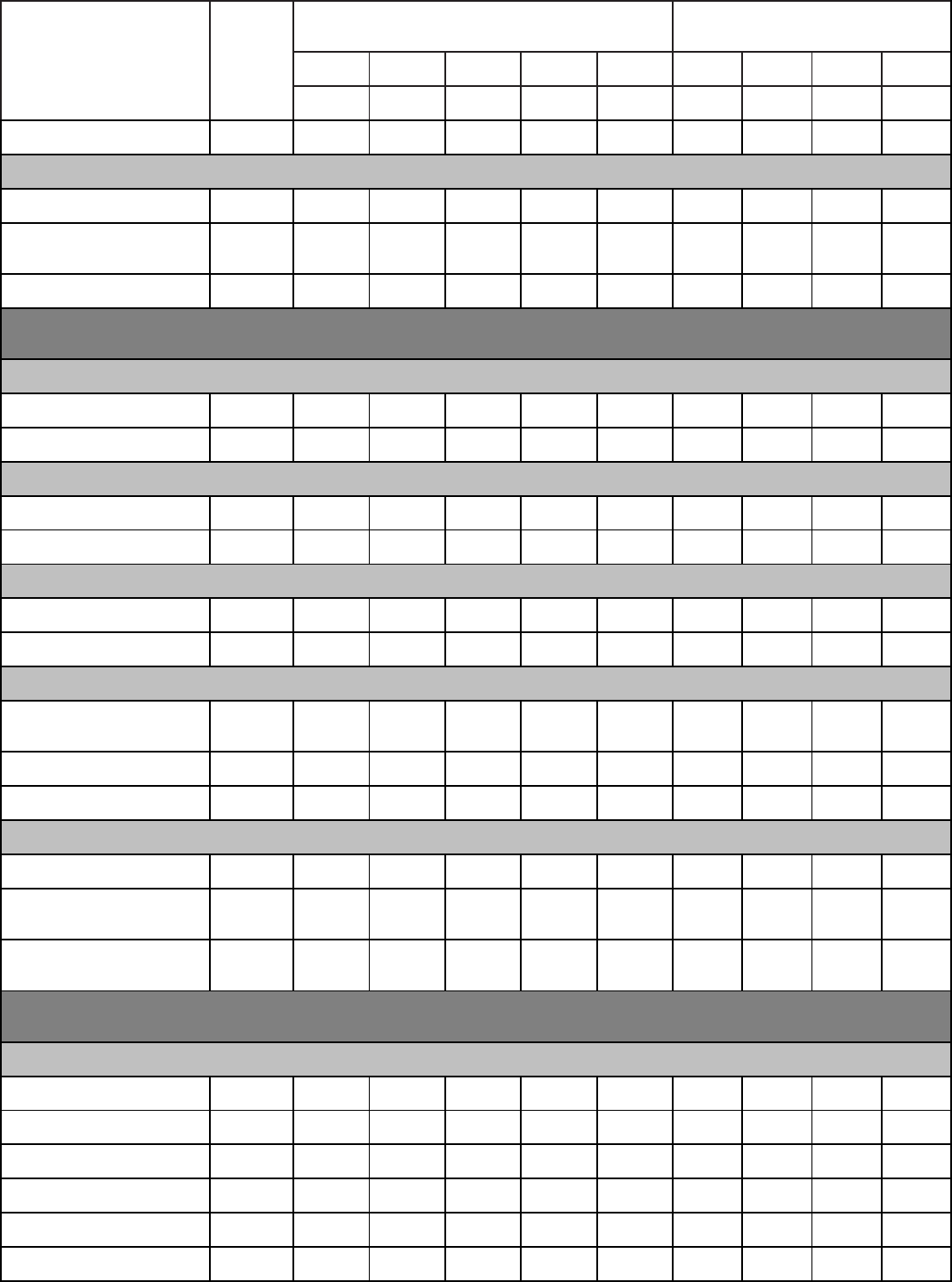
ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
9.2.5. Security Scanning
5 AB - -
9.2.7. GUI Testing
5 AB - -
9.2.8. Web Services / API Testing
5 AB - -
9.3. Continuous Testing
5 AB - -
10.1.1. Collection
5 AB - -
10.1.2. Prioritization
-B- -
10.2.1. Data Entry
-B- -
10.2.2. Correct Logic
2b b - -
10.3.1. Migration
-B- -
10.3.2. Redesign
-BB-
10.4.1. Federal Requirements
(ATO, ATC, etc.)
-B- -
10.4.2. Functional Testing
2b b - -
10.4.3. Security Testing
2b b - -
10.5.1. Hardware Limitations
-B- -
10.5.2. OS / Host System
Limitations
-B- -
10.5.3. Complexity Analysis (Big-O
Notation)
-b- -
11.1.1. Cache Levels
----
11.1.2. Memory Allocation
-A- -
11.1.3. Stack
-A- -
11.1.4. Heap
-A- -
11.1.5. Data Types
5 AB - -
11.2. Character Encoding
5 AB - -
9.2.6. Nonfunctional Testing Automation
10. SOFTWARE MAINTENANCE
TR: 1D7X1P Learning Program (Percipio)
10.1. Corrective Bug Management
10.5. Perfective Efficiency Analysis
10.4. Perfective Periodic Validation
11. ARCHITECTURE
TR: 1D7X1P Learning Program (Percipio)
11.1. Memory
10.3. Adaptive
10.2. Error Correction
1D7X1P STS
8
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
11.3. Compilers / Flags
-B- -
12.1.1. Networking RFCs
-B- -
12.1.2. Network Byte Order
-B- -
12.2.1. BSD Sockets
-B- -
12.2.2. WinSock
-B- -
12.2.3. Pipes
-B- -
12.2.4. FIFOs
-B- -
12.2.5. Websockets
-B- -
12.3.1. Web Proxies
-A- -
12.3.2. Forward Proxy
-A- -
12.3.3. Reverse Proxy
-A- -
12.3.4. Anonymous Proxies
-A- -
12.3.5. Tunneling
-A- -
13.1. User Centered Design
AB - -
13.2. Information Architecture
AB - -
13.3. Interaction Design
AB - -
13.4. Visual Design
AB - -
13.5. Accessibility
AB - -
13.6. Usability
AB - -
14.1. Overview
A---
14.2. Power Apps
BB - -
14.3. Power BI
BB - -
14.4.1. Power Automate
Fundamentals
BB - -
14.4.2. Create Workflow
2b b - -
14.5. Power Virtual Agents
A---
13. USER EXPERIENCE DESIGN (UXD)
TR: 1D7X1P Learning Program (Percipio)
14.4. Power Automate
14. POWER PLATFORM
TR: 1D7X1P Learning Program (Percipio)
12. NETWORKING
TR: 1D7X1P Learning Program (Percipio)
12.1. Network Fundamentals
12.2. Sockets
12.3. Proxy / Redirection
1D7X1P STS
9
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
15.1.1. About
BB - -
15.1.2. Best Practices
BB - -
15.1.3. HTML Structure
2b b - -
15.1.4. Create Elements, Attributes,
Headers, and Paragraphs
2b b - -
15.1.5. Use Styles
2b b - -
15.1.6. Use Formatting Elements
2b b - -
15.1.7. Add Links
2b b - -
15.1.8. Use Images
2b b - -
15.1.9. Add Tables
2b b - -
15.1.10. Create Lists
2b b - -
15.1.11. Create Hyperlinks
2b b - -
15.1.12. Add Email Links
2b b - -
15.1.13. Add Comments
2b b - -
15.1.14. Resources
BB - -
15.2.1. Sequential Design
-B- -
15.2.2. Threading
-b- -
15.2.3. Design Patterns (e.g. MVC)
5 AB - -
15.2.4. JavaScript Fundamentals
B
15.2.5. JavaScript / HTTP
Interaction
1b b - -
15.2.6. Intro to JavaScript
Frameworks
AB - -
15.2.7. Document Object Model
(DOM)
BB - -
15.2.8. Representational State
Transfer (REST)
-B- -
15.3.1. About
BB - -
15.3.2. Syntax
BB - -
15.2. Design Concepts
15.3. Cascading Style Sheets
15. WEB DEVELOPMENT
TR: 1D7X1P Learning Program (Percipio); http://www.w3.org/standards/webdesign/; https://www.w3.org/WAI/intro/accessibility.php; https://www.usability.gov/;
https://www.w3schools.com/tags/; https://www.w3schools.com/html/; https://www.w3schools.com/css/; https://www.w3schools.com/cssref/;
https://www.w3schools.com/js/; AF e-Learning: JavaScript Essentials Library ID: sl_jsce_a01_it_enus, HTML & CSS ISBN #9780071496292; Web Design for Dummies
ISBN #9781118004906
15.1. Hypertext Markup Language Code (HTML)
1D7X1P STS
10
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
15.3.3. Selectors
BB - -
15.3.4. Three Ways to Insert
Cascading Style Sheet
BB - -
15.3.5. Work with Colors
2b---
15.3.6. Work with images
2b---
15.3.7. Box Model
BB - -
15.3.8. Use Height and Width
Modifications
2b B - -
15.3.9. Use Auto Value
2b---
15.3.10. Use Text Modification
2b---
15.3.11. Use Icons and Stylesheets
2b---
15.3.12. Add Commenting
2b---
15.3.13. Resources
BB - -
16.1.1. Logical
AB - -
16.1.2. Normalization
AB - -
16.1.3. Denormalization
AB - -
16.1.4. Physical
AB - -
16.1.5.1. Relational
AB - -
16.1.5.2. Key Value
AB - -
16.1.5.3. Document
AB - -
16.1.5.4. Graph
AB - -
16.1.5.5. Column Oriented
AB - -
16.1.6.1. CAP Theorem
-BB-
16.1.6.2. Atomicity, Consistency,
Isolation, Durability (ACID)
-BB-
16.1.6.3. Basically Available, Soft
State, Eventual Consistency (BASE)
-BB-
16.1.7. Query Performance Tuning
-BB-
16.1.8. Backups
AB - -
16.1.6. Transaction Processing
16. DATABASE
TR: 1D7X1P Learning Program (Percipio)
16.1. Design
16.1.5. Data Models
1D7X1P STS
11
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
16.1.9. Restore and Recovery
AB - -
16.2.1. Table
AB - -
16.2.2. View
AB - -
16.2.3. Stored Procedure
AB - -
16.2.4. Trigger
AB - -
16.2.5. Index
AB - -
16.2.6. Query Language
Fundamentals
2b B - -
17.1. Containerization Technologies
A---
17.1.1. Create Container
1b---
17.1.2. Container Customization
BB - -
17.1.3. Run Container
2b---
17.1.4. Deploy Container
2b---
17.1.5. Pull Containers from
Repository
2b---
17.1.6. Container Management /
Clustering
AB - -
16.2. Objects
17. CONTAINERIZATION
TR: 1D7X1P Learning Program (Percipio)
1D7X1P STS
12
Atch 3

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1.1. Duties of the AFS
5/7 ABB -
2.1.1. Multimeter
5 AA - -
2.1.2. Time Domain Reflectometry
B---
2.1.3. Optical Time Domain
Reflectometry
5 BB - -
2.1.4. Bit Error Rate Testing
B---
2.1.5. Spectrum Analyzer
----
2.1.6. Local Area Network (LAN)
Test Set
A---
2.1.7. Network / Protocol Analyzer
(Sniffer)
B---
2.1.8. Breakout Box
AA - -
2.1.9. Fiber Optic Test Set (Light
Source)
A---
2.2.1. Multimeter
5 -b- -
2.2.2. Fiber Optic Test Set (Light
Source)
----
2.3.1. Inventory / Accountability
Fundamentals
A---
2.3.2. Maintenance Documentation
5 AA - -
2.3.3. Installation Standards
5 AA - -
2.3.4. Inspections (PMI)
5/7 AAB -
2.4.1. Troubleshoot Network
Equipment (e.g. IP Data, Voice,
Video)
2b---
2.4.2. Authorized Service
Interruptions (ASIs)
AB - -
2.5.1. Fundamentals
5 BB - -
2.4. Troubleshooting
2.5. Grounding
1. ENTERPRISE OPERATIONS CAREER FIELD
TR: 1D7X1Q Learning Program (Percipio), AFI 36-2101, 1D7XX CFETP, AFECD
2.1. Test Equipment Theory
2.3. Standard Maintenance Concepts
2. MAINTENANCE PRACTICES
TR: 1D7X1Q Learning Program (Percipio), TO 33K-1-100, and Applicable Test Equipment TOs
2.2. Perform Maintenance Using Test Equipment
1. Implementation. This STS will be used for technical training provided by AETC for the 3-level course.
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
1D7X1Q STS
1
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
2.5.2. Verify Proper Grounding (i.e.
Equipment / Rack)
5 -b- -
2.5.3. Bonding
AA - -
2.5.4. Shielding
AA - -
2.5.5. Lightning Protection
AA - -
2.6.1. Cable Installation Standards
BB - -
2.6.2. Ethernet Cable Termination
BB - -
2.6.3. Fiber Cable Termination
BB - -
2.7.1. Fundamentals
5 AA - -
2.7.2. Concepts
5 -A- -
2.7.3. Handling, Packaging, and
Storing
5 -A- -
3.1.1. Network Virtualization
B---
3.1.2. Software Defined Networking
B---
3.2.1. Switching Application
BB - -
3.2.2. Switching Standards
B---
3.2.3. Link Aggregation
AB - -
3.3.1. Protocol Application
BC - -
3.3.2. Protocols / Standards
B---
3.4.1. Fundamentals
AB - -
3.4.2. Application
B---
3.4.3. Configure
2b---
3.4.4. IEEE 802 Standards
BC - -
3.5.1. Enterprise Wireless Network
Application
B---
2.6. Cable
2.7. Electrostatic Discharge (ESD)
3.1. Enterprise Networking
3.3. Layer 3 (Routing)
3.4. Spanning Tree (STP)
3.5. Wireless Networking (WLAN)
3. IP NETWORKING
TR: 1D7X1Q Learning Program (Percipio), AFI 36-2101, 1D7XX CFETP, AFECD
3.2. Layer 2 (Switching)
1D7X1Q STS
2
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
3.5.2. Enterprise Wireless Protocols
/ Standards
B---
3.5.3. Wireless Access Points
Application
BC - -
3.5.4. Configure Extended Service
Set Configurations
2b b - -
3.6.1. Fundamentals
AB - -
3.6.2. DSCP Fundamentals
AB - -
3.6.3. Configure
2b---
3.6.4. Redundancy Fundamentals
AB - -
3.7.1. Network Management
Software
B---
3.7.2. SNMP
BC - -
3.7.3. Network Traffic Analysis
(sFlow, Netflow, jFlow)
BC - -
3.7.4. Implement IP Network
Monitoring
2b---
3.7.5. Mobile Device Management
AB - -
4.1.1. Telephony Fundamentals
5 AB - -
4.1.2. Telephony Capabilities
(PSTN, POTS, VOIP, TEAMS)
AB - -
4.2.1. Fundamentals
A---
4.3.1. Concepts
AB - -
4.3.2. 911 / E-911
A---
5.1.1. Fundamentals of IT
Documentation
BB - -
5.1.2. Service Level Agreements
(SLAs)
AA - -
3.6. Quality of Service (QoS)
4.1. Telephony
4.2. Call Routing
4.3. Telephony Switching
5. ENTERPRISE ADMINISTRATIVE FUNCTIONS
TR: 1D7X1Q Learning Program (Percipio)
5.1. Fundamentals of IT
3.7. IP Network Monitoring
4. VOICE COMMUNICATIONS
TR: 1D7X1Q Learning Program (Percipio), Applicable Commercial Manuals
1D7X1Q STS
3
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
5.1.3. Project Support Agreement
(PSA)
-A- -
5.2.1. Identify
-B- -
5.2.2. Analyze
-B- -
5.3.1. COMSEC Inventory
Procedures
b---
5.3.2. Perform Key Transfer Using
Common Fill Device
2b---
6.1.1. Fundamentals
AAB -
6.1.2. Configure / Use IP Crypto
Equipment
2b---
6.2.1. Symmetric and Asymmetric
Keys
A---
7.1.1. Uninterrupted Power Supplies
(UPS)
5 AB - -
7.1.2. Facility Battery Backups
5 AB - -
7.1.3. Generators
5 AB - -
7.2. Long Haul Communications
Fundamentals
5 AB - -
7.3. AOR Power Requirements
-B- -
8.1.1. Information Protection
Principles
AA - -
8.1.2. Rules of Engagement
A---
8.1.3. Assessment and
Authorization
A---
8.1.4. Event Response
A---
8.1.5. Security Patch
Implementation
A---
5.2. Communications Network Trend Analysis
5.3. Communications Security (COMSEC)
7. CRITICAL COMMUNICATIONS FACILITIES POWER SYSTEMS
TR: 1D7X1Q Learning Program (Percipio), Applicable Commercial Manuals
6. ENCRYPTION / DECRYPTION
TR: Applicable Commerial Manuals
6.1. Crypto Devices
6.2. Crypto Keys
8.1. Security
7.1. Power Systems
8. INFORMATION PROTECTION OPERATIONS
TR: 1D7X1Q Learning Program (Percipio)
1D7X1Q STS
4
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
8.1.6. Malicious Logic Protection
A---
8.2.1. Concept
5 AB - -
8.2.2. Steps
A---
8.3.1. Principles
AB - -
9.1. Programming Languages
5 AB - -
9.2. Graphical User Interfaces (GUI)
5 AB - -
9.3. Cross Domain Data Solutions
5 AA - -
9.4. Memory Structure
5 AB - -
9.5. Interrupt Requests (IRQ)
5 AB - -
9.6. Drivers
5 AB - -
9.7. Basic Input / Output System
(BIOS)
5 AB - -
9.8. Memory
5 AB - -
9.9. Complementary Metal Oxide
Semiconductor (CMOS)
5 AB - -
10.1.1. Storage Types
5 BB - -
10.1.2. System Storage
Configuration
5 AB - -
10.1.3. I / O Technologies
AB - -
10.1.4. Blade / Backplane
Technologies
5 AB - -
10.2.1. Concepts
5 BB - -
10.2.2. Server Virtualization
5 BB - -
10.2.3. Virtualization Environment
5 BB - -
10.2.4. Client Virtualization
5 BB - -
10.2.5. Implement Virtualization
2b---
10.1. Hardware
10. SERVERS
TR: 1D7X1Q Learning Program (Percipio)
10.2. Virtualization Overview
10.2.6. Operating Systems
9. INFORMATION TECHNOLOGY SYSTEMS FUNDAMENTALS
TR: 1D7X1Q Learning Program (Percipio)
8.2. Defense in Depth
8.3. Boundary Protection
1D7X1Q STS
5
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
10.2.6.1. Types and Characteristics
5 BB - -
10.2.6.2. PMO Systems
5 BB - -
10.2.6.3. Configure Common Server
Roles
5 2b b - -
10.2.6.4. Perform basic Shell
configurations
5 2b b - -
10.2.6.5. Configure Basic Cmd Line
Programs
5 2b b - -
10.2.6.6. Configure Basic Account
Management functions
5 2b b - -
10.2.6.7. Perform Basic Hardening
procedures
5 2b b - -
10.2.6.8. Perform Basic Process
Management functions
5 2b b - -
10.2.6.9. Linux
5 BB - -
10.2.7.1. Remote Access
AB - -
10.2.8.1. Flat File
AB - -
10.2.8.2. Relational
AB - -
10.2.8.3. NoSQL
AB - -
10.2.8.4. Schema
AB - -
10.2.8.5. Compile Basic SQL Query
and Reports
2b---
10.2.9.1. Language Types
BB - -
10.2.9.2. Web Services
AB - -
10.2.9.3. Web Security
AB - -
10.3.1. Backup / Restore Process
AB - -
10.3.2. Offsite Storage
AB - -
10.3.3. Continuity of Operations
(COOP)
AB - -
10.3.4. Priority Restoration Plan
AB - -
10.3.5. Alternate Power
AB - -
10.3.6. Startup and Shutdown
Procedures
5 2b b - -
10.3. Disaster / Contingency / Operational / Crisis
10.2.9. Web Fundamentals
10.2.8. Database
10.2.7. Applications
1D7X1Q STS
6
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
11.1.1. Components of Public Key
Infrastructure (PKI)
AB - -
11.1.2. Biometrics
5 AB - -
11.2. Systems Management
5 AB - -
11.3.1. Incident / Event Reporting
5 AB - -
11.3.2. Perform Incident Response
5 2b b - -
11.4.1. Monitor System Resources
5 2b b - -
11.4.2. Identify Event Logging Tools
AB - -
12.1. Types and Characteristics
5 AB - -
12.2. Boundary Interaction Tools
AB - -
13.1.1. Functions
5 AB - -
13.1.2. Base Roles
AB - -
13.1.3. NOS Roles
AB - -
13.1.4. Describe DISA requirements
AB - -
13.1.5. Describe Assessment and
Authorizations (A&A) Requirements
AB - -
13.2.1. Functions and Capabilities
BB - -
13.2.2. Review a Vulnerability Scan
5 2b b - -
13.3.1. Purpose
AB - -
11. NETWORKED SYSTEMS
TR: 1D7X1Q Learning Program (Percipio)
11.1. Network Authentication
11.4. Network Operations (NetOps) Monitoring
13.3. Patch Management
12. ENTERPRISE BOUNDARY CONCEPTS
TR: 1D7X1Q Learning Program (Percipio)
13. VULNERABILITY MANAGEMENT
TR: 1D7X1Q Learning Program (Percipio)
13.1. Air Force Standard Vulnerability Assessment (VA)
13.2. Air Force Standard Vulnerability Assessment (VA) Tools
11.3. Event Response
1D7X1Q STS
7
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
13.3.2. Client Install and Uninstall
2b---
13.3.3. Install Security Patches
2b---
13.3.4. Utilize Dashboard for
Reporting
2b---
14.1. Types and Characteristics
5 AB - -
14.2. Intrusion Detection Methods
5 BB - -
14.3. Intrusion Detection Tools
5 BB - -
14.4. Respond to an Incident
2b---
14.5.1. Functions
5 AB - -
14.5.2. Configure End Point Client
2b---
14.6. Network Based Intrusion
Detection System Functions
5 AB - -
14.8. Hardware
5 -b- -
14.9. Troubleshoot basic OS and
Applications issues
5 2b b - -
14.10. Troubleshoot basic OS and
Startup Problems
5 2b b - -
14.11. Troubleshoot Network issues
5 2b b - -
15.1. Cyber Taskings (MPTOs,
CTOs, etc.)
5 BB - -
15.2. Collaborative Environments
5 AB - -
16.1. Roles and Responsibilities
AB - -
16.2. Essential Components and
Factors of ICAM Program
5 AA - -
17.1. Training and Resources
5 AA - -
17.2. End Point Security
5 AB - -
16. IDENTITY CREDENTIALING AND ACCESS MANAGEMENT (ICAM)
TR: 1D7X1Q Learning Program (Percipio), AFMAN 17-1304
14.7. Troubleshooting
15. CYBER COLLABORATION, PUBLICATIONS, AND DIRECTIVES
TR: 1D7X1Q Learning Program (Percipio), AFI 33-360
14.5. End Point Protection
17. COMPUTER SECURITY (COMPUSEC)
TR: 1D7X1Q Learning Program (Percipio), AFI 17-130, AFMAN 171301, MPTO 00-33B-5006
14. INTRUSION CONTROLS
TR: 1D7X1Q Learning Program (Percipio)
1D7X1Q STS
8
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
18.1. Program Overview
5 AA - -
18.2. Air Force IT Category (AFI
driven) / DoD IT Types (DoD driven)
5 AA - -
18.3. Security Objectives
5 AB - -
18.4. Roles and Responsibilities
5 AB - -
18.5. System Development
Lifecycle
5 AA - -
19.1. Roles and Responsibilities
5 AA - -
19.2. TEMPEST Information
Messages
5 -A- -
20.1. Purpose
5 AA - -
20.2.1. KMI Operating Account
Manager (KOAM)
AAA -
20.2.2. COMSEC Clerks
5 AA - -
20.2.3. Role Exclusion
-A- -
20.2.4.1. COMSEC Material
Request
5 -A- -
20.2.4.2. COMSEC Material
Issuance
5 -A- -
20.2.4.3. Record Maintenance and
Disposition
5 -A- -
20.2.6. Additional Protection
Measures (Photography, Personal
Electronics, Public Display)
5 -B- -
20.2.7. Accounting Legend Codes
(ALC)
5 -B- -
20.3.1. Purpose
5 -A- -
20.2.5. COMSEC Training Program
20.3. Cryptographic Access Program (CAP)
20.2. COMSEC Role Requirements / Responsibilities
19. TEMPEST PROGRAM MANAGEMENT
TR: 1D7X1Q Learning Program (Percipio); AFMANs 17-1305 Vol 1 (Unclass) & Vol 2 (Classified) (in development), 33-214 (Classified) (IACE:
http://intelshare.intelink.sgov.gov/sites/af_cybersecurity/SitePages/Home.aspx); Emission Security handbook; DISA Wireless STIG; MPTOs 00-33B-2861, 00-33B-2862,
00-33B-2863; AFSSIs 7700, 7702, 7703; TEMPEST Wiki: https://cs2.eis.af.mil/sites/10060/Wiki/TEMPEST.aspx
20. COMMUNICATIONS SECURITY (COMSEC) MANAGEMENT
TR: 1D7X1Q Learning Program (Percipio); AFI 17-130; AFMAN 1-71302-O; TO 00-33-B-5001; AFSSIs 3000-series; DOC 042-12; CNSSIs 4003, 4004, 4005; DoDI
5210.82; CJCSIs 3260.01, 3260.02
20.2.4. Procedures and Process Management
18. RISK MANAGEMENT FRAMEWORK (RMF)
TR: 1D7X1Q Learning Program (Percipio); RMF Knowledge Service; AFI 17-101; DoD 8510.01; FIPS 199, 200; SPs 800-53, 800-37, 800-53A, 800-60, 800-64; CNSSI
1253
1D7X1Q STS
9
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
20.4.1. Authorized Access
5 -B- -
20.4.2. Physical Security Handling
Requirements
5 -B- -
20.4.3. COMSEC Forms
5 AB - -
20.4.4. COMSEC Access List
5 AB - -
20.4.5. Emergency Action Plans
(EAPs)
AB - -
20.5.1. Disposition
5 AA - -
20.5.2. Destruction
5 AB - -
20.6.1. Two Person Integrity (TPI)
Handling Procedures
5 -B- -
20.6.2. TPI Material Storage
Requirements
5 -B- -
20.6.3. Tactical Situations Storage
Requirements
5 -A- -
20.6.4. Transportation
Requirements for TPI
5 -A- -
20.7.1. Introduction
A---
20.7.2. Incident Types / Concepts
5 -A- -
20.7.3. Incident Reporting
5 -A- -
20.7.4. Disposal of Material Involved
in a COMSEC Incident
5 -A- -
20.8. COMSEC Audits
5 -B- -
20.9. Secure Voice Program
5 AB - -
21.1.1. End User Support
5 AB - -
21.1.2. Wire Color Coding
Standards
5 AB - -
21.1.3. Construct Copper Ethernet
Cable
-b- -
20.6. Control of Top Secret (TS) Keying Material
20.7. COMSEC Incidents
21. OPERATIONAL PROCEDURES
TR: 1D7X1Q Learning Program (Percipio); AFI 32-1065; American Public Works Association Policy and ANSI; MIL-STD 2000A; TOs 00-25-234; 31-1-141-1, 31-10-7;
31-10-11; 31-10-13, 31-10-24, and 31W3-10-20
21.1. Standard Maintenance Practices
21.2. Specialized Tools
TR: Applicable Technical Manuals
20.4. Physical Security Principles for Handling COMSEC Material
20.5. Destruction of COMSEC Material, Aids, and Equipment
1D7X1Q STS
10
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
21.2.1. Crimp Tool
-A- -
21.2.2. Use Crimp Tool
-b- -
22.1.1. Account Management
Systems
5 BB - -
22.1.2. Manage Computer Accounts
2b---
22.1.3. Account Types
A---
22.2.1. Add to Domain
5 2b b - -
22.2.2. Manage Security Groups
2b---
22.2.3. Manage Limited Access
Accounts
2b---
22.2.4.1. Principles
5 BB - -
22.2.4.2. Query Group Policies
-b- -
22.2.4.3. Apply Group Policy
2b---
22.3.1.1. Install and Configure
General Client Applications
2b---
22.3.1.2. Software Updates
5 BB - -
22.3.2.1. Install and Configure Anti-
virus Software and Virus Definitions
5 2b b - -
22.3.2.2. Harden Device
5 2b b - -
22.3.3.1. Install Specialized Client
Applications
2b---
22.3.3.2. Configure Specialized
Client Applications
2b---
22.3.3.3. Software Management
Policies
5 AB - -
22.2. Access Management
22.2.4. Group Policy
22.3. Applications
22.3.2. Cyber Hygiene
22.3.3. Specialized Software
22. SOFTWARE
TR: 1D7X1Q Learning Program (Percipio), MAJCOM / Local Procedures, Applicable Technical Publications, AFI 17-130, TO 00-33A-1202, AFNET Procedures, AFJQS
1D7XX- 200DR
22.3.1. Cyber Sustainment
22.4. System Recovery Troubleshooting
22.1. Account Management
1D7X1Q STS
11
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
22.4.1. Use Control Panel Functions
2b---
22.4.2. Use Computer Management
Tools
2b---
23.1.1. Add Device to Network
5 2b b - -
23.1.2. Configure Multifunction
Devices
2b---
23.1.3. Map Client System to
Network Device
5 2b b - -
23.2. Methods of Interfacing RF
Devices with IP Networks
AA - -
24.1. Radio Theory
AB - -
24.2. Radio Etiquette
A---
25.1. Conventional LMR Systems
5 -A- -
25.2. Trunked LMR Systems
5 -A- -
25.3. Enterprise LMR Systems
5 -A- -
25.4. LMR Systems Encryption
5 -A- -
25.5. Program LMRs
----
26.1. Principles, Capabilities, and
Limitations
----
27.1. Satellite System Segments
Principles, Capabilities, and
Limitations
AB - -
27.2. Line of Sight Microwave Radio
Systems Principles, Capabilities,
and Limitations
AB - -
27. SATELLITE COMMUNICATIONS (SATCOM)
TR: 1D7X1Q Learning Program (Percipio), CJCSI 6250.01, Applicable DISA Circulars, USSTRATCOM Wideband Standards and Operating Procedures
28. CABLE SPLICING
TR: 1D7X1Q Learning Program (Percipio); TOs 31W3-101-21, 31-10 Series; TO to Comm Std X-Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable% 20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
23. LOCAL AND NETWORKED SOLUTIONS
TR: 1D7X1Q Learning Program (Percipio); MAJCOM / Local Procedures; Applicable Technical Publications; AF e-Learning: Networking Fundamentals: Configuring
Wired and Wireless Networks and Firewalls, CompTIA A+ 220-1001: Configuring a Wired / Wireless Network, CompTIA A+ 220-1001: Networking, CompTIA A+ 220-
1001: Network Types
23.1. Network Connected Devices
24. STANDARD PRACTICES
TR: 1D7X1Q Learning Program (Percipio); AFI 32-1065; American Public Works Association Policy and ANSI; TOs 00-25-234, 31-10-7, 31-10-11, 31- 10-13, 31-10-24,
31-141-1, 31W3 10-20; MIL-STD 2000A
25. LAND MOBILE RADIO (LMR) TRANSMISSION SYSTEMS
TR: 1D7X1Q Learning Program (Percipio), Applicable TOs, Commercial Manuals
26. INSTALLATION NOTIFICATION AND WARNING SYSTEMS (GIANT VOICE)
TR: AFI 10-2501, Commercial Manuals
1D7X1Q STS
12
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
28.1. Modular Splicing System
AA - -
28.2. Plastic-Sheath Plastic-
Insulated Cable
AA - -
29.1. Theory of Fiber Optic
Lightwave Communication
5 AB - -
30.1. Principles of LAN / WAN
Distribution Systems
5 AB - -
30.2. Principles of Intra-Building
Wiring Distribution System
5 AB - -
31.1. Antenna Fundamentals
5 AB - -
31.2. Antenna Types and
Characteristics
5 AB - -
32.1. Confined Spaced
Fundamentals
5 AB - -
32.2. Confined Spaces Safety
5 AB - -
32.3. Confined Spaces Entry
Documentation
AB - -
32. CONFINED SPACES BASICS
TR: 1D7X1Q Learning Program (Percipio); AFI 91-203; TOs 31W3-10-21, 31-10-6, 31-10-13, 31-10-12, 31-10-3; TO to Comm Std X-Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
29. FIBER OPTICS
TR: 1D7X1Q Learning Program (Percipio), TO 31-10-34, TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-
%20Cable%20and%20Antenna% 20Systems/TO_to_Civilian_Std_X-Reference.xlsx
30. NETWORK DISTRIBUTION SYSTEMS
TR: 1D7X1Q Learning Program (Percipio); Commercial Manuals; ANSI/TIA-568 series, 569, 570, 606, 607; TIA-TSB 67, 72; AF e-Learning; TO 00-33D-3003; TO to
Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-
Reference.xlsx
31. ANTENNA SYSTEMS
TR: 1D7X1Q Learning Program (Percipio); TOs 31-1-141 Series, 31-10-14, 31R2-2GRC-1232, 31-10-3, 31R5-4-142-2; TO to Comm Std X-Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
1D7X1Q STS
13
Atch 4

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1.1. Duties of the AFS
A-B-
2.1. Title Authorities
AB - -
2.2. Title Authorities Application
AB - -
2.3. USCYBERCOM Structure
AB - -
2.4. AFCYBER Structure
AB - -
2.5. Cyber Protection Teams
AB - -
2.6. Cyber National Mission Force
AB - -
2.7. Preapproved Actions
AB - -
3.1. Functional Mission Analysis
Cyber (FMA-C)
BB - -
3.2. Structure
AB - -
3.3. Missions
AB - -
3.4. Offensive Cyberspace
Operations
AB - -
3.5. Defensive Cyberspace
Operations
AB - -
3.6. Exploitation
AB - -
3.7. Effects on Adversary Decision
Makers
AB - -
4.1. Define Non-Secure Networks
AB - -
4.2. Define Secure Networks
AB - -
4.3. Nuclear Command, Control,
and Communications Systems
AB - -
4.4. Space Systems
AB - -
4.5. Airborne Networks
AB - -
4.6. Battlefield Networks
AB - -
5.1. Risks,Threats, and
Vulnerabilities
AB - -
4. ENTERPRISE SYSTEMS / PROGRAMS
TR: 1D7X1M Learning Program (Percipio)
5. CYBER SECURITY
TR: 1D7X1M Learning Program (Percipio)
1. MISSION DEFENSE ACTIVITIES (MDA)
TR: 1D7X1M Learning Program (Percipio)
3. CYBER ENCLAVE
TR: 1D7X1M Learning Program (Percipio)
2. PUBLICATIONS AND DIRECTIVES
TR: 1D7X1M Learning Program (Percipio)
1. Implementation. This STS will be used for technical training provided by AETC for the 3-level course.
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
1D7X1M STS
1
Atch 5

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
5.2. Network Security
AB - -
5.3.1. Concepts
-B- -
5.3.2. Configure
2b---
5.3.3. Logging
AB - -
5.3.4. Rule Tracing
AB - -
5.3.5. Boundary Interaction Tools
BB - -
6.1. Packet Capture
BB - -
6.2. Principles of Packet Analysis
AB - -
6.3. Perform Packet Analysis
2b---
7.1. ACL
BB - -
7.2. Configure ACL
2b---
8.1. Services Concepts
AB - -
8.2. Processess Concepts
AB - -
8.3. DLL Concepts
AB - -
8.4. Registry Hive Concepts
AB - -
8.5. Monitor System Resources
AB - -
8.6. Identify Event Logging Tools
AB - -
8.7. Virtualization
AB - -
9.1. Infectious and Malicious
Software
BB - -
9.2. Registry Hive Concepts
AB - -
9.3. Identify Event Logging Tools
AB - -
10.1. ICS Concepts
BB - -
10.2. SCADA Concepts
BB - -
10. ICS AND SCADA
TR: 1D7X1M Learning Program (Percipio)
5.3. Firewalls
8. APPLIANCE (SERVER) DEFENSE
TR: 1D7X1M Learning Program (Percipio)
6. NETWORK FUNDAMENTALS
TR: 1D7X1M Learning Program (Percipio)
9. CLIENT SYSTEMS
TR: 1D7X1M Learning Program (Percipio)
7. SWITCHING AND ROUTING
TR: 1D7X1M Learning Program (Percipio)
1D7X1M STS
2
Atch 5

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
10.3. ICS / SCADA Protocols
AB - -
10.4. ICS / SCADA Vulnerabilities
AB - -
10.5. ICS / SCADA Attacks
AB - -
10.6. COINE - CE Monitoring
System
AB - -
11.1. OSI Reference Model
BB - -
11.2. Fundamentals of Protocols
BB - -
11.3. TCP / UDP Comparison
AB - -
11.4. Wireless Standards
AB - -
11.5. Ports
BB - -
11.6.1. Client Sockets
AB - -
11.6.2. Server Sockets
AB - -
11.7.1. Web Proxies
AB - -
11.7.2. Forward Proxy
AB - -
11.7.3. Reverse Proxy
AB - -
11.7.4. Anonymous Proxies
AB - -
11.7.5. Tunneling
AB - -
11.8. Protocols
BB - -
11.9. Services
BB - -
11.10.1. SSH
AB - -
11.10.2. SSL / TLS
AB - -
11.10.3. Secure FTP Versions
AB - -
11.10.4. HTTP / HTTPS
AB - -
11.10.5. PKI
BB - -
11.10.6.1. Concepts
AB - -
11.10.6.2. Install and Configure Air
Force Approved VPN
AB - -
11.10.6.3. Perform basic Network
Troubleshooting
AA - -
11.7. Proxy / Redirection
11.10. Secure Protocols
11. INTERNET PROTOCOL (IP) NETWORKING
TR: 1D7X1M Learning Program (Percipio)
11.10.6. Virtual Private Network (VPN)
11.6. Sockets
1D7X1M STS
3
Atch 5

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
11.10.6.4. Secure a VPN
AB - -
11.10.6.5. End-to-End Encryption
AB - -
11.10.6.6. Benefits
AB - -
11.10.6.7. Disadvantages
AB - -
11.10.6.8. End point Access
AB - -
11.10.6.9. Architecture
AB - -
12.1. Information Protections
Principles
AB - -
12.2. Rules of Engagement
BB - -
12.3. Assessment and Authorization
AB - -
12.4. Security Patch Implementation
BB - -
12.5. Malicious Logic Protection
AB - -
12.6. Deploy Security Patches
2b 2b - -
12.7. Intel Driven Patching
BB - -
13.1. Switches
BB - -
13.2. Routers
BB - -
13.3. VOIP
BB - -
13.4. Servers
BB - -
13.5. Clients
BB - -
14.1. Functions
AA - -
14.2. Base Roles
AA - -
14.3. NOS Roles
BB - -
14.4. Describe Assessment and
Authorizations Requirements
BB - -
14.5. Functions and Capabilities of
ACAS
AB - -
14.6. Review a Vulnerability Scan
AB - -
14.7. Identify Most Vulnerable
Systems
2b---
12. INFORMATION PROTECTION OPERATIONS
TR: 1D7X1M Learning Program (Percipio)
13. CONCEPTS AND IMPACTS OF STIGS WITHIN THE MDA ARENA
TR: 1D7X1M Learning Program (Percipio)
14. VULNERABILITY MANAGEMENT
TR: 1D7X1M Learning Program (Percipio)
1D7X1M STS
4
Atch 5

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
14.8. Vulnerability Remediation
BB - -
14.9. STIG Assessments
BB - -
14.10.1. Monitoring
BB - -
14.10.2. Analysis
BB - -
14.10.3. Remediation
BB - -
14.10.4. Reporting
BB - -
14.11.1. SDC Build Limitations
AB - -
15.1. Types and Characteristics
-B- -
15.2. Intrusion Detection Methods
AB - -
15.3. Intrusion Detection Tools
AB - -
16.1.1. Basic Commands /
Navigation
AB - -
16.1.2. Basic File Structure
AB - -
16.1.3. Linux Access Control
Models
AB - -
16.2.1. Basic Commands /
Navigation
AB - -
16.2.2. Role Based Access Controls
AB - -
16.3.1. Principles of VDI
Infrastructure
AB - -
17.1. Fundamentals
BB - -
17.2. Powershell
BB - -
17.3. Shells
AB - -
17.4. Scripting
BB - -
17.5. Build a Script Using
Powershell
2b---
16.3. Virtual Desktop Interface (VDI)
15. INTRUSION CONTROLS
TR: 1D7X1M Learning Program (Percipio)
16.2. Windows Operating Systems
16. SOFTWARE
TR: 1D7X1M Learning Program (Percipio)
17. SOFTWARE DEVELOPMENT
TR: 1D7X1M Learning Program (Percipio)
14.11. Standard Desktop Configuration (SDC)
16.1. Linux
14.10. Endpoint Security
1D7X1M STS
5
Atch 5

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
18.1. Development Repositories
AB - -
18.2. Repository Best Practices
AB - -
18.3. Software Development
Methodologies
AB - -
18.4. Stages of Software
Development
AB - -
18.5. Automation
BB - -
18.6. Automate Patch Deployment
2b---
19.1. Secure Coding Techniques
AB - -
20.1. Application Fuzzing
AA - -
20.2. Regresion Testing
AA - -
21.1. Software Diversity
AB - -
22.1. Principles of Database
Utilization
AB - -
22.2. Data Validation
AB - -
22.3. SQL Injection
AB - -
22.4. Code Injection
AB - -
22.5. Cross Site Scripting
AB - -
23.1. Networking RFCs
AB - -
23.2. Network Byte Order
AB - -
24.1. Network Management
Software
AB - -
24.2. SNMP v3
AB - -
18. SOFTWARE DEVELOPMENT PROCESS
TR: 1D7X1M Learning Program (Percipio)
22. DATABASE
TR: 1D7X1M Learning Program (Percipio)
23. ARCHITECTURE / NETWORKING
TR: 1D7X1M Learning Program (Percipio)
19. SOFTWARE SECURITY
TR: 1D7X1M Learning Program (Percipio)
24. NETWORKING AND NETWORK MONITORING
TR: 1D7X1M Learning Program (Percipio)
25. MITRE ATT&CK FRAMEWORK
TR: 1D7X1M Learning Program (Percipio)
20. SOFTWARE TESTING
TR: 1D7X1M Learning Program (Percipio)
21. SOFTWARE MAINTENANCE
TR: 1D7X1M Learning Program (Percipio)
1D7X1M STS
6
Atch 5

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
25.1. Principles of the ATT&CK
Framework
BB - -
25.2. Navigating the ATT&CK
Framework
BB - -
25.3. Understanding Analytics
BB - -
26.1. Principles of the Diamond
Model
AB - -
27.1. 7 Phases of a Cyber Attack
AB - -
28.1. Tools to Baseline Systems
(WMIC / Powershell)
AB - -
28.2. Data Types Captured From a
System
BB - -
28.3. Perform a System Baseline
2b---
29.1. Intelligence Sources
AB - -
29.2. Indicators of Compromise
AB - -
29.3. How to Leverage IOCs
BB - -
29.4. Pyramid of Pain
AB - -
29.5. Scan a System for IOCs from
Intel Product
2b - -
30.1. Foundations of a SEIM
AB - -
30.2. Sensors
AB - -
30.3. Log Sources
AB - -
30.4. Alerts
AB - -
30.5. Storage Considerations (Log
Rollover Rate)
AB - -
31.1. Incident Reponse
Methodologies
AB - -
31.2. SOPs
AB - -
26. DIAMOND MODEL OF INTRUSION ANALYSIS
TR: 1D7X1M Learning Program (Percipio)
31. INCIDENT RESPONSE
TR: 1D7X1M Learning Program (Percipio)
27. CYBER KILL CHAIN
TR: 1D7X1M Learning Program (Percipio)
28. BASELINE OF SYSTEMS METHODOLOGIES
TR: 1D7X1M Learning Program (Percipio)
29. CYBER INTELLIGENCE
TR: 1D7X1M Learning Program (Percipio)
30. SECURITY EVENT INFORMATION MANAGER (SEIM)
TR: 1D7X1M Learning Program (Percipio)
1D7X1M STS
7
Atch 5

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
31.3. Categorizing Events
AB - -
31.4. Roles and Procedures
AB - -
31.5. Reporting Chain
AB - -
31.6. Responding to an Incident
AB - -
31.7. Perform Incident Reponse
2b---
31.8. Reporting During / After an
Incident
AB - -
31.9. Perform Incident Reporting
2b---
1D7X1M STS
8
Atch 5

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1.1. Duties of AFS
ABB -
2.1. Climbing and Working Aloft
----
2.2. Radio Frequency Radiation
ABC-
2.3. DoD Electromagnetic
Environmental Effects (E3) Program
-AB-
2.4. Lightning Protection and
Grounding
A---
3.1. Metric Notation
AAA -
3.2. Decibel Math (Logarithmic
Power Calculation)
ABB -
3.3. Conduct Logarithmic Power
Calculation
2b---
3.4. Prefixes
AA - -
3.5. Fundamentals of Electricity
BBC-
3.6. Component and Device Theory
ABB -
3.7. Wave Generating Circuits
AA - -
3.8. Digital Circuits
AA - -
4.1. Wire Color Coding Standards
AAB -
4.2. Fiber Optic Cable
BB - -
4.3. Twisted Pair
AA - -
4.4. Coaxial Cable
BB - -
4.5. Shielding
AB - -
4.6. Labeling
ABB -
4.7. Build Ethernet Cable
2b---
4.8. Build Coax Cable
2b---
4.9. Coax Testing
AB - -
4.10. Perform Cable Testing
2b---
3. BASIC ELECTRONICS
TR: 1D7X1W Learning Program (Percipio)
1. EXPEDITIONARY COMMUNICATIONS
TR: 1D7X1W Learning Program (Percipio)
4. CABLE FUNDAMENTALS
TR: 1D7X1W Learning Program (Percipio)
2. SAFETY / RISK MANAGEMENT (RM)
TR: 1D7X1W Learning Program (Percipio); AFIs 32-1065, 90-802, 91-202; AFMAN 91-203; AFPAM 90-803; AFPD 91-2; MIL-STD 188-124B
1. Implementation. This STS will be used for technical training provided by AETC for the 3-level course.
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
1D7X1W STS
1
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
5.1.1.1. Enterprise Networks
BBC-
5.1.1.2. DISA Circuits
AAB -
5.1.1.3. Commercial ISPs
AAB -
5.1.2.1. LOS
AAB -
5.1.2.2. SATCOM
AAB -
5.1.2.3. Troposcatter
AAB -
6.1.1. Pre Placed Key (PPK)
AAB -
6.1.2. Firefly Vector Set
AAB -
6.2.1. Traffic Encryption Keys (TEK)
AAB -
6.2.2. Key Encryption Keys (KEK)
AAB -
6.2.3. TrKEK
AAB -
7.1.1. Transmitters
AA - -
7.1.2. Receivers
AA - -
7.1.3. Transceivers
AA - -
7.1.4. RF Transmission Mediums
ABC-
7.2.1. Understand Modulation
BBC-
7.2.2. Amplitude Modulation
BB - -
7.2.3. Frequency Modulation
BB - -
7.2.4. Digital Modulation
ABC-
7.3.1. Frequency Bands and
Characteristics
ABC-
5.1. Global Circuit and Transport Concepts
5.1.1. Terrestrial Transport Methods
6.2. Key Roles
7. RF TRANSMISSION FUNDAMENTALS
TR: 1D7X1W Learning Program (Percipio), AFI 36-2101, 1D7XX CFETP, AFECD
7.2. Modulation Techniques
7.3. RF Spectrum
7.1. Radio Theory
5. LONG HAUL COMMUNICATIONS CONCEPTS
TR: 1D7X1W Learning Program (Percipio)
5.1.2. Wireless Long Haul Fundamentals
6. ENCRYPTION / DECRYPTION
TR: 1D7X1W Learning Program (Percipio)
6.1. Crypto Keys
1D7X1W STS
2
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
7.3.2. Joint Spectrum Interference
Resolution (JSIR) Program
-AB-
7.3.3. Air Force Spectrum
Interference Resolution (AFSIR)
Program
-AB-
7.4.1. Radio Wave Propagation
Principles
BBC-
7.4.2. Refraction
AB - -
7.4.3. Reflection
AB - -
7.4.4. Diffraction
AB - -
7.4.5. Skywave Fundamentals
ABC-
7.5.1. Path Loss
AB - -
7.5.2. Atmospheric Attenuation
AB - -
7.5.3. Multipathing
AB - -
7.5.4. Free Space Loss
ABC-
7.5.5. Anomalous Propagation
ABC-
7.5.6. Solar Emissions and Effects
AB - -
8.1. Multimeter
2b B - -
8.2. Built-in Test Equipment
AA - -
8.3. Communication Systems
Analyzer
2b A - -
8.4. Dummy Load
AA - -
8.5. VSWR Tester
AA - -
8.6. Compass / Inclinometer
2b A - -
9.1.1. Fundamentals of Antenna
Propagation
BBC-
9.1.2. Antenna Gain
ABB -
9.1.3. Polarization
ABC-
9.1.4. Mutual Interference
ABB -
9.1.5. Impedance Matching
ABB -
7.4. Electromagnetic Wave Propagation Theory
8. TEST EQUIPMENT
TR: 1D7X1W Learning Program (Percipio)
9. ANTENNA FUNDAMENTALS
TR: 1D7X1W Learning Program (Percipio)
9.1. Antenna RF Propagation Theory
7.5. Signal Loss
1D7X1W STS
3
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
9.1.6. Deployable Antenna Types
AAB -
9.1.7. Beamwidth
AAB -
9.1.8. Calculate Electrical and
Physical Length
2b A - -
9.1.9. Relationship of Antenna
Height and Takeoff Angle
BB - -
9.2.1. Omnidirectional and
Directional Antennas
AB - -
9.2.2. Common Antenna Types
AB - -
9.2.3. Airborne Antenna
Applications
-AB-
9.2.4. Basic Antenna Tests
AA - -
9.2.5. Conduct Antenna Tests
2b---
9.2.6. Field Expedient Antenna
Concepts
BBB -
9.2.7. Construct Field Expedient
Antennas
2b---
10.1.1. Purpose
ABB -
10.1.2. Overview of Tactical Radios
A---
10.1.3. Radio Etiquette
B---
10.1.4. Practice Radio Etiquette
2b---
10.1.5. Signal Discipline Basics
ABC-
10.2.1. Capabilities and Limitations
ABC-
10.2.2. Controls and Indicators
A---
10.2.3. Operate the Transceiver
2b---
10.2.4. Perform Preventive
Maintenance Inspections
2b---
10.2.5. Troubleshoot
2b---
10.3.1. Capabilities and Limitations
ABC-
10.3.2. Controls and Indicators
A---
10.2. HF Transceiver Equipment
10.3. Tactical VHF / UHF Transceiver
9.2. Antenna Types and Applications
10. TACTICAL RADIO / SATCOM APPLICATIONS
TR: 1D7X1W Learning Program (Percipio), AFTTP(I) 3-2.27, Applicable Commercial Manuals
10.1. General Principles
1D7X1W STS
4
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
10.3.3. Operate the Transceiver
2b---
10.3.4. Perform Preventive
Maintenance Inspections
2b---
10.3.5. Troubleshoot
2b---
10.4.1. Capabilities and Limitations
ABC-
10.4.2. Controls and Indicators
A---
10.4.3. Operate the Transceiver
2b---
10.4.4. Perform Preventative
Maintenance Inspections
2b---
10.4.5. Troubleshoot
2b---
10.5.1.1. Frequency Hopping
ABC-
10.5.1.2. Spread Spectrum
AAB -
10.5.1.3. JTIDS / MIDS
-AB-
10.5.1.4. Tactical Data Links
AAB -
10.5.1.5. SADL
AAB -
10.5.2.1. Integrated Waveform
ABB -
10.5.2.2. ALE and 3G HF
ABB -
10.5.2.3. MUOS
ABB -
10.5.2.4. ANW2
AB - -
10.5.2.5. HPW
AB - -
10.5.2.6. Program Radio Using an
Advanced Waveform
2b---
11.1.1. Space Segment
AA - -
11.1.2. Command and Control
Segment
AA - -
11.1.3. Terminal (Ground) Segment
AA - -
11.2.1. IEEE and ITU Radio
Frequency Band Standards
AAB -
10.5. Battlefield Networks
10.5.2. Advanced Waveforms
11.1. Satellite System Segments Principles, Capabilities, and Limitations
10.4. UHF and Multiband TACSAT
11.2. Satellite Bands, Purpose, Capabilities, and Limitations
11. SATCOM FUNDAMENTALS
TR: 1D7X1W Learning Program (Percipio)
10.5.1. Jam Resistant Communications
1D7X1W STS
5
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
11.2.2. L, C, X, Ku, K, and Ka Band
applications and considerations
ABC-
11.3.1. FDMA
BBB -
11.3.2. TMDA
BBB -
11.3.3. CDMA
ABB -
11.4.1.1. Introduction to UHF, SHF,
EHF Terminals
AB - -
11.4.1.2. Multiband Satellite
Terminals
ABB -
11.4.2.1. Understand Phase
Modulation
BBC-
11.4.2.2. Types of Modulation
BBB -
11.4.2.3. Modulation Considerations
ABC-
11.4.2.4. Forward Error Correction
(FEC)
ABB -
11.4.3.1. Modems
AB - -
11.4.3.2. Transmitters
AB - -
11.4.3.3.1. Upconverter
AB - -
11.4.3.3.2. Block Upconverter
AB - -
11.4.3.4. Power Amplifier
AB - -
11.4.4.1. Receiver
AB - -
11.4.4.2. Low Noise Amplifier
AB - -
11.4.4.3. Low Noise Block
AB - -
11.4.4.4.1. Downconverter
AB - -
11.4.4.4.2. Block Downconverter
TR: subtask of 11.4.4.4
AB - -
11.4.4.5. Demodulator
AB - -
11.3. Satellite Access Principles
11.4.1. SATCOM Terminal Characteristics
11.4.3.3. Upconverters
11.4.4. Receive Systems
11.4.2. Phase Modulation
11.4.3. Transmit Systems
11.4.4.4. Downconverters
11.4. Current Satellite Constellations
1D7X1W STS
6
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
11.4.5.1. Antenna Systems
5 AB - -
11.4.5.2. Waveguides
5 AB - -
11.4.5.3. Feed Horns / Feed
Assemblies
5 AB - -
11.4.5.4. Acquisition and Tracking
Principles
5 AB - -
11.4.5.5. Calculate Satellite Look
Angles
2b---
11.4.5.6. Acquire and Track
Satellites
2b---
11.4.6.1. Principles, Capabilities,
and Limitations
ABC-
11.4.6.2. Controls and Indicators
A---
11.4.6.3. Operate a GPS Receiver
2b---
11.4.7.1. Perform Power Up / Down
Procedures
2b---
11.4.7.2. Configure Baseband
2b---
11.4.7.3. Perform Baseband
Equipment Ops Check
2b---
11.4.7.4. Configure Transmit and
Receive Equipment
2b---
11.4.7.5. Configure the Antenna
System
2b---
11.4.7.6. Configure the Control,
Monitor, and Alarm System
2b---
11.4.7.7. Timing and
Synchronization
ABC-
11.5.1.1. Satellite Database
AAB -
11.5.1.2. Satellite Access Request
(SAR)
AAB -
11.5.1.3. Gateway Access Request
(GAR)
AAB -
11.5.1.4. Submit SAR / GAR
----
11.4.5. Antenna Systems
11.4.7. Multiband Satellite Terminal Operations
11.5.1. Access Procedures
11.5.2. Communication Link Establishment and Maintenance
11.5. SATCOM Link Operations
11.4.6. Global Positioning System Receivers
1D7X1W STS
7
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
11.5.2.1. Principles
ABB -
11.5.2.2. Establish a
Communications Link
2b---
11.5.2.3. Counter Counter Measure
Principles
ABC-
11.5.2.4. Maintain Master Station
Logs
AAB -
11.5.2.5. Develop After Action
Reports
AAB -
11.5.3.1. SATCOM Link Reporting
-AB-
11.5.3.2. HAZCON Reports
-AB-
11.5.4.1. Understand TDMA
Architecture
ABB -
11.5.4.2. Understand Option Files
ABC-
11.5.4.3. Load Options File
2b---
11.5.4.4. Complete
Communications Link with a TDMA
Terminal
2b---
12.1. Uninterruptable Power
Supplies
AAB -
12.2. Batteries
AAB -
12.3. Inverters
AAB -
12.4. Filters
AAB -
12.5. Generators
AAB -
12.6. Considerations for Field
Application
ABC-
13.1. Methods of Interfacing RF
Devices with IP Networks
ABB -
13.2. Interface Selected RF
Equipment with an IP Network
2b---
13.3. Radio Over IP (ROIP)
Principles
ABB -
13. RF DEVICES TO IP NETWORKING AND IP RADIOS
TR: 1D7X1W Learning Program (Percipio)
11.5.4. TDMA Satellite Terminal Operations
12. ELECTRICAL POWER SYSTEMS
TR: 1D7X1W Learning Program (Percipio)
11.5.3. Reporting Requirements
13.4. Mesh Radio Networks
1D7X1W STS
8
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
13.4.1. Mobile At-hoc Network
(MANET) principles
BBC-
13.4.2. Establish MANET
Communications Links
2b---
14.1.1. Common Terminologies
AAB -
14.1.2. Applications
ABC-
14.1.3. Considerations
ABC-
14.1.4. LTE Bubbles
-AB-
14.2.1. Mobile Device Management
ABC-
14.2.2. User Management
-AB-
14.2.3. Mobile VPNs
ABB -
14.2.4. Connect through VPN
2b---
14.2.5. Application Installation
2b---
14.2.6. Application Management
-AB-
14.2.7. Mobile COP (Common
Operating Picture) Applications,
Devices and Servers
BBC-
14.2.8. Demonstrate Use of Tactical
Mobile Applications
2b---
15.1. Subnetting Principles
BBC-
15.2. Apply Subnetting Principles
2b---
15.3. WLAN Principles and
Protocols
BBB -
15.4. Configure WLAN (Wireless
IEEE 802.11)
2b---
16.1. Multicast
ABB -
16.2. Extending IP Traffic Over
Various Transports
BBB -
16.3. Demonstrate Wireless / Wired
IP Traffic Extension
2b---
15. INTERNET PROTOCOL (IP) NETWORKING (TACTICAL)
TR: 1D7X1W Learning Program (Percipio)
16. SWITCHING AND ROUTING (TACTICAL)
TR: 1D7X1W Learning Program (Percipio)
14.1. Cellular Principles
14. CELLULAR IP NETWORKS AND EQUIPMENT (GSM, LTE, CDMA)
TR: 1D7X1W Learning Program (Percipio)
14.2. Mobile Devices and Management
1D7X1W STS
9
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
17.1. 802.1X
-BB-
17.2. Implement 802.1X
----
17.3. Port Security
-B- -
17.4. PKI
-BB-
18.1. Virtualization
-BB-
18.2. Virtualized Server Admin
-BC-
18.3. Demonstrate Virtualized
Server Admin
----
18.4. Understand VOIP Call
Manager Principles
-BB-
19.1. Manage User Accounts
-BC-
19.2. Manage User Devices
-BC-
19.3. Execute User Account
Management
----
19.4. Execute Client Systems
Management
----
19.5. Add VOIP Phone to
CallManager
----
19.6. Hardware
-AB-
19.7. Software
-AB-
20.1.1. Integrate Various Tactical
Networks and Systems over
Transport
2b---
21.1.1. Describe Command Cyber
Readiness (CCRI) DISA
Requirements
-BB-
21.2.1. Emissions Control /
Signature Reduction
ABC-
17. NETWORK AUTHENTICATION FUNDAMENTALS
TR: 1D7X1W Learning Program (Percipio)
18. APPLIANCES (SERVERS)
TR: 1D7X1W Learning Program (Percipio)
19. CLIENT SYSTEMS
TR: 1D7X1W Learning Program (Percipio)
21.2. Expeditionary Security Concepts
21. CYBER SECURITY
TR: 1D7X1W Learning Program (Percipio); AFIs 10-701, 17-130, 16-1404; AFPD 10-7; AFMAN 17-1301
20. CYBER ENCLAVE
TR: 1D7X1W Learning Program (Percipio); AFPD 172; AFIs 17-201, 13-Series; JP 3-12; http://www.afcyber.af.mil; Joint Pub 6-0; CJCSIs 3231.01C, 6211.02D
21.1. Vulnerability Management
20.1. Enterprise Systems Integration
1D7X1W STS
10
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
21.2.2. Data Protection
ABC-
21.2.3. Process and Respond to
CCIRs
-AB-
22.1. Localized Interference
Resolution
ABC-
22.2.1. Electronic Attack (EA)
ABC
22.2.2. Electronic Protection (EP)
ABC
22.2.3. Electronic Warfare Support
(ES)
ABC
22.3. Spectrum Sensing
-AB-
22.4. Unit / AOR Comm Plans
(ANNEX K) PACE
ABC-
23.1.1. Joint Operations and
Battlestaff
ABC-
23.1.2. Joint Publications
AAB -
23.1.3. Military Planning Process
ABB -
23.1.4. OPORDs, FRAGORDs,
DEPORDs, and CONOPs
ABC-
23.1.5. JOPES
-AB-
24.1. General Expeditionary
Concepts
ABC-
24.1.1. Deployment Process
Overview
----
24.1.2. UTC Concepts
ABB -
24.1.3. Deployment Planning and
Execution
ABB -
24.1.4. Site Survey / Site Selection
Process
ABC-
24.1.5. Force Protection
ABB -
24.1.6. Understand TOC / AOC /
JOC Cyber Considerations
ABC-
24.1.7. Bandwidth Management
ABC-
22. ELECTROMAGNETIC SPECTRUM OPERATIONS
22.2. ELECTRONIC WARFARE (EW)
23. JOINT CONCEPTS
TR: 1D7X1W Learning Program (Percipio); AFI 13-Series; Joint Pub 6-0; CJCSIs 3231.01C, 6211.02D
23.1. Joint Operation Foundations
24. EXPEDITIONARY CONCEPTS
TR: 1D7X1W Learning Program (Percipio); AFIs 10-401, 10-403; AFMAN 171302-O; https://jkodirect.jten.mil/Atlas2/page/login/Login.jsf;
https://aefonline.afpc.randolph.af.mil/default.aspx; AMC myLearning Gateway (AF Fundamentals of Expeditionary Mobility Operations) & Deployable Comms CONOPS
(Uploaded)
1D7X1W STS
11
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
24.1. General Expeditionary
Concepts
ABC-
24.1.1. Deployment Process
Overview
----
24.1.2. UTC Concepts
ABB-
24.1.3. Deployment Planning and
Execution
ABB-
24.1.4. Site Survey / Site Selection
Process
ABC-
24.1.5. Force Protection
ABB-
24.1.6. Understand TOC / AOC /
JOC Cyber Considerations
ABC-
24.1.7. Bandwidth Management
ABC-
24. EXPEDITIONARY CONCEPTS
TR: 1D7X1W Learning Program (Percipio); AFIs 10-401, 10-403; AFMAN 171302-O; https://jkodirect.jten.mil/Atlas2/page/login/Login.jsf;
https://aefonline.afpc.randolph.af.mil/default.aspx; AMC myLearning Gateway (AF Fundamentals of Expeditionary Mobility Operations) & Deployable Comms CONOPS
(Uploaded)
1D7X1W STS
12
Atch 6

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1.1. Duties of the AFSC
A---
2.1.1. Multimeter
A---
2.1.2. Time Domain Reflectometry
----
2.1.3. Optical Time Domain
Reflectometry
B---
2.1.4. Bit Error Rate Testing
----
2.1.5. Spectrum Analyzer
----
2.1.6. Local Area Network (LAN)
Test Set
----
2.1.7. Network/Protocol Analyzer
(Sniffer)
----
2.1.8. Breakout Box
----
2.1.9. Fiber Optic Test Set (Light
Source)
----
2.2.1. Multimeter
----
2.2.2. Time Domain Reflectometer
(TDR)
----
2.2.3. Optical Time Domain
Reflectometer (OTDR)
----
2.2.4. Bit Error Rate Test Set
(BERT)
----
2.2.5. Spectrum Analyzer
----
2.2.6. Local Area Network (LAN)
Test Set
----
2.2.7. Network/Protocol Analyzer
(Sniffer)
----
2.2.8. Breakout Box
----
2.2.9. Fiber Optic Test Set (Light
Source)
----
2.3.1. Inventory/Accountability
Fundamentals
----
2.3.2. Maintenance Documentation
A---
2.2. Perform Maintenance using Test Equipment
1. NETWORK SYSTEMS OPERATIONS CAREER FIELD
TR: 1D7X1A Learning Program (AF e-Learning); AFI 36-2101; CFETP; AFECD
2. MAINTENANCE PRACTICES
TR: 1D7X1A Learning Program (AF e-Learning); TO 33K-1-100 and Applicable Test Equipment Technical Orders
2.3. Standard Maintenance Concepts
2.1. Test Equipment Theory
1. Implementation. This STS will be used for technical training provided by AETC for the 3-level course.
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
1D7XX/X STS (Legacy)
1
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
2.3.3. Installation Standards
A---
2.3.4. Inspections (PMI)
A---
2.4.1. Troubleshoot Network
Equipment (IP Data, Voice, Video,
----
2.4.2. Explain Land Line Concepts
----
2.4.3. Authorized Service
Interruptions (ASIs)
----
2.5.1. Fundamentals
B---
2.5.2. Verify Proper Grounding
(i.e.Equipment/Rack)
----
2.5.3. Bonding
----
2.5.4. Shielding
----
2.5.5. Lightning Protection
----
2.6.1. Fundamentals
A---
2.6.2. Circuit/Cable ID and Marking
A---
2.6.3. Color Coding Standards
A---
2.6.4. Physical Medium Standards
----
2.6.5. Patch Panels and
Termination Points
----
2.6.6. Device Physical
Interconnection
----
2.6.7. Demonstrate Proper Cable
Management Practices
----
2.7.1. Fundamentals
----
2.7.2. Terminate Copper Ethernet
Cable
----
2.7.3. Fiber Termination
----
2.8.1. Fundamentals
A---
2.8.2. Concepts
----
2.8.3. Handling, Packaging, and
Storing
----
2.4. Troubleshooting
2.6. Cable Installation/Management
2.8. Electrostatic Discharge (ESD)
2.5. Grounding
2.7. Cable Termination
1D7XX/X STS (Legacy)
2
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
3.1.1. Fundamentals
----
3.1.2. OSI Reference Model
----
3.1.3. Topologies
----
3.2.1. Fundamentals
----
3.2.2. Develop/Apply IP Addressing
Schema
----
3.2.3. Fundamentals of Protocols
----
3.2.4. Network Protocols
----
3.3.1. Network Virtualization
----
3.3.2. Software Defined Networking
----
3.4.1. Switching Application
----
3.4.2. Switching Standards
----
3.4.3. Configure Network Devices
----
3.4.4. Link Aggregation
----
3.5.1. Fundamentals
----
3.5.2. Protocol Application
----
3.5.3. Protocols/Standards
----
3.5.4. Configure Network Devices
----
3.5.5. Configure Protocols
----
3.5.6. VPN Concentrators
----
3.6.1. Fundamentals
----
3.6.2. Application
----
3.6.3. Administer
----
3.7.1. Fundamentals
----
3.6. VLANs
3.2. IPv4/IPv6 Addressing
3.1. Internetworking Basics
3.7. Spanning Tree (STP)
3. IP NETWORKING
TR: 1D7X1A Learning Program (AF e-Learning)
3.5. Layer 3 (Routing)
3.3. Enterprise Networking
3.4. Layer 2 (Switching)
1D7XX/X STS (Legacy)
3
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
3.7.2. Application
----
3.7.3. Configure
----
3.7.4. IEEE 802 Standards
----
3.8.1. Enterprise Wireless Network
Application
----
3.8.2. Enterprise Wireless
Protocols/Standards
----
3.8.3. Wireless Access Points
Application
----
3.8.4. Configure Wireless Access
Points
----
3.9.1. Fundamentals
----
3.9.2. DSCP Fundamentals
----
3.9.3. Configure
----
3.9.4. Redundancy Fundamentals
----
3.10.1. Network Management
Software
----
3.10.2. SNMP
----
3.10.3. Network Traffic Analysis
(sFlow, Netflow, jFlow)
----
3.10.4. Implement IP Network
Monitoring
----
3.10.5. Mobile Device Management
----
3.11.1. Application
----
3.11.2. Configure
----
4.1.1. Telephony Fundamentals
A---
4.1.2. Voice Over Internet Protocol
(VoIP)/ Voice Over Secure Internet
Protocol (VoSIP) Fundamentals
----
3.9. Quality of Service (QoS)
4. VOICE COMMUNICATIONS
TR: 1D7X1A Learning Program (AF e-Learning); Applicable Commercial Manuals
4.1. Telephony
3.8. Wireless Networking (WLAN)
3.10. IP Network Monitoring
3.11. Enterprise Logical Security
1D7XX/X STS (Legacy)
4
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
4.1.3. Plain Old Telephone System
(POTS)
----
4.1.4. Digital
--
4.1.5. Integrated Services Digital
Network (ISDN)
----
4.1.6. SIP/H.323
----
4.1.7. Voice/Video Compression
Standards
----
4.1.8. Configure VoIP Phone
----
4.2.1. Fundamentals
----
4.2.2. Configure
----
4.2.3. Customer Groups
----
4.2.4. Multilevel Precedence and
Preemption (MLPP)
----
4.2.5. Class of Service
----
4.2.6. Defense Switched Network
(DSN)
----
4.2.7. Translations
----
4.2.8. Configure Telephony
Features
----
4.2.9. Direct Inward Dialing (DID)
----
4.2.10. Caller ID
----
4.2.11. Video Teleconferencing
(VTC)
----
4.3.1. Concepts
----
4.3.2. Switch Security
----
4.3.3. 911/E-911
----
5.1.1. Fundamentals of IT
Documentation
----
5.1.2. Service Level Agreements
(SLAs)
----
5.1.3. Project Support Agreement
(PSA)
----
4.3. Telephony Switching
5. ENTERPRISE ADMINISTRATIVE FUNCTIONS
TR: 1D7X1A Learning Program (AF e-Learning)
5.1. Fundamentals of IT
4.2. Call Routing
5.2. Communications Network Trend Analysis
1D7XX/X STS (Legacy)
5
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
5.2.1. Identify
----
5.2.2. Analyze
----
5.3.1. Principles
A---
5.3.2. Red/Black
A---
5.3.3. Perform COMSEC Inventory
----
5.3.4. Perform Over the Air Rekey
(OTAR)
----
5.3.5. Perform Key Transfer Using
Common Fill Device
----
5.3.6. TEMPEST
----
6.1.1. Fundamentals
----
6.1.2. Configure/Use Serial Crypto
Equipment
----
6.1.3. Configure/Use IP Crypto
Equipment
----
6.2.1. Pre Placed Key (PPK)
----
6.2.2. Firefly Vector Set (FFVS)
----
7.1.1. Uninterrupted Power Supplies
(UPS)
A---
7.1.2. Facility Battery Backups
A---
7.1.3. Generators
A---
8.1.1. Modulation
----
8.2.1. Fundamentals
----
8.2.2. Timing
----
8.2.3. Signaling
----
5.3. Communications Security (COMSEC)
7. CRITICAL COMMUNICATIONS FACILITIES POWER SYSTEMS
TR: 1D7X1A Learning Program (AF e-Learning); Applicable Commercial Manuals
6.1. Crypto Devices
7.1. Power Systems
8.1. Long Haul Modulation
8.2. Multiplexing
6.2. Crypto Keys
8. LONG HAUL COMMUNICATIONS
TR: 1D7X1A Learning Program (AF e-Learning)
6. ENCRYPTION/DECRYPTION
TR: 1D7X1A Learning Program (AF e-Learning)
1D7XX/X STS (Legacy)
6
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
8.3.1. Concepts
----
8.3.2. Perform Patching
----
8.4.1. Contingency Planning &
Implementation
----
8.4.2. Develop
----
8.4.3. Communication
Requirements Process
----
8.4.4. Gateway Access
Request/Gateway Access
Authorization (GAR/GAA)
----
8.5.1. Responsibilities
----
8.5.2. Node Site Coordinator
----
8.5.3. Completion Reports
----
8.5.4. Circuit History Folders
A---
8.6.1. Procurement/ Change
Process
----
8.6.2. Telecommunications Service
Requests (TSRs)
----
8.6.3. Telecommunications Service
Order (TSOs)
----
8.6.4. Telecommunications Service
Priority (TSPs)
----
8.6.5. Command Communication
Service Designator (CCSDs)
----
8.7.1. Fundamentals
----
8.7.2. Use Tracking Software
----
9.1.1. Information Protection
Principles
----
9.1.2. Rules of Engagement
----
9.1.3. Assessment and
Authorization
----
9.1.4. Event Response
----
8.7. Maintenance Tracking Software
9.1. Security
8.5. Circuit Actions
8.4. Contingency Plans
8.6. Circuit
9. INFORMATION PROTECTION OPERATIONS
TR: 1D7X1A Learning Program (AF e-Learning)
8.3. Circuit Patching
1D7XX/X STS (Legacy)
7
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
9.1.5. Security Patch
Implementation
----
9.1.6. Malicious Logic Protection
----
9.2.1. Concept
A---
9.2.2. Steps
----
9.3.1. Principles
----
9.3.2. Firewalls
----
9.3.3. Intrusion Detection
----
9.3.4. Misuse Detection
----
9.3.5. Internal Control
----
9.3.6. Access Prevention
----
9.3.7. Authentication
----
9.3.8. Encryption
----
9.3.9. Network
Vulnerabilities/Mitigation
----
9.3.10. Voice Protection System
(VPS)
----
10.1.1. Establish IP Network
----
10.1.2. Establish Voice Network
----
11.1. Duties of AFSC
A---
12.1. Overview
A---
12.2. Capabilities
A---
13.1. Programming Languages
A---
13.2. Graphical User Interfaces
(GUI)
A---
13.3. Cross Domain Data Solutions
A---
9.2. Defense in Depth
13. INFORMATION TECHNOLOGY SYSTEMS FUNDAMENTALS
TR: 1D7X1B Learning Program (AF e-Learning)
10. EXPEDITIONARY COMMUNICATIONS CONCEPTS
TR: 1D7X1A Learning Program (AF e-Learning); MAJCOM/Local Procedures; Applicable Commercial Manuals
11. SYSTEMS OPERATIONS CAREER FIELD
TR: 1D7X1B Learning Program (AF e-Learning); AFH 33-337; AFIs 10-401, 33-100, 33-101, 33-115, 33-150; 36-2101; CFETP; AFECD
12. AFCYBER WEAPONS SYSTEMS
TR: 1D7X1B Learning Program (AF e-Learning)
9.3. Boundary Protection
10.1. Expeditionary Communications Connections
1D7XX/X STS (Legacy)
8
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
13.4. Memory Structure
A---
13.5. Interrupt Requests (IRQ)
A---
13.6. Drivers
A---
13.7. Basic Input/Output System
(BIOS)
A---
13.8. Memory
A---
13.9. Complementary Metal Oxide
Semiconductor (CMOS)
A---
14.1.1. Storage Types
B---
14.1.2. Configure System Storage
A---
14.1.3. I/O Technologies
----
14.1.4. Blade/Backplane
Technologies
A---
14.2.1. Concepts
B---
14.2.2. Server Virtualization
B---
14.2.3. Virtualization Environment
B---
14.2.4. Client Virtualization
B---
14.2.5. Implement Virtualization
----
14.3.1. Definition
----
14.3.2. Characteristics
----
14.3.3. Service Model Types
----
14.3.4. Deployment Models Types
----
14.3.5. Benefits
----
14.3.6. Implementation
Considerations
----
14.4.1. Enterprise Services
----
14.4.2. Ports, Protocols & Services
(PPS)
----
14. SERVERS
TR: 1D7X1B Learning Program (AF e-Learning)
14.4. Software
14.2. Virtualization Overview
14.1. Hardware
14.3. Cloud Computing
14.4.3. Operating Systems
1D7XX/X STS (Legacy)
9
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
14.4.3.1. Types and Characteristics
B---
14.4.3.2. PMO Systems
B---
14.4.3.3. Common Server Roles
2b---
14.4.3.4. Shell
2b---
14.4.3.5. Scripting
2b---
14.4.3.6. Basic Cmd Line Programs
2b---
14.4.3.7. Account Management
2b---
14.4.3.8. Hardening
2b---
14.4.3.9. Process Management
2b---
14.4.4.1. USAF Functional &
Mission Systems
----
14.4.4.2. Support Systems
----
14.4.4.3. Collaborative Tools
----
14.4.4.4. Server Management
Systems
----
14.4.4.5. Server Information
Protection
----
14.4.4.6. Remote Access
----
14.4.5.1. Flat File
----
14.4.5.2. Relational
----
14.4.5.3. NOSQL
----
14.4.5.4. Schema
----
14.4.5.5. SQL Query and Reports
----
14.4.6.1. Language Types
----
14.4.6.2. Web Services
----
14.4.6.3.1. Session Management
----
14.4.6.3.2. Secure Socket Layer
(SSL)
----
14.4.6.3.3. Transport Layer Security
(TLS)
----
14.4.6.3. Web Security
14.4.4. Applications
14.4.5. Database
14.4.6. Web Fundamentals
1D7XX/X STS (Legacy)
10
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
14.5.1. Backup/Restore Process
----
14.5.2. Offsite Storage
----
14.5.3. Continuity of Operations
(COOP)
----
14.5.4. Priority Restoration Plan
----
14.5.5. Alternate Power
----
14.5.6. Startup and Shutdown
Procedures
2b---
14.6. Service and Trouble
Management System
TR: AFJQS1D7XX-230T,
AFJQSXXXXX-212S
----
15.1. Overview
----
15.2. Definition
----
15.3.1. Components of Public Key
Infrastructure (PKI)
----
15.3.2. Biometrics
A---
15.3.3. Username/Password
A---
15.4. Network Addressing
A---
15.5. Systems Management
A---
15.6.1. Incident/Event Reporting
A---
15.6.2. Perform Incident Response
2b---
15.7.1. Monitor System Resources
2b---
15.7.2. Identify Event Logging Tools
----
16.1.1. Mission
----
16.1.2. Employment Concepts
----
14.5. Disaster/Contingency/ Operational/Crisis
15.6. Event Response
16. EXPEDITIONARY COMMUNICATIONS
TR: 1D7X1B Learning Program (AF e-Learning)
15.3. Network Authentication
15. NETWORKED SYSTEMS
TR: 1D7X1B Learning Program (AF e-Learning)
15.7. Network Operations (NetOps) Monitoring
16.1. Deployable Communications Systems Support (e.g.TDC)
1D7XX/X STS (Legacy)
11
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
16.1.3. Capabilities
----
16.1.4. Interfacing Considerations
----
16.2.1. Pre Deployment
----
16.2.2. Deployment
----
16.2.3. Establish Services
----
16.2.4. Extended Services
----
16.2.5. Re Deployment
----
16.2.6. Reconstitute
----
17.1. Types and Characteristics
B---
17.2. Boundary Interaction Tools
----
18.1.1. Functions
A---
18.1.2. Base Roles
----
18.1.3. NOS Roles
----
18.1.4. Describe Command Cyber
Readiness (CCRI) DISA
requirements
----
18.1.5. Describe Assessment &
Authorizations (A&A) Requirements
----
18.2.1. Functions and Capabilities
----
18.2.2. Review a Vulnerability Scan
2b---
18.2.3.1. STIG Viewer
----
18.2.3.2. Employing a STIG
----
18.2.3.3. STIG Compliance
Scanning Tool
----
18.2.4. Best Practice for VA Tools
----
18.2. Air Force Standard Vulnerability Assessment (VA) Tools
18.2.3. STIG Compliance Requirements
18.3. Patch Management
18. VULNERABILITY MANAGEMENT
TR: 1D7X1B Learning Program (AF e-Learning)
17. BOUNDARY INTERACTION
TR: 1D7X1B Learning Program (AF e-Learning)
18.1. Air Force Standard Vulnerability Assessment (VA)
16.2. TDC Deployment
1D7XX/X STS (Legacy)
12
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
18.3.1. Purpose
----
18.3.2. Client Install and Uninstall
----
18.3.3. Install Security Patches
----
18.3.4. Utilize Dashboard for
Reporting
----
19.1. Types and Characteristics
A---
19.2. Intrusion Detection Methods
B---
19.3. Intrusion Detection Tools
B---
19.4. Respond to an Incident
----
19.5.1. Functions
A---
19.5.2. Manage
----
19.6. Network Based Intrusion
Detection System Functions
A---
20.1. Hardware
----
20.2. OS and Applications
2b---
20.3. OS and Startup Problems
2b---
20.4. Network
2b---
21.1. Duties of the AFSC
A---
22.1. Publications
A---
22.2. Guidance Currency
A---
22.3. Cyber Taskings
A---
22.4. Collaborative Environments
A---
23.1. Roles and Responsibilities
----
23.2. Essential Components and
Factors of ICAM Program
A---
22. CYBER COLLABORATION, PUBLICATIONS, DIRECTIVES
TR: 1D7X1D Learning Program (AF e-Learning); AFI 33-360
19. INTRUSION CONTROLS
TR: 1D7X1B Learning Program (AF e-Learning)
19.5. End Point Protection
23. IDENTITY CREDENTIALING & ACCESS MANAGEMENT (ICAM)
TR: 1D7X1D Learning Program (AF e-Learning); AFMAN 17-1304 (in development)
21. SECURITY OPERATIONS CAREER FIELD
TR: 1D7X1D Learning Program (AF e-Learning); AFIs 17-130, 33-150, 36-2101; AFGM2018 1702; 1D7XX CFETP; AFECD
20. TROUBLESHOOTING
TR: 1D7X1B Learning Program (AF e-Learning)
1D7XX/X STS (Legacy)
13
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
24.1. Training and Resources
A---
24.2. End Point Security
A---
24.3. COMPUSEC Assessments
A---
25.1. Program Overview
A---
25.2. Air Force IT Category (AFI
driven)/DoD IT Types (DoD driven)
A---
25.3. Security Objectives
A---
25.4. Roles and Responsibilities
A---
25.5. System Development
Lifecycle
A---
25.6.1. RMF Step, PREPARE
System
A---
25.6.2. RMF Step, CATEGORIZE
System
A---
25.6.3. RMF Step, SELECT
Security Controls
A---
25.6.4. RMF Step, IMPLEMENT
Security Controls
A---
25.6.5. RMF Step, ASSESS
Security Controls
A---
25.6.6. RMF Step, AUTHORIZE
System
A---
25.6.7. RMF Step, MONITOR
Security Controls
A---
26.1. Overview
A---
26.2. Notice and Consent
A---
27.1. Introduction
A---
27.2. Risk Assessment
----
27.3. Risk Management
----
27.4. Sanitization
24. COMPUTER SECURITY (COMPUSEC)
TR: 1D7X1D Learning Program (AF e-Learning); AFI 17-130, AFMAN 171301, MPTO 00-33B-5006
25.6. RMF Methodology
26. CONSENT TO MONITORING FOR OFFICIAL IT RESOURCES
TR: 1D7X1D Learning Program (AF e-Learning); AFI 10-701
27. REMANENCE SECURITY
TR: 1D7X1D Learning Program (AF e-Learning); AFI 17-301, NSA Media Destruction Guidance: MPTO 00-33B-5006
25. RISK MANAGEMENT FRAMEWORK (RMF)
TR: 1D7X1D Learning Program (AF e-Learning); RMF Knowledge Service; AFI 17-101; DoD 8510.01; FIPS 199, 200; NSPs SP 800-53, 800-37, 800-53A, 800-60, 800-
64; CNSSI 1253
1D7XX/X STS (Legacy)
14
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
27.4.1. Unclassified Devices
A---
27.4.2. Classified Devices
A---
27.5. Media Reuse
A---
27.6. Disposal
A---
27.7. Mixed Media Devices
A---
27.8. Degauser Calibration and
Testing
----
28.1. Overview
A---
28.2. Roles and Responsibilities
A---
28.3. TEMPEST Information
Messages
A---
29.1. Assessment and Authorization
Tools
A---
29.2. Vulnerability Management
Tools
A---
30.1.1. Purpose
A---
30.1.2. Management Terms
A---
30.1.3. COMSEC Architecture
within the COMSEC Chain of
Command
----
30.1.4. COMSEC Material
Distribution
A---
30.1.5. Automated COMSEC
Programs
A---
30.2.1. KMI Operating Account
Manager (KOAM)
----
30.2.2. COMSEC
Accountants/COMSEC Clerks
A---
30.2.3. Role Exclusion
----
30.2.4. Account Personnel
Changeover
----
30.2. COMSEC Role Requirements/Responsibilities
28. TEMPEST PROGRAM MANAGEMENT
TR: 1D7X1D Learning Program (AF e-Learning); AFI 17-130; AFMANs 17-1305 Vol 1 (Unclass) & Vol 2 (Classified) (in development), 33-214 (Classified) (IACE:
http://intelshare.intelink.sgov.gov/sites/af_cybersecurity/SitePages/Home.aspx); Emission Security handbook; DISA Wireless STIG; MPTOs
00-33B-2861, 00-33B-2862, 00-33B-2863; AFSSIs 7700, 7702, 7703; TEMPEST Wiki: https://cs2.eis.af.mil/sites/10060/Wiki/TEMPEST.aspx
29. TOOLS
TR: 1D7X1D Learning Program (AF e-Learning)
30. COMMUNICATIONS SECURITY (COMSEC) MANAGEMENT
TR: 1D7X1D Learning Program (AF e-Learning); AFI 17-130, AFMAN 1-71302-O, TO 00-33-B-5001, AF COMSEC ACCOUNTING PROCEDURES, AFSSIs 3000-
series; DOC 042-12; CNSSIs 4003, 4004, 4005; DoDI 5210.82; CJCSIs 3260.01, 3260.02
30.1. Overview
1D7XX/X STS (Legacy)
15
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
30.3.1. Information Dissemination
Process
----
30.3.2.1. COMSEC Material
Request
----
30.3.2.2. COMSEC Material
Issuance
----
30.3.2.3. Record Maintenance and
Disposition
----
30.3.2.4. Request KMI Technical
Service Center (TSC) Support
----
30.3.2.5. COMSEC Equipment
Request
----
30.3.2.6. COMSEC Material
Replacement (Request, etc…)
----
30.3.2.7. Disposition Instructions for
Increase/Surplus Material
----
30.3.3.1. COMSEC Training
Program Management
----
30.3.3.2. AF Form 4168, COMSEC
Users Training
----
30.3.4. Additional Protection
Measures (Photography, Personal
Electronics, Public Display)
A---
30.3.5. Accounting Legend Codes
(ALC)
A---
30.3.6.1. Account Information Letter
----
30.3.6.2. Notification of Existence of
COMSEC Account Letter
----
30.3.7. In-Place Date
----
30.4.1. Purpose
A---
30.4.2. Program Management
----
30.5.1. Authorized Access
A---
30.4. Cryptographic Access Program (CAP)
30.5. Physical Security Principles for Handling COMSEC Material
30.3. Administration and Management of COMSEC Material
30.3.2. Procedures and Process Management
30.3.3. COMSEC Training Program
30.3.6. Account Management
1D7XX/X STS (Legacy)
16
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
30.5.2. Preventative Maintenance
Inspections (PMIs)
----
30.5.3. Protective Technologies
Overview
----
30.5.4. Physical Security Handling
Requirements
----
30.5.5. COMSEC Forms
A---
30.5.6. COMSEC Access List
A---
30.5.7. COMSEC Publication
Amendments
----
30.6.1. Disposition
A---
30.6.2. Destruction
B---
30.7.1. Safeguard and
Accountability
----
30.7.2. Transportation / Shipping
----
30.8.1. COMSEC No Lone Zone
Exceptions
A---
30.8.2. Two Person Integrity (TPI)
Handling Procedures
A---
30.8.3. TPI Material Storage
Requirements
A---
30.8.4. Tactical Situations Storage
Requirements
----
30.8.5. Transportation
Requirements for TPI
A---
30.10. COMSEC Keying Material
Transportation Requirements
----
30.11. Emergency Action Plans
(EAPs)
----
30.12.1. Introduction
----
30.12.2. Incident Types/ Concepts
----
30.12.3. Incident Reporting
----
30.12.4. Disposal of Material
Involved in a COMSEC Incident
----
30.9. COMSEC Nuclear Surety
30.12. COMSEC Incidents
30.6. Destruction of COMSEC Material, Aids and Equipment
30.7. Controlled Cryptographic Items (CCIs)
30.8. Control of Top Secret (TS) Keying Material
1D7XX/X STS (Legacy)
17
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
30.12.5. Report Submission
Process
----
30.13. COMSEC Audits
A---
30.14. Secure Voice Program
A---
31.1.1. Concepts
A---
31.1.2. Server Virtualization
A---
31.1.3. Virtualization Environment
A---
31.1.4. Client Virtualization
A---
31.2.1. Definition
----
31.2.2. Characteristics
----
31.2.3. Service Model Types
----
31.2.4. Deployment Models Types
----
31.2.5. Benefits
----
31.3.1. Types of Characteristics
A---
31.3.2. Scripting
A---
31.4.1. Flat File
----
31.4.2. Relational
----
31.4.3. NOSQL (Non-relational)
----
31.4.4. Schema
----
31.5.1. Language Types
----
31.5.2. Web Services
----
31.6.1. Session Management
----
31.6.2. Secure Socket Layer
----
31.7.1. Overview
----
31.7.2. Definition
----
31.3. Operating Systems Fundamentals
31.4. Database Fundamentals
31.5. Web Fundamentals
31.6. Web Security Fundamentals
31.7. Network/System Fundamentals
31. CYBER SYSTEMS FAMILIARIZATION
TR: 1D7X1D Learning Program (AF e-Learning); Skill Capability Pathfinder
31.1. Virtualization Fundamentals
31.2. Cloud Computing Fundamentals
1D7XX/X STS (Legacy)
18
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
31.7.3. Patch Management Purpose
----
31.7.4. Ports, Protocols & Services
----
31.8.1. Components of Public Key
Infrastructure (PKI)
----
31.8.2. Biometrics
A---
31.8.3. Username/Password
A---
31.8.4. Systems Management
----
31.9.1. Incident/Event Reporting
A---
31.10.1. Identify Event Logging
Tools
----
31.11.1. Functions
A---
31.11.2. Base Roles
----
31.11.3. NOS Roles
----
31.11.4. Describe Assessment and
Authorizations (A&A) Requirements
----
31.12.1. Types and Characteristics
A---
31.12.2. Intrusion Detection
Methods
A---
31.12.3. Intrusion Detection Tools
A---
31.12.4. Boundary Interaction Tools
----
31.13.1. Functions
A---
31.13.2. Network Based Intrusion
Detection System Functions
A---
32.1. Explain duties of AFSC
A---
31.13. End Point Protection Fundamentals
32. CLIENT SYSTEMS OPERATIONS CAREER FIELD
TR: 1D7X1E Learning Program (AF e-Learning); CFETP; AFECD
33. SAFETY/RISK MANAGEMENT (RM)
TR: 1D7X1E Learning Program (AF e-Learning); AFI 90-802; AFPAM 90-803
31.8. Network Authentication Fundamentals
31.9. Event Response Fundamentals
31.10. Network Operations (NetOps) Monitoring Fundamentals
31.11. Vulnerabilities Management Fundamentals
31.12. Intrusion Controls Fundamentals
1D7XX/X STS (Legacy)
19
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
33.1. Air Force Safety, Fire, and
Health Standards for AFSC
A---
33.2. Hazards of the AFSC
A---
34.1.1. Use Publications when
Performing Work
2b---
34.1.2. End User Support
2b---
34.1.3. TEMPEST
----
34.1.4. Wire Color-Coding
Standards
A---
34.1.5. Construct Copper Ethernet
Cable
----
34.1.6. Fiber Optics Concepts
----
34.1.7. Storage Media Sanitization
A---
34.1.8. Fundamentals of IT
Documentation
B---
34.1.9. Fundamentals of
Maintenance Documentation
----
34.2.1. Crimp Tool
----
34.2.2. Tone Generator
----
34.2.3. Inductive Amplifier
----
34.2.4. LAN Tester
----
34.2.5. Light Source
----
34.2.6. Use Crimp Tool
----
34.2.7. Use Networking Tools (i.e.,
LAN Tester, Cable Tester)
----
35.1.1. Purpose
A---
35.1.2. Pre-Installation
Requirements
A---
35.1.3. Operating System Image
Management
b---
34.2. Specialized Tools
TR: Applicable Technical Publications
35. SOFTWARE
TR: 1D7X1E Learning Program (AF e-Learning); MAJCOM/Local Procedures; Applicable Technical Publications
35.1. Windows Operating System (OS)
34. OPERATIONAL PROCEDURES
TR: 1D7X1E Learning Program (AF e-Learning); AFI 32-1065, American Public Works Association Policy and American National St; MIL STD 2000A; TOs 00-25-234-
WA-1; 31-1-141-1-WA-1; 31-10-7-WA-1; 31-10-11-WA-1; 31-10-13; 31-10-24-WA-1; and 31W3-10-20
34.1. Standard Maintenance Practices
1D7XX/X STS (Legacy)
20
Atch 7
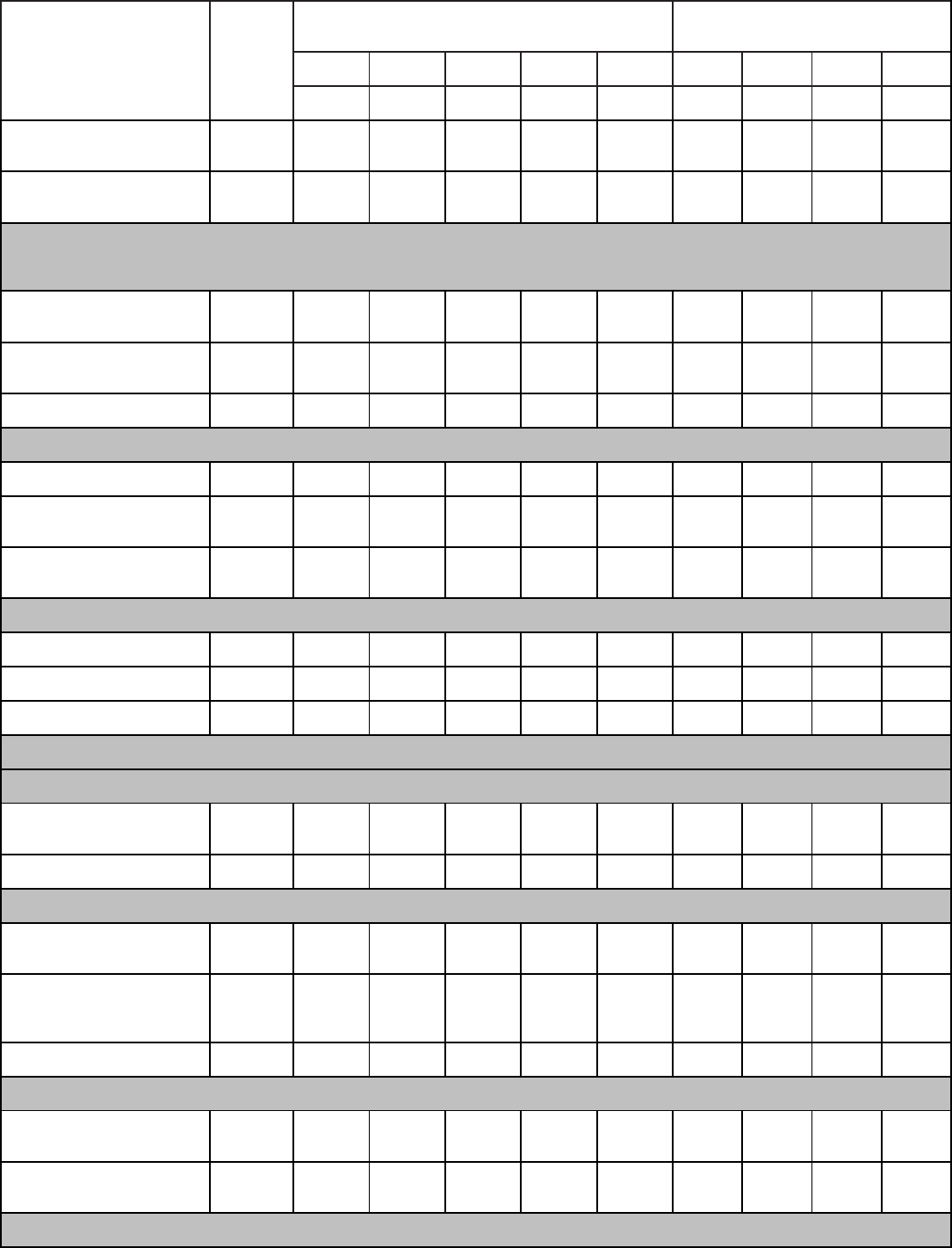
ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
35.1.4. Install Approved Workstation
Standard Image
2b---
35.1.5. Virtual Desktop Interface
(VDI)
----
35.2.1. Account Management
Systems
B---
35.2.2. Manage Computer Accounts
----
35.2.3. Account Types
----
35.3.1. Add to Domain
2b---
35.3.2. Manage Security Groups
----
35.3.3. Manage Limited Access
Accounts
----
35.3.4.1. Principles
B---
35.3.4.2. Query Group Policies
----
35.3.4.3. Apply Group Policy
----
35.4.1.1. Install and Configure
General Client Applications
2b---
35.4.1.2. Software Updates
B---
35.4.2.1. Cyber Vulnerability
Management
2b---
35.4.2.2. Install and Configure Anti-
virus Software and Virus Definitions
2b---
35.4.2.3. Harden Device
2b---
35.4.3.1. Install and Configure
Specialized Client Applications
B---
35.4.3.2. Software Management
Policies
A---
35.5. Mobile Devices
35.3.4. Group Policy
35.4. Applications
35.4.1. Cyber Sustainment
35.4.2. Cyber Hygiene
35.4.3. Specialized Software
35.2. Account Management
TR: AFI 17-130; TO 00-33A-1202;
AFNET Procedures; AFJQS 1D7XX- 200DR
35.3. Access Management
1D7XX/X STS (Legacy)
21
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
35.5.1. Cross-Platform Software
Solutions
B---
35.5.2. Mobile Device Management
B---
35.6.1.1. Backup Methods
B---
35.6.1.2. Recovery Methods
B---
35.6.1.3. Perform User Data Backup
----
35.6.2. Use Remote Tools
2b---
35.6.3. Powershell and Scripting
----
35.6.4. Use Control Panel Functions
2b---
35.6.5. Use Computer Management
Tools
2b---
36.1.1. Theory of Operation
B---
36.1.2. Major Components
B---
36.1.3. Peripheral Devices
----
36.2.1. Fundamentals
A---
36.2.2. Concepts
----
36.2.3. Handling, Packaging, and
Storing
----
36.3. Install Hardware in a Client
System
2b---
36.4. Troubleshooting Hardware
----
37.1. Network Theory
B---
37.2. Wireless Connectivity
B---
37.3. Configure Wireless Access
----
36.2. Electrostatic Discharge (ESD)
37. LOCAL & NETWORKED SOLUTIONS
TR: 1D7X1E Learning Program (AF e-Learning); MAJCOM/Local Procedures; Applicable Technical Publications; AF e-Learning CBTs: Networking
Fundamentals: Configuring Wired and Wireless Networks and Firewalls; CompTIA A+ 220-1001: Configuring a Wired/Wireless Network; CompTIA A+ 220-1001:
Networking; CompTIA A+ 220-1001: Network Types
35.6. Troubleshooting Software
35.6.1. System Recovery
36. HARDWARE
TR: 1D7X1E Learning Program (AF e-Learning); MAJCOM/Local Procedures; AF e-Learning CBT: A+ 220-1001: Installing Hardware and Display Components;
Commercial Manuals; Applicable Technical Publications
36.1. Client Systems
1D7XX/X STS (Legacy)
22
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
37.4.1. Add Device to Network
2b---
37.4.2. Configure Multifunction
Devices
----
37.4.3. Map Client System to
Network Device
2b---
37.5.1. Concepts
----
37.5.2. Install and Configure Air
Force Approved VPN
2b---
37.6. Troubleshooting Network
2b---
38.1. Duties of the AFSC
B---
38.2.1. Overview
B---
38.2.2. Responsibilities
B---
38.2.3. Leadership
B---
38.2.4. Continuity
B---
38.2.5. KMWG support (MAJCOM
and AF levels)
----
38.3.1. Sustained Roles
B---
38.3.2. Mobile Roles
B---
39.1.1. Purpose
----
39.1.2. People, Processes, and
Tools
----
39.1.3. Elicit User Requirements
----
39.1.4. Solutions Design, Build,
Test, and Deploy
----
39.2.1. Best Practice Identification /
Sharing
----
39.2.2. Change Management
----
39.2.3. Critical Thinking
----
38.2. Knowledge Management Center (KMC)
38.3. Roles and Responsibilities
39. KNOWLEDGE MANAGEMENT CORE COMPETENCIES
TR: 1D7X1K Learning Program (AF e-Learning); AFMAN 33-396
39.1. Operationalized Knowledge Management
39.2. Agile Learning
37.4. Network Connected Devices
37.5. Virtual Private Network (VPN)
38. KNOWLEDGE OPERATIONS CAREER FIELD
TR: 1D7X1K Learning Program (AF e-Learning); AFMAN 33-396; AFH 36-2618; AFECD
1D7XX/X STS (Legacy)
23
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
39.2.4. Knowledge Capture
----
39.2.5. Lessons Learned
----
39.3.1. 7-min Drills
----
39.3.2. Battle Rhythm Mapping /
Management
----
39.3.3. Decision Support Systems
----
39.3.4. Knowledge / Concept
Mapping
----
39.3.5. Meeting Management
----
39.4.1. Analytics
----
39.4.2. Expertise Tracking /
Marketing
----
39.4.3. Innovation Management
----
39.4.4. KM Assessments
----
39.4.5. Knowledge Engineering
----
39.4.6. Metrics and Measurement
----
39.4.7. Project Management
----
39.4.8. Roles / Responsibility
Capture (RACI)
----
39.4.9. Task Tracking
Methodologies
----
39.4.10. Work Methodology (agile,
Kanban, capture)
----
39.5.1. Establishment of KM Battle
Rhythm events
----
39.5.2. KM Doctrine
----
39.5.3. KM Fundamentals
----
39.5.4. KM Governance
----
39.5.5. KM Plan / Strategy
----
39.5.6. KM Roles
----
39.5.7. KM Training
----
39.5.8. Knowledge Worker Concept
----
39.3. Decision Cycle
39.4. Enhance Performance
39.5. KM Program Management
1D7XX/X STS (Legacy)
24
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
39.5.9. Leadership Endorsement /
Support
----
39.6.1. Brainstorming Methods
----
39.6.2. Collaboration Tools &
Environments
B---
39.6.3. Communication Plans
----
39.6.4. Communication Skills
----
39.6.5. Communities of Practice
(virtual/physical)
----
39.6.6. Content Management
----
39.6.7. Dashboards
----
39.6.8. Knowledge Dissemination
----
39.6.9. Portal Content Design
----
39.6.10. Social Business Platforms
----
39.6.11. Visualization of Information
----
40.1.1. Information Concepts
B---
40.1.2. Types of Services
B---
40.1.3. Standards
B---
40.2.1. Policy
----
40.2.2. Roles and Responsibilities
B---
40.2.3. Site Structure
B---
40.2.4. Identify Storage Parameters
B---
40.2.5.1. Elicit User Requirements
2b---
40.2.5.2. Evaluate User
Requirements
B---
40.2.5.3. Types
B---
40.2.5.4. Purpose
B---
40.1. Overview
40.2. SharePoint
40.2.5. Sites / Pages
39.6. Shared Understanding
40. ENTERPRISE INFORMATION SERVICES (EIS)
TR: 1D7X1K Learning Program (AF e-Learning); AFMAN 33-396; https://www.milsuite.mil/; https://www.usability.gov/about-us/index.html AF e- Learning SharePoint
2013 ISBN #9781118510711; SharePoint 2010 ISBN #9781118105054; AFJQS1D7XX-225S SharePoint
1D7XX/X STS (Legacy)
25
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
40.2.5.5. Create Sites
2b---
40.2.5.6. Delete Sites
2b---
40.2.5.7. Reset Site
2b---
40.2.5.8. Manage Site Layout
2b---
40.2.5.9. Create / Use Dashboards
2b---
40.2.6.1. Web Analytics
2b---
40.2.6.2. Activate Site Features
2b---
40.2.6.3. Activate Site Collection
Features
2b---
40.2.6.4. Site Collection Audit
2b---
40.2.6.5. Create Customized
Navigation
2b---
40.2.7.1. Establish Site Columns
----
40.2.7.2. Add Site Content Type
2b---
40.2.7.3. Manage Site Settings
2b---
40.2.7.4. Organize
2b---
40.2.8.1. Create Hierarchy
2b---
40.2.8.2. Create / Manage Users
2b---
40.2.8.3. Create / Manage Groups
2b---
40.2.9.1. Create Custom Content
Types
----
40.2.9.2. Add
2b---
40.2.9.3. Move
2b---
40.2.9.4. Delete
2b---
40.2.10.1. Create / Manage
Templates
2b---
40.2.10.2. Create a List
2b---
40.2.10.3. Modify Columns
2b---
40.2.10.4. Export
----
40.2.8. Permissions
40.2.9. Content (Files, graphics, excel files, links, graphics, calendars, etc.)
40.2.10. Lists
40.2.6. Site Actions
40.2.7. Galleries
1D7XX/X STS (Legacy)
26
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
40.2.10.5. Modify Form View
2b---
40.2.11.1. Create / Manage
Templates
2b---
40.2.11.2. Create a Document
Library
2b---
40.2.11.3. Force Check In / Check
Out a Document
2b---
40.2.11.4. Manage Version Control
2b---
40.2.11.5. Set Alerts
2b---
40.2.12.1. Manage
----
40.2.12.2. Create a Standard
2b---
40.2.12.3. Create a Data Sheet
2b---
40.2.12.4. Create / Manage Filters
2b---
40.2.12.5. Use Conditional
Statements
----
40.2.13.1. Purpose
B---
40.2.13.2. Create / Use Workflows
2b---
40.2.13.3. Manual / Automatic
Activation
2b---
40.2.13.4. Out of the Box Workflows
----
40.2.13.5. Associate Workflows to
Lists
----
40.2.13.6. Associate Workflows to
Libraries
----
40.2.14.1. Uses
B---
40.2.14.2. Managing Web/App
Parts
----
40.2.15.1. Recover From Recycle
Bin
2b---
40.2.15.2. Recover From Site
Collection Recycle Bin
B---
40.2.13. Workflow
40.2.14. Web Parts/App Parts
40.2.15. Item Recovery
40.2.11. Library
40.2.12. Views
1D7XX/X STS (Legacy)
27
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
40.2.16. Translate Excel / Access
Features
----
40.2.17.1.1. Customize Content
Types
----
40.2.17.1.2. Implement Custom
Content Types
----
40.2.17.2.1. Access Data Sources
----
40.2.17.2.2. Modify a Data Source
in
Data View
----
40.2.17.3.1. Implement the
Workflow Platform
----
40.2.17.3.2. Design a Workflow
----
40.2.17.4.1. Design Workflows with
Visio
----
40.2.17.4.2. Transfer a Visio
Workflow Design to SharePoint
Designer
----
40.2.17.4.3. Publish a Visio
Workflow Design Using SharePoint
Designer
----
40.2.17.5.1. Package Workflows
----
40.2.17.5.2. Deploy Workflow
Packages
----
40.2.17.5.3. Create Impersonation
Steps
----
40.2.17.5.4. Create Action
Statements
----
41.1.1. About
B---
41.1. Hypertext Markup Language Code (HTML)
40.2.17.2. Integrating Data Sources Using SharePoint Designer
40.2.17.3. Creating Workflows with the Workflow Platform
40.2.17.4. Creating Workflows with SharePoint Designer and Visio
40.2.17.5. Packaging and Deploying Workflows
41. WEB DEVELOPMENT
TR: 1D7X1K Learning Program (AF e-Learning); http://www.w3.org/standards/webdesign/; https://www.w3.org/WAI/intro/accessibility.php; https://www.usability.gov/; AF
e-learning Web Design for Dummies ISBN #9781118004906; https://www.w3schools.com/tags/default.asp; https://www.w3schools.com/html/default.asp; AF e-Learning
HTML & CSS ISBN #9780071496292; https://www.w3schools.com/css/default.asp; https://www.w3schools.com/cssref/default.asp;
https://www.w3schools.com/css/css_intro.asp; https://www.w3schools.com/js/; AF e-Learning JavaScript Essentials Library ID: sl_jsce_a01_it_enus
40.2.17. SharePoint Designer
40.2.17.1. Customizing and Implementing Content Types
1D7XX/X STS (Legacy)
28
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
41.1.2. Best Practices
B---
41.1.3. HTML Structure
2b---
41.1.4. Create Elements, Attributes,
Headlines and Paragraphs
2b---
41.1.5. Use Styles
2b---
41.1.6. Use Formatting Elements
2b---
41.1.7. Add Links
2b---
41.1.8. Use Images
2b---
41.1.9. Add Tables
2b---
41.1.10. Create Lists
2b---
41.1.11. Create Hyperlinks
2b---
41.1.12. Create Marquee
2b---
41.1.13. Add Email Links
2b---
41.1.14. Add Comments
2b---
41.1.15. Resources
B---
41.1.16. JavaScript
----
41.2.1. About
----
41.2.2. Syntax
----
41.2.3. Selectors
----
41.2.4. 3 ways to insert Cascading
Style Sheet
----
41.2.5. Work with Colors
----
41.2.6. Work with images
----
41.2.7. Box Model
----
41.2.8. Use Height and Width
Modifications
----
41.2.9. Use Auto Value
----
41.2.10. Use Text Modification
----
41.2.11. Use Icons & Stylesheets
----
41.2.12. Add Commenting
----
41.2.13. Resources
----
41.2. Cascading Style Sheets
42. CLIENT SYSTEMS FAMILIARIZATION
TR: 1D7X1K Learning Program (AF e-Learning); AFI 17-130; TO 00-33A-1202; AFNET Procedures; AFJQS1D7XX-200DR; Skill Capability Pathfinder
42.1. Account Management Fundamentals
1D7XX/X STS (Legacy)
29
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
42.1.1. Account Management
Systems
B---
42.1.2. Manage Computer Accounts
----
42.1.3. Account Types
----
42.2.1. Add to Domain
B---
42.2.2. Manage Security Groups
----
42.2.3. Manage Limited Access
Accounts
----
42.3.1. Principles
B---
42.3.2. Query Group Policies
----
42.3.3. Apply Group Policy
----
43.1.1. Types and Characteristics
B---
43.1.2. Common Server Roles
B---
43.1.3. Basic Cmd Line Programs
B---
43.1.4. Account Management
B---
43.1.5. Hardening
B---
43.1.6. Process Management
B---
43.2. Incident/Event Reporting
B---
43.3.1. Functions and Capabilities
----
43.3.2. Review Vulnerability Scan
B---
43.4.1. Use STIG Viewer
----
43.4.2. Apply STIG
----
43.4.3. Use STIG Compliance
Scanning Tool
----
43.5. Describe Best Practices for
Vulnerability Assessment Tools
----
42.3. Group Policy Fundamentals
43. CYBER SYSTEMS FAMILIARIZATION
TR: 1D7X1K Learning Program (AF e-Learning); Skill Capability Pathfinder
43.1. Operating Systems Fundamentals
43.3. AF Standard Vulnerability Assessment (VA) Tools Fundamentals
43.4. STIG Compliance Requirements Fundamentals
42.2. Access Management Fundamentals
1D7XX/X STS (Legacy)
30
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
43.6.1. Purpose
----
43.6.2. Client Install and Uninstall
----
43.6.3. Install Security Patches
----
43.6.4. Utilize the Dashboard for
Reporting
----
44.1. Explain duties of AFSC
A---
45.1. Air Force Safety, Fire, and
Health Standards for AFSC
A---
45.2. Hazards of the AFSC
A---
45.3.1. Maintenance Actions
----
45.3.2. Energized Equipment
A---
45.3.3. High Voltage Equipment
----
45.3.4. Radio Frequency (RF)
Hazard Environments
A---
45.4.1. Use
2b---
45.4.2. Maintain
----
45.4.3. Inspect
----
45.5. Perform General
Housekeeping
----
46.1.1. Calculate Powers of Ten
----
46.1.2. Electrical Prefixes
----
46.2.1. Ohm’s Law and its
Applications
----
46.2.2. Identify and Interpret Basic
Electrical Symbols and Drawings
----
46.2.3. Current
----
46. ELECTRONIC PRINCIPLES
TR: TO 31-1-141-2WA-1 Ch.7, 9, and 10
46.1. Metric Notation
46.2. Fundamentals of Electricity
43.6. Patch Management Fundamentals
44. RF TRANSMISSION OPERATIONS CAREER FIELD
TR: AFI 36-2101; CFETP; AFECD
45. SAFETY/RISK MANAGEMENT (RM)
TR: AFI 48-109; AFI 90-802; AFI 91-202; AFMAN 91-203; TO 31Z-10-4
45.3. Practice Safety Precautions
45.4. Safety and Personal Protective Equipment
1D7XX/X STS (Legacy)
31
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
46.2.4. Voltage
----
46.2.5. Resistance
----
46.2.6. Inductance
----
46.2.7. Capacitance
----
46.2.8. Power
----
46.3.1. Theory
----
46.3.2. Applications
----
46.4.1. Theory
----
46.4.2. Applications
----
46.5.1. Transformers
----
46.5.2. Resistors
----
46.5.3. Capacitors
----
46.5.4. Inductors
----
46.5.5. Relays/solenoids
----
46.5.6. Diodes
----
46.5.7. Transistors
----
46.5.8. Integrated Circuit
----
46.6.1. Kirchhoff's Law
----
46.6.2. Series Circuits
----
46.6.3. Parallel Circuits
----
46.7.1. Oscillators
----
46.7.2. Transistor Amplifier Circuits
----
46.8.1. Theory
----
46.8.2. Applications
----
47.1. Use Publications when
Performing Work
2b---
46.5. Component and Device Theory
46.6. Electronic Circuits
46.7. Wave Generating Circuits
46.8. Digital Circuits
47. STANDARD PRACTICES
TR: AFI 32-1065, American Public Works Association Policy and American National St; TOs 00-25-234-WA-1, 31-10-7-WA-1, 31-10-11-WA-1, 31- 10-13-WA-1, 31-10-
24-WA-1, 31-141-1-WA-1 series, 31W3 10-20, MIL-STD 2000A
46.3. Direct Current
46.4. Alternating Current
1D7XX/X STS (Legacy)
32
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
47.2. Installation
----
47.3. Configuration
----
47.4. Interconnection
----
47.5. Inspection
----
47.6. TEMPEST Suppression
Techniques
----
47.7.1. Cabling
----
47.7.2. Installation
----
47.8. Wire Color Coding Standards
----
47.9. Fiber Optics Installation
Concepts
----
47.10. Twisted pair Cable
----
47.11. Coaxial Cables
----
47.12. Fiber Optic Cable
----
47.13. Interfacing Considerations
(e.g.TRI TAC, Pinouts, Signal
Format)
----
47.14. Shielding
----
47.15. Lightning Protection
A---
47.16.1. Install
----
47.16.2. Remove
----
47.16.3. Perform Inspection
----
47.16.4. Perform Maintenance
----
47.17.1. Identify
----
47.17.2. Mark
----
47.18.1. Visual Inspection
----
47.18.2. Basic Troubleshooting
Techniques
B---
48.1.1. Optical Time Domain
Reflectometer
----
48.1. Test Equipment Theory
47.7. Documentation
47.16. Equipment Grounding and Lightning Protection
47.17. Underground Utilities
47.18. Equipment Familiarization
48. TEST EQUIPMENT
TR: Applicable Test Equipment Technical Orders; TO 33K-1-100-1
1D7XX/X STS (Legacy)
33
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
48.1.2. Time Domain Reflectometer
----
48.1.3. Bit Error Rate Test Set
A---
48.1.4. Frequency Counter
----
48.1.5. Network/Protocol Analyzer
----
48.1.6. Spectrum Analyzer
A---
48.1.7. Power Meter
----
48.1.8. Insulation Test Set
----
48.1.9. Megaohmeter
----
48.1.10. Built in Test Equipment
----
48.1.11. Breakout Box
----
48.1.12. Communications System
Analyzer/Communications Service
Monitor
----
48.1.13. Sweep Generator
----
48.1.14. RMS Voltmeter
----
48.1.15. Distortion Analyzer
----
48.1.16. Wattmeter
----
48.1.17. Dummy Load
----
48.1.18. Audio Oscillator
A---
48.1.19. Infrared Tester
----
48.1.20. Earth Ground Tester
A---
48.1.21. Wavemeter
----
48.1.22. VSWR Tester
----
48.2.1. Optical Time Domain
Reflectometer
----
48.2.2. Time Domain Reflectometer
----
48.2.3. Bit Error Rate Test Set
2b---
48.2.4. Frequency Counter
----
48.2.5. Network/Protocol Analyzer
----
48.2.6. Spectrum Analyzer
2b---
48.2.7. Power Meter
----
48.2.8. Insulation Test Set
----
48.2. Equipment Maintenance using Test Equipment
1D7XX/X STS (Legacy)
34
Atch 7
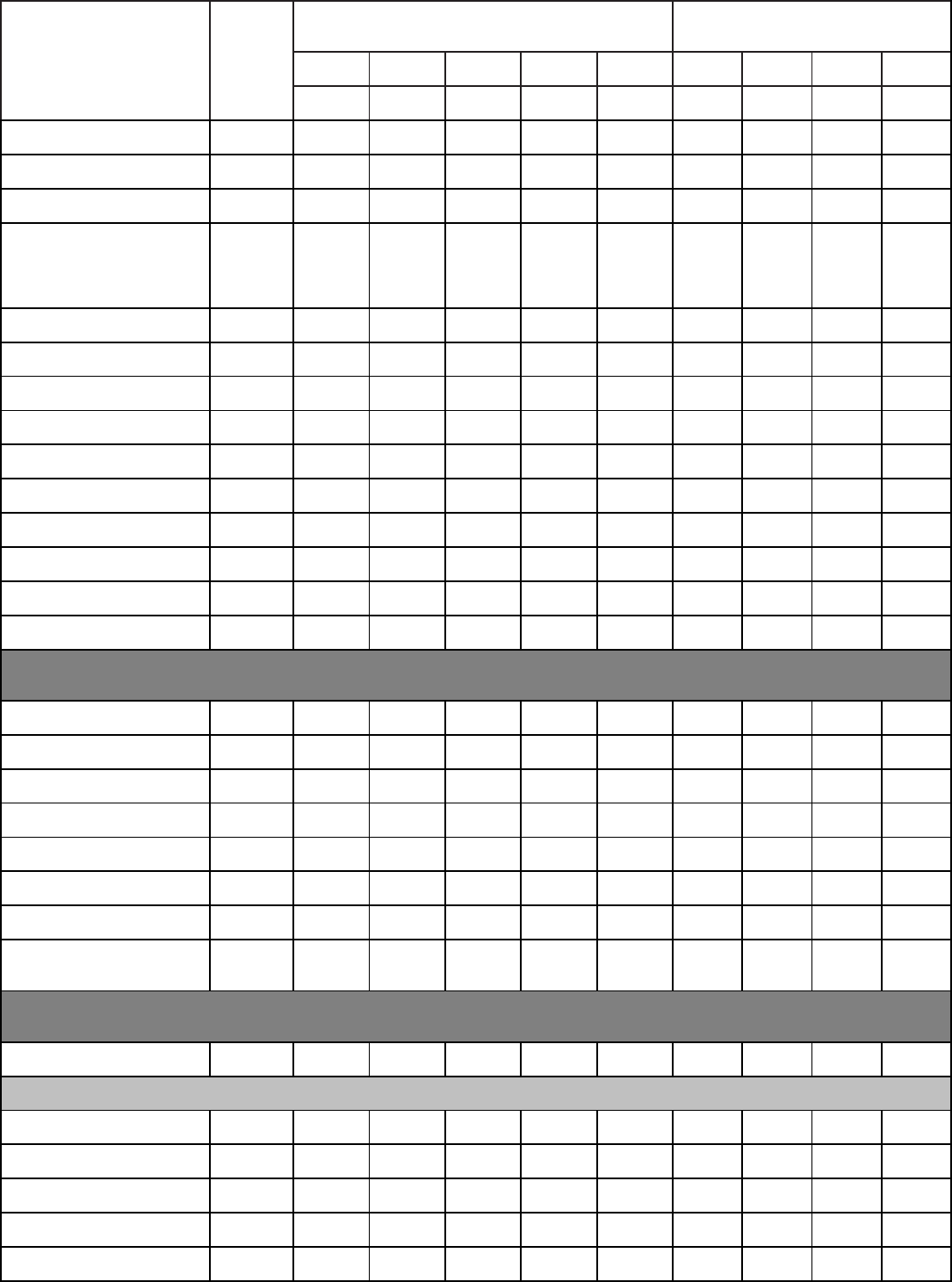
ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
48.2.9. Megaohmeter
----
48.2.10. Built in Test Equipment
----
48.2.11. Breakout Box
----
48.2.12. Communications System
Analyzer/Communications Service
Monitor
2b / - - - -
48.2.13. Sweep Generator
----
48.2.14. RMS Voltmeter
----
48.2.15. Distortion Analyzer
----
48.2.16. Wattmeter
----
48.2.17. Dummy Load
----
48.2.18. Audio Oscillator
----
48.2.19. Infrared Tester
----
48.2.20. Earth Ground Tester
2b---
48.2.21. Wavemeter
----
48.2.22. VSWR Tester
----
49.1. Amphenol Tool
----
49.2. Tone Generator
----
49.3. Inductive Amplifier
----
49.4. LAN Tester
----
49.5. Light Source
----
49.6. Transit
----
49.7. Fusion Splicer
----
49.8. Fiber Optic Source and Meter
----
50.1. Digital Communications
----
50.2.1. Transmitters
----
50.2.2. Receivers
----
50.2.3. Transceivers
----
50.3. RF Transmission Mediums
----
50.4. Modulation Techniques
----
49. SPECIALIZED TOOLS
TR: Applicable Technical Publications
50. BASIC COMMUNICATIONS THEORY
TR: TO 31-1-141-2WA-1 Ch.7, 9, and 10
50.2. Radio Theory
1D7XX/X STS (Legacy)
35
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
50.5. Radio Etiquette
----
50.6. Practice Radio Etiquette
----
50.7.1. Frequency Bands and
Characteristics
----
50.7.2. Joint Spectrum Interference
Resolution (JSIR) Program
----
50.7.3. Air Force Spectrum
Interference Resolution (AFSIR)
Program
----
50.8.1.1. Refraction
----
50.8.1.2. Reflection
----
50.8.1.3. Diffraction
----
50.8.1.4. Skywave Fundamentals
----
50.8.2.1. Path Loss
----
50.8.2.2. Atmospheric Attenuation
----
50.8.2.3. Multipathing
----
50.8.2.4. Free Space Loss
----
50.8.2.5. Anomalous Propagation
----
50.8.2.6. Solar Emissions and
effects
----
51.1.1. Dipole
----
51.1.2. Whip
----
51.1.3. Longwire
----
51.1.4. Horn
----
51.1.5. Helical
----
51.1.6. Parabolic
----
51.1.7. Array
----
51.2. Antenna Efficiency
----
51.1. Common Antennas
50.7. RF Spectrum
50.8. Electromagnetic Wave Propagation Theory
50.8.1. Radio Wave Propagation
50.8.2. Signal Loss
51. ANTENNA PRINCIPLES
TR: TO 31-1-141-12
1D7XX/X STS (Legacy)
36
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
51.3. Antenna Waves
----
51.4. Antenna Site Selection and
Configuration
----
51.5. Mutual Interference
----
51.6. Antenna Gain
----
51.7. Impedance Matching
----
51.8. Resonant & Non Resonant
Antennas
----
51.9. Law of Reciprocity
----
51.10. Polarization
----
51.11. Relationship of Antenna
Height and Take Off Angle
----
51.12. Calculation of Electrical
Length
----
51.13. Calculation of Physical
Length
----
51.14. Beamwidth
----
51.15.1. Deployable Antennas
----
51.15.2. Deployable Antenna Masts
----
51.15.3. Erect Selected Deployable
Antenna Masts and Antennas
----
51.16.1. Effects of Flight on
Antenna Propagation
----
51.16.2. Antenna Configuration On
Airframes
----
52.1.1. Capabilities and Limitations
----
52.1.2. Controls and Indicators
----
52.1.3. Function of Modules
----
52.1.4. Operate the HF Transceiver
----
52.1.5. Perform Preventive
Maintenance Inspection
----
52.1.6. Troubleshoot
----
51.15. Deployable Antenna Equipment
51.16. Airborne Antenna Applications
52. TACTICAL RADIO APPLICATIONS
TR: AFTTP(I) 3-2.27, Applicable Commercial Manuals
52.1. High Frequency (HF) Transceiver Equipment
1D7XX/X STS (Legacy)
37
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
52.1.7.1. HFGCS
----
52.1.7.2. Automatic Link
Establishment (ALE)
----
52.2.1. Capabilities, Configurations,
and Limitations
----
52.2.2. Controls and Indicators
----
52.2.3. Function of Modules
----
52.2.4. Operate the Transceiver
----
52.2.5. Perform Selected Preventive
Maintenance Inspections (PMIs)
----
52.2.6. Troubleshoot
----
52.2.7.1. UHF Follow-on/TACSAT
Purpose, Capabilities, and
Limitations
----
52.2.7.2. UHF TACSAT Transceiver
----
52.2.7.3. Control and Indicator
Functions
----
52.2.7.4. Operate the UHF TACSAT
Transceiver
----
52.3.1.1. Frequency Hopping
----
52.3.1.2. Spread Spectrum
----
52.3.1.3. Joint Tactical Information
Distribution System
(JTIDS)/Multifunctional Information
Distribution System (MIDS)
----
52.3.2. Tactical Data Links (TDLs)
----
52.3.3. Situation Awareness Data
Link (SADL)
----
52.3.4. Enhanced Position Location
Reporting System (EPLRS)
----
52.3.5.1. Integrated Waveform (IW)
----
52.3.5. Advanced Waveforms
52.1.7. Survivable HF Communications
52.2. Tactical VHF/UHF Transceiver
52.2.7. UHF TACSAT
52.3. Battlefield Networks
52.3.1. Jam Resistant Communications
1D7XX/X STS (Legacy)
38
Atch 7
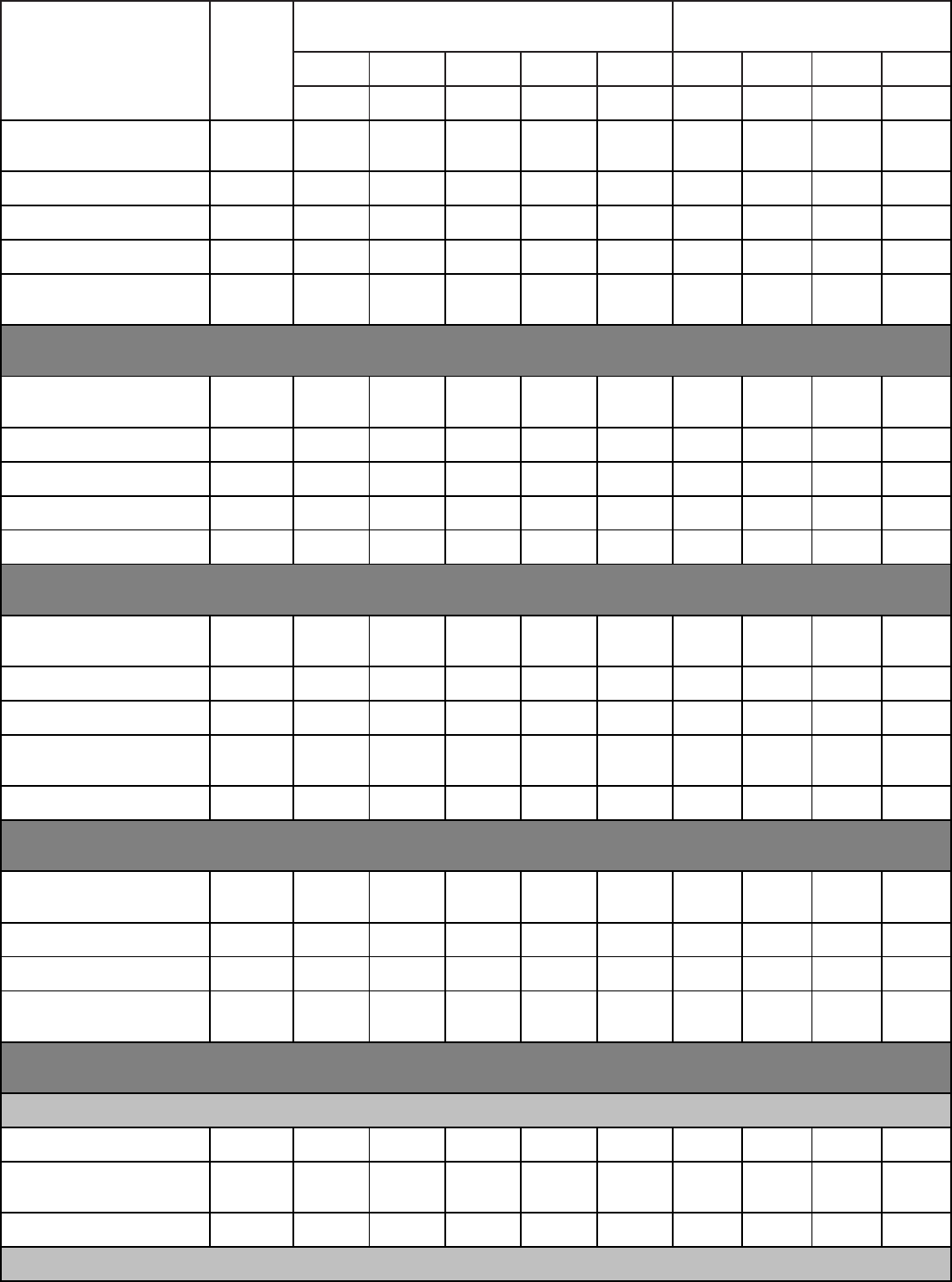
ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
52.3.5.2. Mobile User Objective
System (MUOS)
----
52.3.5.3. ANW2
----
52.3.5.4. TACSAT DAMA
----
52.3.5.5. HPW
----
52.3.5.6. Program Radio Using an
Advanced Waveform
----
53.1. Conventional LMR Systems
----
53.2. Trunked LMR Systems
----
53.3. Enterprise LMR Systems
----
53.4. LMR Systems Encryption
----
53.5. Program LMRs
----
54.1. Principles, Capabilities, and
Limitations
----
54.2. Controls and Indicators
----
54.3. Functions of Modules
----
54.4. Perform Operational Checks
----
54.5. Configure
----
55.1. Common Cryptology Methods
----
55.2. Cryptological Equipment
----
55.3. Fill Devices
----
55.4. Operate Selected
Cryptological Equipment
----
56.1.1. Space Segment
----
56.1.2. Command and Control
Segment
----
56.1.3. Terminal Segment
----
56.1. Satellite System Segments Principles, Capabilities, and Limitations
56.2. Satellite Bands, Purpose, Capabilities and Limitations
53. LAND MOBILE RADIO (LMR) TRANSMISSION SYSTEMS
TR: Applicable TOs and Commercial Manuals
54. INSTALLATION NOTIFICATION AND WARNING SYSTEMS (GIANT VOICE)
TR: AFI 10-2501 and Commercial Manuals
55. CRYPTO PRINCIPLES
TR: Applicable TOs and Manuals
56. SATELLITE COMMUNICATIONS (SATCOM)
TR: CJCSI 6250.01; Applicable DISA Circulars, USSTRATCOM Wideband Standards and Operating Procedures
1D7XX/X STS (Legacy)
39
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
56.2.1. Commercial C, Ku, K, X and
Ka Band
----
56.2.2. Commercial L Band
----
56.3.1. FDMA
----
56.3.2. TDMA
----
56.3.3. CDMA
----
56.3.4. DAMA
----
56.4.1. Wideband Global Satellite
(WGS)
----
56.4.2. Defense Satellite
Communications System (DSCS)
----
56.4.3. Defense Meteorological
Satellite Program (DMSP)
----
56.4.4. Defense Support Program
(DSP)
----
56.4.5. MILSTAR
----
56.4.6. Advanced Extremely High
Frequency (AEHF)
----
56.4.7. Global Positioning Service
(GPS)
----
56.4.8. Mystic Star
----
56.4.9. Commercial Satellite
Systems
----
56.4.10. Air Force Satellite Control
Network (AFSCN)
----
56.5.1. Introduction to UHF, SHF,
EHF Terminals
----
56.5.2. Multiband Satellite
Terminals
----
56.5.3. Power Distribution System
----
56.5.4.1. Transmitter
----
56.5.4.2. Up Converters
----
56.5.4.3. Power Amplifiers (PA)
----
56.5.4. Transmit Systems
56.5.5. Receive Systems
56.3. Satellite Access Principles
56.4. Satellite Systems and Constellations
56.5. SATCOM Terminal Characteristics
1D7XX/X STS (Legacy)
40
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
56.5.5.1. Receiver
----
56.5.5.2. Low Noise Amplifiers
(LNA)
----
56.5.5.3. Down Converters
----
56.5.6.1. Antenna Systems
----
56.5.6.2. Acquisition and Tracking
Principles
----
56.5.6.3. Calculate Satellite Look
Angles using specialized tools
----
56.5.6.4. Acquire and Track
Satellites
----
56.5.7.1. Perform Power Up/Down
Procedures
----
56.5.7.2. Configure the Baseband
Equipment
----
56.5.7.3. Perform Baseband
Equipment Operational Check
----
56.5.7.4. Configure Transmit and
Receive Equipment
----
56.5.7.5. Perform Transmit and
Receive Equipment perational
Check
----
56.5.7.6. Configure the Antenna
System
----
56.5.7.7. Configure Control,
Monitor, and Alarm system
----
56.5.7.8. Interfacing External
Multiplexing Equipment
----
56.5.7.9. Timing and
Synchronization
----
56.5.8.1. Principles, Capabilities,
and Limitations
----
56.5.8.2.1. Principles, Capabilities,
and Limitations
----
56.5.8.2.2. Perform Operational
Check
----
56.5.8.2.3. Configure
----
56.5.8.2.4. Troubleshoot
----
56.5.8.2. Multiplexing Equipment
56.5.6. Antenna and Tracking Systems
56.5.7. Multiband Satellite Terminal Operation
56.5.8. Network Bandwidth Management Equipment
1D7XX/X STS (Legacy)
41
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
56.6.1.1. Satellite Database
----
56.6.1.2. Satellite Access Request
(SAR)
----
56.6.1.3. Submit SAR
----
56.6.1.4. Gateway Access Request
----
56.6.2.1. Principles
----
56.6.2.2. Establish a
Communications Link
----
56.6.3.1. Identify Counter Counter
Measures Facts and Terms
----
56.6.3.2. Maintain Master Station
Logs
----
56.6.3.3. Develop After Action
Reports
----
56.6.3.4.1. SATCOM Equipment
Reports (SERS)
----
56.6.3.4.2. HAZCON Reports
----
56.7.1. Principles, Capabilities, and
Limitations
----
56.7.2. Controls and Indicators
----
56.7.3. Operate a GPS Receiver
----
57.1.1. Internetworking Basics
Fundamentals
----
57.1.2. OSI Reference Model
----
57.1.3. Topologies
----
57.1.4. IPv4/IPv6 Addressing
Fundamentals
----
57.1.5. Fundamentals of Protocols
----
56.6.3.4. DISA Reports
56.7. Global Positioning System Receiver
57. INTERNET PROTOCOL (IP) NETWORKING
TR: AF e-Learning
57.1. Internetworking Basics
56.6. SATCOM Link Operations
56.6.1. Access Processes
56.6.2. Communication Link Establishment
56.6.3. Communication Link Maintenance
1D7XX/X STS (Legacy)
42
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
57.2.1. Internet Protocols
----
57.2.2. TCP/IP
----
57.2.3. LAN Technologies
----
57.2.4. WLAN (Wireless IEEE
802.11)
----
57.2.5.1. WAN Fundamentals
----
57.2.5.2. Routing
----
57.2.5.3. Configure Router
----
57.2.5.4. Quality of Service (QoS)
----
57.2.5.5. Survivability
----
57.2.5.6. IP Network Security
----
58.1. Methods of Interfacing RF
Devices with IP Networks
----
58.2. Interface Selected RF
Equipment with an IP Network
----
58.3. Cellular IP Networks and
Equipment (GSM, LTE, CDMA)
----
59.1. Switched Electrical Power
Systems
----
59.2. Uninterruptible Power
Supplies (UPS)
----
59.3. Batteries
----
59.4. Rectifiers
----
59.5. Filters
----
59.6. Inverters
----
59.7. Generators
----
60.1.1. Principles, Capabilities, and
Limitations
----
60.1.2. Controls and Indicators
----
57.2.5. WAN Technologies
58. RF DEVICES TO IP NETWORKING
TR: Commercial Publications
59. ELECTRICAL POWER SYSTEMS
TR: Commercial Manuals
60. MICROWAVE TRANSMISSION SYSTEMS
TR: TO 31-1-141-11-WA-1, TO 31-1-141-12-WA-
60.1. Line of Sight Microwave Radio Systems
57.2. Networking
1D7XX/X STS (Legacy)
43
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
60.1.3. Setup and Teardown
----
60.1.4. Configure Microwave
System
----
60.1.5. Troubleshoot
----
60.2. Troposcatter Radio System
Theory
----
61.1. Explain duties of AFSC
A---
62.1.1. Goals and Principles
A---
62.1.2. Use Software
Development/Engineering Tools
(e.g.IDE, DBMS, CLI)
2b---
62.1.3. Compiling
2b---
62.2.1. Define Problem
3b---
62.2.2. Problem Solution
Statements
3b---
62.2.3. Develop Problem Solution
3b---
62.3.1. Concepts
A---
62.3.2. Design
A---
62.3.3. Programming
2b---
62.4.1. Sequential Design
----
62.4.2. Conditional Primitives
2b---
62.4.3. Iterative Primitives
2b---
62.4.4. Data Manipulation
2b---
62.4.5. Exception Handling
2b---
62.4.6. Bit Functions
----
62.4.7. Threading
----
62.4.8. System Interfaces
2b---
62.4.9. Design Patterns (e.g.MVC)
A---
62.4. Design Concepts
61. SOFTWARE DEVELOPMENT OPERATIONS CAREER FIELD
TR: 1D7X1Z Learning Program (AF e-Learning); AFH 33-337; AFIs 10-401, 33-100, 33-101, 33-115 Vols 1 & 3, 33-150, 36-2101; 1D7X1Z CFETP; AFECD
62. SOFTWARE DEVELOPMENT FUNDAMENTALS
TR: 1D7X1Z Learning Program (AF e-Learning)
62.1. Software Engineering
62.2. Problem Solving
62.3. Object Oriented Software Engineering
1D7XX/X STS (Legacy)
44
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
62.5.1. HTML Basics
2b---
62.5.2. CSS Basics
2b---
62.5.3. JavaScript
2b---
62.5.4. JavaScript /HTTP Interaction
2b---
62.5.5. JavaScript Libraries
(e.g.jQuery, Angular, Bootstrap)
A---
62.5.6. Document Object Model
(DOM)
A---
62.5.7. Representational State
Transfer (REST)
----
62.5.8.1. Government Cloud
Providers
----
62.5.8.2. Commercial Cloud
Providers
----
62.6.1. Reasoning / Purpose
A---
62.6.2.1. JSON
A---
62.6.2.2. Google Protobuffs
----
62.6.2.3. XML
A---
62.6.2.4. YAML
----
62.7.1. Create
2b---
62.7.2. Read
2b---
62.7.3. Update
2b---
62.7.4. Delete
2b---
63.1. Interpersonal Skills
A---
63.2. Elicit User Requirements
2b---
63.3. Evaluate User Requirements
----
63.4. User Stories
2b---
63.5. Feasibility Studies
----
62.7. Persistent Storage Functions
63. SOFTWARE DEVELOPMENT PROCESS
TR: 1D7X1Z Learning Program (AF e-Learning)
63.6. Technical Design Considerations
62.5. Web Fundamentals
62.5.8. Cloud Providers
62.6. Serialization
62.6.2. Types
1D7XX/X STS (Legacy)
45
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
63.6.1. Environmental Limitations
----
63.6.2. Environmental
Considerations
----
63.7. Software Quality Metrics
A---
63.8. Extreme Programming
2b---
63.9. Lifecycle Methodologies
A---
63.10. Test Driven Development
2b---
63.11. Iterative Development
A---
63.12. DevOps
A---
63.13.1. Software System
Documentation
A---
63.13.2. User Documentation
A---
64.1. Overview
A---
64.2.1. Purpose
A---
64.2.2. Repositories
A---
64.2.3. Lock Modify Unlock Model
A---
64.2.4. Copy Modify Merge Model
A---
64.2.5. Utilize Source Control Tools
2b---
64.2.6.1. Version Number Scheme
----
64.2.6.2. Release Baselines
----
64.2.6.3. Concurrent Release
Development
----
64.3.1. Development of Library
Modules
----
64.3.2. Use
2b---
64.3.3. Maintain
----
64.2. Source Control
64.2.6. Versioning
64.3. Software Support Libraries
65. SOFTWARE SECURITY
TR: 1D7X1Z Learning Program (AF e-Learning)
63.13. Create/Update Software Documentation
64. SOFTWARE CONFIGURATION MANAGEMENT
TR: 1D7X1Z Learning Program (AF e-Learning)
1D7XX/X STS (Legacy)
46
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
65.1.1. Buffer Overflow
B---
65.1.2. Stack Overflow
B---
65.1.3. Heap Overflow
B---
65.1.4. Format String Attack
B---
65.1.5. Fuzzing
----
65.1.6. Safe Functions
B---
65.1.7. Memory Leaks
B---
65.1.8. Root Kits
----
65.1.9. Privilege Escalation/Lateral
----
65.1.10. Check Return Values
----
65.1.11. Shellcode
----
65.2.1. Transport Layer Security
----
65.2.2. Encoding
----
65.2.3. Tunneling
----
65.2.4. Session Hijacking
----
65.2.5. Integrity / Checksum Check
----
65.2.6. Cross Site Request Forgery
----
65.3.1. Data Validation
2b -
65.3.2. Sanitization
2b -
65.3.3. SQL Injection
--
65.3.4. Code Injection
--
65.3.5. Cross Site Scripting
--
65.4.1. Block
----
65.4.2. Stream
----
65.4.3. Securely Stored
Tokens/Keys/Certificates
----
65.4.4. End to End Encryption
----
65.4.5. RSA
----
65.2. Transport Security
65.3. Input Validation
65.4. Encryption
65.1. System Security
1D7XX/X STS (Legacy)
47
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
65.4.6. Public Key Infrastructure
(PKI)
----
65.4.7.1. Certificate Trust Chain
----
65.4.7.2. Certificate Revocation List
----
65.4.7.3.1. OpenSSL
----
65.4.7.3.2. Bouncy Castle
----
65.4.7.4. Authentication Levels
----
65.5.1. Strings
----
65.5.2. VirusTotal
----
65.5.3. Advanced Static Analysis
----
65.5.4. Advanced Dynamic Analysis
----
65.5.5. Wireshark
----
65.5.6. Imports/Exports
----
65.5.7. Isolate in Virtual Machine
----
65.6. Common Vulnerabilities and
Exposures (CVE)
----
65.7. Information Assurance
Vulnerability Alert (IAVA)
----
65.8. Auditing
----
66.1.1. Test Plans
A---
66.1.2.1. Format
2b---
66.1.2.2. Positive Testing
A---
66.1.2.3. Negative Testing
A---
66.1.3. Bug Reporting
A---
66.2.1. Black / White Box Testing
----
66.2.2. Functional Testing
65.5. Malware Reverse Engineering
66. SOFTWARE TESTING
TR: 1D7X1Z Learning Program (AF e-Learning)
66.1. Documentation
66.1.2. Test Cases
66.2. Testing Types
65.4.7. Certificates
65.4.7.3. Certificate Generation
1D7XX/X STS (Legacy)
48
Atch 7
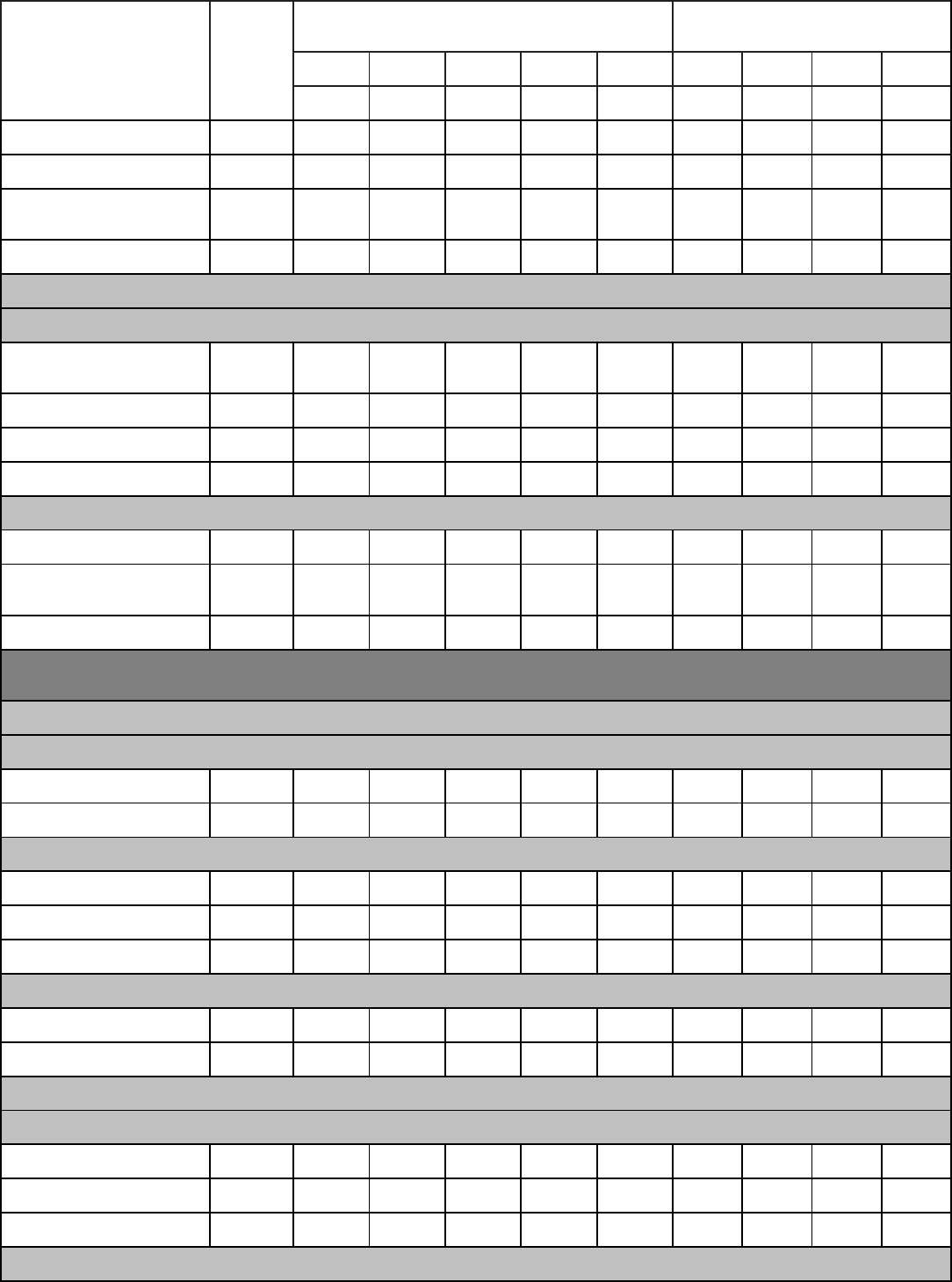
ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
66.2.2.1. Unit Testing
A---
66.2.2.2. Integration Testing
A---
66.2.2.3. System / Regression
Testing
A---
66.2.2.4. Acceptance Testing
A---
66.2.3.1.1. Vulnerability Scanning
----
66.2.3.1.2. Security Scanning
----
66.2.4. Performance Testing
A---
66.2.5. End to End Testing
A---
66.3.1. GUI Testing
A---
66.3.2. Web Services / API Testing
A---
66.4. Continuous Testing
A---
67.1.1.1. Collection
A---
67.1.1.2. Prioritization
----
67.1.2.1. Data Entry
----
67.1.2.2. Syntax
2b---
67.1.2.3. Logic
2b---
67.2.1. Migration
----
67.2.2. Redesign
----
67.3.1.1. Federal Requirements
----
67.3.1.2. Functional Testing
2b---
67.3.1.3. Security Testing
2b---
67.3.1. Periodic Validation
67.3.2. Efficiency Analysis
67.1. Corrective
67.1.1. Bug Management
67.1.2. Error Correction
67.2. Adaptive
67.3. Perfective
66.2.3. Nonfunctional Testing
66.2.3.1. Security Testing
66.3. Testing Automation
67. SOFTWARE MAINTENANCE
TR: 1D7X1Z Learning Program (AF e-Learning)
1D7XX/X STS (Legacy)
49
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
67.3.2.1. Hardware Limitations
----
67.3.2.2. OS / Host System
Limitations
----
68.1. User Centered Design
A---
68.2. Information Architecture
A---
68.3. Interaction Design
A---
68.4. Visual Design
A---
68.5. Accessibility
A---
68.6. Usability
A---
69.1.1. Logical
A---
69.1.2. Normalization
A---
69.1.3. Denormalization
A---
69.1.4. Physical
A---
69.1.5.1. Relational
A---
69.1.5.2. Key Value
A---
69.1.5.3. Document
A---
69.1.5.4. Graph
A---
69.1.5.5. Column Oriented
A---
69.1.6.1. CAP Theorem
----
69.1.6.2. Atomicity, Consistency,
Isolation, Durability (ACID)
----
69.1.6.3. Basically Available, Soft
State, Eventual Consistency (BASE)
----
69.1.7. Query Performance Tuning
A---
69.1.8. Backups
A---
69.1.9. Restore and Recovery
A---
69.2.1. Table
A---
69.1.5. Data Models
69.1.6. Transaction Processing
69.2. Objects
68. USER EXPERIENCE DESIGN (UXD)
TR: 1D7X1Z Learning Program (AF e-Learning)
69. DATABASE
TR: 1D7X1Z Learning Program (AF e-Learning)
69.1. Design
1D7XX/X STS (Legacy)
50
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
69.2.2. View
A---
69.2.3. Stored Procedure
A---
69.2.4. Trigger
----
69.2.5. Index
----
69.2.6. Query Language
Fundamentals
2b---
70.1.1. Cache Levels
----
70.1.2. Memory Allocation
----
70.1.3. Stack
----
70.1.4. Heap
----
70.1.5. Data Types
A---
70.2. Character Encoding
A---
70.3. Compilers / Flags
----
71.1.1. Networking RFCs
----
71.1.2. Network Byte Order
----
71.2.1. SSH
A---
71.2.2. SSL / TLS
A---
71.2.3. Secure FTP Versions
A---
71.2.4. HTTP(S)
A---
71.2.5. SNMP
A---
71.3.1. BSD Sockets
----
71.3.2. WinSock
----
71.3.3. Pipes
----
71.3.4. FIFOs
----
71.3.5. Websockets
----
71.4.1. Web Proxies
----
71. NETWORKING
TR: 1D7X1Z Learning Program (AF e-Learning)
71.1. Network Fundamentals
71.2. Common Protocols (e.g.Handshake, State, OSI Layer, Header Standard Port #)
71.3. Sockets
71.4. Proxy/Redirection
70. ARCHITECTURE
TR: 1D7X1Z Learning Program (AF e-Learning)
70.1. Memory
1D7XX/X STS (Legacy)
51
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
71.4.2. Forward Proxy
----
71.4.3. Reverse Proxy
----
71.4.4. Anonymous Proxies
----
71.4.5. Tunneling
----
71.5.1. Ping
A---
71.5.2. Tracert / Traceroute
A---
71.5.3. Ipconfig / Ifconfig
A---
71.5.4. Netstat
A---
72.1. Duties/Responsibilities of
AFSC
A---
72.2. Spectrum Operations Role in
Cyber
B---
73.1. Air Force Safety, Fire, and
Health Standards for AFSC
A---
73.2. Hazards of the AFSC
A---
73.3. Manage Work Center Safety
Program
----
74.1. Cyber Mission Force
----
74.2. Explain Qualifications
----
74.3.1. OPSEC
----
74.3.2. INFOSEC
----
74.3.3. COMPUSEC
----
74.3.4. TEMPEST
A---
74.3.5. COMSEC
A---
74.4. Physical Security
A---
74.5. Classified Material Control
----
74.6. Force Management
TR: AFECD; AFIs 36-2651, 36-2845, 38-101, 33-396
71.5. Command Line Network Utilities
72. SPECTRUM OPERATIONS CAREER FIELD
TR: 1D7X2F Learning Program (AF e-Learning); AFI 36-2101; CFETP; AFECD
73. SAFETY/RISK MANAGEMENT (RM)
TR: AFI 48-109; AFI 90-802; AFI 91-202; AFMAN 91-203
74. INTRODUCTION TO CYBER
TR: AFI 36-2101; AFGM2018-17-02
74.3. Security Programs
TR: AFIs 10-701, 16-1404; AFPD
1D7XX/X STS (Legacy)
52
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
74.6.1. Utilization and Training
Workshop (U&TW) & Specialty
Training Requirements Team
(STRT)
----
74.6.2. Occupational Survey
----
75.1. International
Telecommunications Union (ITU)
Radio Regulations
B---
75.2.1. U.S. National Policy
Regulation
B---
75.2.2. National
Telecommunications & Information
Administration (NTIA)
B---
75.2.3. Federal Communications
Commission (FCC)
B---
75.2.4. Code of Federal Regulations
Title 47
B---
75.2.5. Spectrum Legislation
----
75.2.6. National Frequency Table of
Allocations
----
75.3.1. DoD Chief Information
Officer (DoD CIO)
A---
75.3.2. Defense Spectrum
Organization (DSO)
A---
75.3.3. Joint Chiefs of Staff United
States Military Command, Control,
Communications, and Computers
(C4) Executive Board (JCSMC4EB)
A---
75.3.4. Military Command, Control,
Communications, and Computers
(C4) Executive Board (MC4EB)
Frequency Panel (FP)
B---
75.3.5. Joint Spectrum Center (JSC)
B---
75.3.6. Unified/Specified Command
B---
75.3.7. DoD Area Frequency
Coordinator
B---
75.3.8. MAJCOM
B---
75.3.9. Wing/Base
B---
75. SPECTRUM MANAGEMENT
75.2. National and Government
75.3. DoD Spectrum Management Organization
1D7XX/X STS (Legacy)
53
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
75.3.10. Test Ranges
----
75.3.11. US Army Spectrum
Organization
----
75.3.12. US Navy Spectrum
Organization
----
75.3.13. US Marine Corps
Spectrum Organization
----
75.3.14. US Air Force Spectrum
Organization
B---
75.3.15. DoD Policy
B---
75.4. OCONUS Spectrum
Management Structure (e.g. NATO)
----
75.5.1.1. Application for Equipment
Frequency Allocation (DD Form
1494)
B---
75.5.1.2. Note to Holders
B---
75.5.1.3. Foreign Disclosure
B---
75.5.1.4. Commercial Off the Shelf
B---
75.5.1.5. Host Nation Coordination
B---
75.5.2.1.1. Purpose
B---
75.5.2.1.2. Query Database
2b---
75.5.2.1.3. Perform Title Search
2b---
75.5.2.1.4. Supportability
Comments (e.g. Host Nation
Documents)
2b---
75.5.2.2.1. Purpose
B---
75.5.2.2.2. Query Database
2b---
75.5.2.2.3. Supportability
Restrictions
B---
75.5.2.3.1. Purpose
B---
75.5.2.3.2. Query Database
2b---
75.5.1. Processes
75.5.2. Operational Databases (Global Electromagnetic Spectrum Information System, GEMSIS)
75.5.2.1. Spectrum Certification Systems (Ex: SCS Database/E2ESS)
75.5.2.2. Host Nation Support Systems (Ex: Host Nation Supportability Worldwide Database Online HNSWD-O)
75.5.2.3. Joint Spectrum Data Repository (JSDR)
75.5. Spectrum Certification
1D7XX/X STS (Legacy)
54
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
75.5.2.4.1. Overview of Installation
----
75.5.2.4.2. Configure System
Preferences
----
75.5.2.4.3. Help Files
----
75.5.2.5.1. Purpose
A---
75.5.2.5.2. Install Topographic
Manager (TOPOMAN)
2b---
75.5.2.5.3. Topographic Data
Acquisition
A---
75.5.2.5.4. Import/Activate Data
Files
2b---
75.5.2.6.1. Purpose
A---
75.5.2.6.2. Perform Initial Data
Exchange
2b---
75.5.2.6.3. System Interfaces (e.g.
STE, SIPRNET)
A---
75.5.2.7.1. Purpose
A---
75.5.2.7.2. Load Initial Frequency
Assignments
2b---
75.5.2.7.3. Perform Database Query
2b---
75.5.2.7.4. Manipulate Database
Query
2b---
75.5.2.7.5. Use Proposal Functions
2b---
75.5.2.7.6. Interpret Status Codes
2b---
75.5.2.7.7. Interpret Digital Agendas
2b---
75.5.2.7.8. Produce Management
Reports
2b---
75.5.2.7.9. Use System Manager
Module
2b---
75.5.2.7.10. Use Allotment Plans
Module
2b---
75.5.2.7.11. Use Interference
Analysis Module
2b---
75.5.2.4. Spectrum XXI
75.5.2.5. Topographic Data
75.5.2.6. Data Exchange
75.5.2.7. Frequency Assignment Module
1D7XX/X STS (Legacy)
55
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
75.5.2.7.12. Use Engineering Tools
Module
2b---
75.5.2.7.13. Use Joint Restricted
Frequency List Editor Module
----
75.5.2.7.14. Use Electronic Warfare
Deconfliction Module
----
75.6.1. Allied Partners
----
75.6.2.1. Peacetime
B---
75.6.2.2. Wartime/ Contingency
B---
75.7. Position Continuity Plan
----
76.1. Bandwidth Types (e.g.
Necessary, Authorized and
Occupied)
B---
76.2.1. Composition
B---
76.2.2. Formulate
2b---
76.2.3. Interpret
2b---
76.2.4. Determine
2b---
76.3.1. Principles
B---
76.3.2. Types
B---
76.3.3. Research Table of
Allocations
2b---
76.3.4. Research Footnotes,
Provisions and Remarks
2b---
76.3.5. Determine Radio Service
2b---
76.3.6. Determine Type Station
Class
2b---
76.4.1. Administrative Data
B---
76.4.2. Emission Characteristics
Data
B---
76.4.3. Organizational Data
B---
76.4.4. Transmitter Data
B---
76.4.5. Space Systems Data
B---
75.6.2. Frequency Assignment
76. SPECTRUM MANAGEMENT PRINCIPLES ADMINISTRATION
76.2. Emission Designators
76.3. Radio Communications Service and Station Classes
76.4. Standard Frequency Action Format (SFAF)
75.6. Coordination Policy
1D7XX/X STS (Legacy)
56
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
76.4.6. Receiver Data
B---
76.4.7. Supplemental Details Data
B---
76.4.8. SFAF Processing
B---
76.4.9. Prohibited Data Entries
B---
76.4.10. Restricted Data Entries
B---
76.4.11. Data Item Occurrence
Identifiers
B---
76.4.12. Data Item Purge Identifier
B---
76.4.13. Mass Purge Identifier
B---
76.4.14. Multiple Record Identifiers
B---
76.4.15. Types of Input for SFAF
Proposals (e.g. Theater Unique
Requirements)
B---
76.4.16. Mass Record Changes
B---
76.4.17. SFAF Transaction Security
Rules
B---
76.4.18. Classification of Aggregate
Frequency Records (e.g. Theater
Unique Requirements)
B---
76.5.1. Frequency Resource Record
System (FRRS)
B---
76.5.2. Government Master File
(GMF)
----
76.5.3. Federal Communications
Commission (FCC) File
----
76.5.4. International Frequency List
(IFL)
----
76.5.5. Area Studies
----
77.1. Order of Operations
----
77.2. Convert Between Units of
Power, Voltage and Frequency
----
77.3. Solve Problems Using
Common Logarithms
----
77.4. Convert Decibels
----
76.5. National and International Databases
77. MATHEMATICS OF SPECTRUM MANAGEMENT
77.5. Power
1D7XX/X STS (Legacy)
57
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
77.5.1. Power, Voltage, Current &
Resistance
----
77.5.2. Calculate Power Using
Decibels
----
78.1.1. Amplitude Modulated
B---
78.1.2. Frequency Modulated
B---
78.1.3. Pulse/Phase Modulated
B---
78.1.4. Principles of Transmitters/
Receivers
B---
78.2.1. Internal Noise Theory
----
78.2.2. Receiver Selectivity
----
78.3.1. Coaxial Cables (Flexible,
Semi-rigid, & Rigid)
----
78.3.2. Open/Parallel Lines
----
78.3.3. Wave Guides
----
78.3.4. Fiber Optics
----
78.3.5. Dielectric Types
----
78.3.6. Attenuation
----
78.3.7. Standing Wave Ratios
----
78.3.8. Effective Isotropic Radiated
Power (EIRP)
----
78.3.9. Effective Transmit Power
(ETP)
----
78.4.1.1. Dipole
----
78.4.1.2. Whip
----
78.4.1.3. Longwire
----
78.4.1.4. Horn
----
78.4.1.5. Helical
----
78.4.1.6. Parabolic
----
78.4.1.7. Reflector
----
78.4.1.8. Array
----
78.2. Receiver Sensitivity
78.3. Transmission Lines
78.4. Antenna Principles
78.4.1. Common Antennas
78. RADIO FREQUENCY (RF) PRINCIPLES
78.1. Modulation Techniques
1D7XX/X STS (Legacy)
58
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
78.4.2. Antenna Efficiency
----
78.4.3. Antenna Gain
----
78.4.4. Polarization
B---
78.5.1.1. Free Space
----
78.5.1.2. Refraction
----
78.5.1.3. Reflection
----
78.5.1.4. Diffraction
----
78.5.1.5. Knife Edge Diffraction
----
78.5.2. Path Loss
----
78.5.3. Multipathing
----
78.5.4. Free Space Loss
----
78.5.5. Calculate Path Loss
----
78.6.1. Frequency Hopping Theory
B---
78.6.2. Spread Spectrum Theory
B---
78.6.3. Jam Resistant Systems
Employment
----
78.6.4.1. Have Quick Systems
----
78.6.4.2. Single Channel Ground
and Airborne Radio System
(SINCGARS)
----
78.6.4.3. Joint Tactical Information
Distribution System
(JTIDS)/Multifunctional Information
Distribution System (MIDS)
----
78.6.4.4. Airborne\ Enhanced
Position Location Reporting System
(A\EPLRS)
----
78.6.4.5. Software Defined Systems
----
79.1.1. Physical & Non- Physical
Emissions from the Sun
----
78.5.1. Radio Wave Propagation
78.6. Jam Resistant Communications
78.6.4. Frequency Agile Systems
79. SPECTRUM PLANNING FOR HIGH FREQUENCY (HF) SYSTEMS
79.1. Solar Ionospheric Physics
78.5. Electromagnetic Wave Propagation Theory
1D7XX/X STS (Legacy)
59
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
79.1.2. Ionization
----
79.1.3. Recombination
----
79.1.4. Earth’s Atmosphere
----
79.1.5. Sunspots
----
79.1.6. Sunspot Number
----
79.1.7. Solar Flares
----
79.1.8. Solar Variations
----
79.2.1. Skip Distance
----
79.2.2. Skip Zone
----
79.2.3. Critical Angle
----
79.2.4. Critical Frequency
----
79.2.5. Maximum Usable Frequency
(MUF)
----
79.2.6. Frequency Optimum
Transmission (FOT)
----
79.2.7. Lowest Usable Frequency
(LUF)
----
79.2.8. Factors for Refraction
----
79.2.9. Ionospheric Sounders
----
79.2.10. Automatic Link
Establishment (ALE)
----
79.3. Antenna Radiation Patterns
----
79.4.1. Physical Properties of
Antennas
----
79.4.2. HF Antenna Selection
Based on Patterns Versus Path
Requirements
----
79.5.1. Characteristics and
Variations
----
79.5.2. Effects on Termination and
Directivity
----
79.6.1. Principles of Sideband
Techniques
----
79.2. Skywave Fundamentals
79.4. Antenna Planning
79.5. Long-Wire Antennas
79.6. HF Tuning Techniques
1D7XX/X STS (Legacy)
60
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
79.6.2. Reference Frequency and
Assigned Frequency Identification
----
79.6.3. Occupied Spectrum
----
79.7.1. Fundamentals
B---
79.7.2. Reliability Factors
----
79.7.3. Interpret Propagation
Prediction Products
----
79.8. Use Automated HF Prediction
Systems
----
79.9.1. Principles of HF System
Planning
B---
79.9.2. Determine best Antenna for
Requirements
----
79.9.3. Determine Path
Requirements using Propagation
Data
----
79.9.4. Engineer Ground Wave
Communications
----
79.9.5. Engineer Skywave
Communications
2b---
79.9.6. Complete SFAF Proposals
for HF Requirements
2b---
79.9.7. Nominate HF Frequencies
2b---
80.1.1. Principles of VHF/UHF AM
Systems Planning
----
80.1.2. Principles of Area Coverage
of A/G/A Systems Calculation
----
80.1.3. Principles of AM/FM
Air/Ground Communications
Engineering
----
80.1.4. Complete SFAF Proposals
for VHF/UHF AM/FM A/G/A
Requirements
2b---
80.1.5. Nominate VHF/UHF AM
A/G/A Frequencies
2b---
79.9. HF Systems Engineering
80. SPECTRUM PLANNING FOR VERY HIGH (VHF) & ULTRA HIGH FREQUENCY (UHF) SYSTEMS
80.1. VHF/UHF Amplitude Modulated (AM)/ Frequency Modulated (FM) Air/Ground/Air (A/G/A) Systems
80.2. VHF/UHF Frequency Modulated (FM) Systems
79.7. HF Groundwave Propagation and Predictions
1D7XX/X STS (Legacy)
61
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
80.2.1. Principles of VHF/UHF FM
Systems Planning
B---
80.2.2.1. Simplex
B---
80.2.2.2. Duplex/ Repeater
B---
80.2.2.3. Trunking
B---
80.2.3. Principles of System
Parameter Calculation (Distance,
Reliability, Antenna Height,
Frequency, Receive Signal Level
and Systems Gain/ Losses)
----
80.2.4. Complete SFAF Proposals
for LMR Requirements
2b---
80.2.5. Nominate LMR Frequencies
2b---
80.2.6. Complete SFAF Proposals
for VHF/UHF G/G Requirements
2b---
80.2.7. Nominate VHF/UHF G/G
Frequencies
2b---
81.1.1. Parabolic Antennas
----
81.1.2. Horn Antennas
----
81.1.3. Reflectors
----
81.1.4. Principles of the Gain
Calculation of Parabolic Antennas
----
81.1.5. Principles of the Gain
Calculation of Flat Passive
Reflectors
----
81.2.1. Principles of Refraction
B---
81.2.2. Principles of Direct and
Ground Propagation Paths
B---
81.2.3. Usable Frequency Range
----
81.2.4. Advantages/ Disadvantages
of LOS Systems in Communications
----
81.2.5. LOS Equipment Capabilities
and Limitations
----
81. SPECTRUM PLANNING FOR MULTICHANNEL SYSTEMS
81.1. Microwave Antennas
81.2. Line of Site (LOS) Systems
80.2.2. Spectrum Support for Land Mobile Radio (LMR) Systems
1D7XX/X STS (Legacy)
62
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
81.2.6. Basic Configurations of LOS
Systems
----
81.2.7. Propagation Considerations
in LOS Communications
----
81.2.8. Principles of Free Space
Loss for LOS Systems
Communications Calculation
----
81.2.9. Principles of LOS Systems
Path Profile
----
81.2.10. Principles of LOS Systems
Predicted Reliability
----
81.2.11. Develop SFAF Proposals
for LOS Requirements
2b---
81.2.12. Nominate LOS Systems
Frequencies
2b---
81.2.13. Frequency Share Plan for
Operating Multiple Systems at a
Single Location
----
81.3.1. TROPO Theory
----
81.3.2. Capabilities/ Limitations of
TROPO Systems
----
81.3.3. Principles of TROPO Total
Propagation Loss (TPL) Calculation
----
81.3.4. Principles of TROPO
Receive Signal Level (RSL)
Calculation
----
81.3.5. Principles of TROPO
Median Receiver Input Signal Level
Calculation
----
81.3.6. Principles of TROPO
Minimum Receiver Input Signal
Level Calculation
----
81.3.7. Principles of TROPO Fade
Margin and Reliability Calculation
----
81.3.8. Principles of TROPO Total
Path Loss Calculation
----
82.1. Application of Satellite
Systems
----
82.2. Satellite Terminology
----
82.3. Satellite Orbits
----
81.3. Troposcatter (TROPO) Systems
82. SPECTRUM PLANNING FOR SATELLITE SYSTEMS
1D7XX/X STS (Legacy)
63
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
82.4. Interference Mechanisms
Affecting Up/Down Link
Performance (e.g. Scintillation)
----
82.5. SFAF Requirements for
Satellite Access Authorization
(SAA)s
----
82.6. Develop SFAF Proposals for
SATCOM requirements
----
82.7. Satellite Look and Elevation
Angles
----
82.8.1. Ground Mobile Forces SAR
----
82.8.2. Tactical UHF SAR
(TACSAT)
----
82.8.3. Software Defined
Waveforms (MUOS, IW, DAMA,
DASA)
A---
82.9. DoD use of Commercial
Satellites
----
83.1.1. Principles of Radar
Operations
B---
83.1.2. Radar Types and Functions
B---
83.1.3.1. Operation
A---
83.1.3.2. Modes
A---
83.1.3.3. Complete SFAF
----
83.1.4. Principles of Radar Distance
Calculation
----
83.1.5. Complete SFAF Proposals
for Radar Requirements
----
83.1.6. Nominate Radar
Frequencies
2b---
83.2.1. Principles of NAVAID
Operations
B---
83.2.2. NAVAID Types and
Functions
B---
83.2.3. NAVAID Frequencies
B---
82.8. Satellite Access Request (SAR) Procedures
83. SPECTRUM PLANNING FOR NON- COMMUNICATIONS SYSTEMS
83.1. Radar Systems
83.1.3. IFF/SIF
83.2. Navigational Aid (NAVAID) Systems (e.g. TACAN)
1D7XX/X STS (Legacy)
64
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
83.2.4. Complete SFAF Proposal for
NAVAID Requirements
----
83.2.5. Nominate NAVAID
Frequencies
2b---
83.2.6. Principles of Global
Positioning Systems (GPS)
B---
83.2.7. Military Aircraft Collision
Avoidance System (MILACAS)
----
83.3. Wireless Technologies (e.g.
Radio Frequency Identification,
Wireless LAN)
----
83.4. Remotely Piloted Vehicles
----
83.5. Airborne ISR\C2 (e.g.
AWACS, JSTARS)
----
84.1.1. DoD EMC Programs
B---
84.1.2. Effects of Electromagnetic
Interference (EMI)
B---
84.2.1. EMI Potential
B---
84.2.2. Harmonic-Free Complement
Generation using Spectrum
Management Software
----
84.2.3. Intermodulation- Free
Compliment Generation using
Spectrum Management Software
----
84.3.1. Co-Channel Interference
B---
84.3.2. Adjacent Channel
Interference
B---
84.3.3. Spurious Responses
B---
84.3.4. Spurious Emissions
B---
84.3.5. Intermodulation
B---
84.3.6. Unintentional
Interference/Jamming
B---
84.3.7. Power Line Noise
B---
84.3.8. Mutual Interference
B---
84. ELECTROMAGNETIC COMPATIBILITY (EMC)
84.1. Fundamentals of EMC
84.2. Harmonics and Intermodulation
84.3. Types of Interference
85. ELECTRONIC COUNTERMEASURES (ECM) AND ELECTRONIC WARFARE (EW)
1D7XX/X STS (Legacy)
65
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
85.1.1. Electronic Attack
B---
85.1.2. Electronic Protection
B---
85.1.3. Electronic Support
B---
85.2. Clearance Process
B---
85.3. Coordination (ECM and EW)
B---
86.1. DoD RADHAZ Program
A---
86.2. Effects of Non- Ionizing
Radiation on Personnel, Fuels and
Ordnance (e.g. HERO, HERP)
A---
86.3. Electromagnetic Radiation
(EMR) Survey Requirements
B---
87.1.1. JTF Terminology
A---
87.1.2. Associated Publications/
Directives
A---
87.1.3. JTF Organizations
A---
87.1.4. JTF Command & Control
A---
87.1.5. JTF Operational Phases
A---
87.2. Information Warfare Purpose
and Relationship)
A---
87.3. Joint Electromagnetic
Spectrum Operations Cell
(JEMSOC)
A---
87.4.1. Crisis Action Planning (CAP)
Process
A---
87.4.2. CAP Spectrum Management
Responsibilities
A---
87.4.3. Global Command & Control
System and Joint Operational
Planning Execution System in CAP
----
87.4.4. Battlefield Spectrum Use
Considerations
B---
87.5.1. JACS Overview
----
87.5. Joint Automated Communication Electronics Operation Instructions (JCEOI) System (JACS)
85.1. Types
86. DOD ELECTROMAGNETIC ENVIRONMENTAL EFFECTS (E3) PROGRAM
87. SPECTRUM MANAGEMENT IN A JOINT ENVIRONMENT
87.1. Joint Task Force (JTF)
87.4. JTF Planning, Deployment, Buildup, and Employment
1D7XX/X STS (Legacy)
66
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
87.5.2.1. Overview
A---
87.5.2.2. Build
----
87.5.2.3. Manipulate
----
87.5.3. Import Data
----
87.5.4. Complete Frequency
Analysis
----
87.5.5. Generate SFAF Proposals
Import/Export
----
87.5.6. Use Resource Manager
Import/Export
----
87.5.7. Import SFAF Assignments
----
87.5.8. Generate JCEOI
----
87.5.9.1. Prints
----
87.5.9.2. Reports
----
87.5.10.1. Build HOPSET
----
87.5.10.2. Build LOADSET
----
87.5.10.3. Install LOADSET into
Radio
----
87.6.1. Annex K
A---
87.6.2. Air Tasking Order
(ATO)/Special Instructions (SPINS)
A---
87.6.3.1. Shipboard
Communications Planning
(OPTASK COMMS)
----
87.6.3.2. Shipboard Radar Planning
----
87.6.3.3. Deconflict Strike Group
Radar
----
87.6.3.4. Develop Strike Group
Communication Plans
----
87.6.3. Real Time Spectrum Operations (RTSO)
88. ELECTROMAGNETIC BATTLESPACE (EMB) INTERGRITY (ELECTRONIC WARFARE SUPPORT)
88.1. Interference Reporting Policy
87.5.2. Master Net List
87.5.9. Produce JCEOI Outputs
87.5.10. Operations
87.6. Service Specific Communications Operations Plans
1D7XX/X STS (Legacy)
67
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
88.1.1. Joint Spectrum Interference
Resolution (JSIR)
B---
88.1.2. Air Force Spectrum
Interference Resolution (AFSIR)
Program
B---
88.2.1. Electronic Order of Battle
(EOB)
A---
88.2.2. Conduct EMB Site/ Emitter
Survey
2b---
88.2.3. Operate EMB Analysis Tools
2b---
88.2.4. Operate GPS Receiving
Device
----
88.2.5. Establish Normal Baseline
of EMB
2b---
88.2.6. Determine Abnormal
Activities within the EMB
2b---
88.2.7. Determine
Availability/Limitations of EMB to
meet mission requirements
2b---
88.3.1. Direction Finding
Techniques
B---
88.3.2. Determine Emission
Location
2b---
88.3.3.1. Determine Modulation
Type
2b---
88.3.3.2. Determine Occupied
Bandwidth
2b---
88.3.3.3. Determine Amplitude
2b---
88.3.3.4. Determine Emission
Transmission Period
2b---
88.3.4.1.1. Friendly Forces
B---
88.3.4.1.2. Hostile Forces
B---
88.3.4.1.3. Neutral Sources
B---
88.3.4.1.4. Unintentional Sources
B---
88.3.4.2. Natural Sources
B---
88.3.3. Emission Characteristics
88.3.4. Mitigation Techniques
88.3.4.1. Man-Made Sources
88.2. Electromagnetic Management Battlespace (EMB) Signature Management
88.3. Interference Resolution
1D7XX/X STS (Legacy)
68
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
88.3.4.3. Incident Escalation
Procedures
B---
89.1.1. Identify AOR
----
89.1.2. Conduct EMB Site/ Emitter
Survey
----
89.1.3. Establish Normal Baseline
of EMB
----
89.1.4. Operate EMB Analysis Tools
----
89.1.5. Query HNSWDO Database
----
89.1.6. Use Spectrum XXI Proposal
Functions
----
89.1.7. Complete SFAF Proposals
for VHF/UHF G/G Requirements
----
89.1.8. Nominate VHF/UHF G/G
Frequencies
----
90.1. Management Policies
----
90.2.1. Base/Unit Roles &
Responsibilities
----
90.2.2. Supervisor / Trainer Roles &
Responsibilities
----
90.2.3. Task Certifier Roles &
Responsibilities
----
90.2.4. Trainee Responsibilities
----
91.1. Career Field Functional
Management
----
91.2. Superintendent Duties
----
91.3. Force Development/
Management
----
91.4. Awards and Recognition
----
92.1. Financial Management
----
90. WORK CENTER MANAGEMENT
TR: 1D7XX Learning Program (AF e-Learning); AFIs 10-201, 21-103, 146352, DODI1400.25V610_AFI36-807; TO 00-33A-1001; AFJQS XXXXX-212S
90.2. Training
91. FUNCTIONAL MANAGEMENT
TR: 1D7XX Learning Program (AF e-Learning); AFECD; AFIs 36-2651, AFPD 36-28, 38-101, AFMAN 33-396; AFQTP 1D7XX-225E; 1D7XX CFETP
92. RESOURCE MANAGEMENT
TR: 1D7XX Learning Program (AF e-Learning); AFPDs 10-6, 656; AFIs 10-601, 65601 V(1) & V(2)
89. CAPSTONE
89.1. Pre-Deployment
1D7XX/X STS (Legacy)
69
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
92.2. Funded Requirements
----
92.3. Unfunded Requirements
----
93.1. Manpower Requirements
----
93.2. Air Force Manpower Standard
(AFMS) Application
----
93.3. Manpower Studies
----
93.4. Manpower Products
----
93.5. Allocating Personnel
----
94.1. Duties/Responsibilities of
AFSC
A---
94.2. Cable and Antenna Systems'
Role in Cyber
B---
94.3.1. Explain Duties of AFSC
----
94.3.2. Explain Responsibilities of
AFSC
----
94.3.3. Explain AFSC Core
Competencies
----
94.3.4. Explain Qualifications
----
95.1.1. Communication Squadrons
----
95.1.2. Combat Communication
Squadrons
----
95.1.3. Expeditionary
Communication Squadron
----
95.1.4. Contingency Response
Wing (CRW)
----
95.1.5. Engineering & Installation
Squadron (E&I)
----
96.1.1. Deployment Process
Overview
----
96.1. Concepts of Aerospace Expeditionary Force (AEF) Employment
94. CABLE AND ANTENNA SYSTEMS CAREER FIELD
TR: AFECD, AFH 33-337; AFGM2018-17-02, 31 May 2018, AFI 36-2101; 1D7X3C CFETP; TO 00-33A-1001-WA-1
94.3. Air Force Specialty Code 1D7X3C
95. CYBERSPACE ORGANIZATIONAL SUCTURE
TR: AFPD 10-17; AFGM2018-17-02, 31 May 2018, 38-101, https://cs.eis.af.mil/a6/default.aspx
95.1. Air Force Units
96. EXPEDITIONARY COMMUNICATIONS
TR: https://aef.afpc.randolph.af.mil, https://jkodirect.jten.mil/Atlas2/faces/page/login/Login.seam; AFIs 10-401, 10-403, 21-109, 33-201 (V2), 23-101
93. MANPOWER AND ORGANIZATION
TR: 1D7XX Learning Program (AF e-Learning); AFPD 38-1; AFIs 38-101, 38-101
1D7XX/X STS (Legacy)
70
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
96.1.2. Deployment Planning and
Execution
----
96.1.3. Unit Type Codes (UTC)
----
97.1.1. DoD Information Network
(DoDIN)
----
97.1.2. Defense Information
Systems Network (DISN)
----
97.1.3. Defense Switched Network
----
97.1.4. Non-Secure Internet
Protocol Router Network
(NIPRNET)
----
97.2.1. Secret Internet Protocol
Router Network (SIPRNET)
----
97.2.2. Defense Red Switch
Network (DRSN)
----
97.2.3. Joint World-Wide
Intelligence Communications
System (JWICS)
----
97.2.4. National Security Agency
(NSA) Network
----
97.3.1. Global High Frequency
Network
----
98.1.1. Definition
----
98.1.2. Background
----
98.1.3.1. Open Conversations
----
98.1.3.2. Short Message Services
(i.e. texting)
----
98.1.3.3. Social Media
----
98.1.3.4. Family/Friends
----
98.1.3.5. Critical Information
----
98. C4I SECURITY
TR: ACP 122; AFIs 33-129,33-138, 33-332; AFKAG-1&2; AFMAN 33-326; DOD Manuel 5200.01 Volume 1; TO 31S5-4-7205 -8-1 PKI Fundamentals
98.1. Operations Security (OPSEC)
TR: AFI 10-701; AFPD 10-7
98.1.3. Vulnerabilities
97. ENTERPRISE SYSTEMS/PROGRAMS
TR: AFI 13 Series, CJCSI 6211.02C, Joint Pub 6-0
97.1. Define Non-Secure Networks
97.2. Define Secure Networks
97.3. Nuclear Command and Control Systems
TR: CJCSI 3231.01B
1D7XX/X STS (Legacy)
71
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
98.2.1. Definition
----
98.2.2.1. Privacy Act (PA)
----
98.2.2.2. Controlled Unclassified
Information (CUI)
----
98.2.2.3. Sensitive Unclassified
----
98.2.2.4. Classified
----
98.3.1. Definition
----
98.3.2. Vulnerabilities
----
98.3.3. Protected Distribution
Systems (PDS)
----
98.3.4. Separation
----
98.4.1. Definition
----
98.4.2. Secure Area Access
Management
----
98.4.3. Facility Security
Requirements
----
99.1. Safety
B---
99.2. Risk Management
B---
99.3. Air Force Consolidated
Occupational Safety Instructions for
AFSC
B---
99.4. Hazards of the AFSC
A---
99.5. Fire Extinguishers
A---
99.6. Understanding First Aid
A---
99.7. CPR
2b---
99.8. Personal and Family
Countermeasures
A---
99.9.1. Maintenance Actions
2b---
99.9.2. Energized Equipment
2b---
98.3. Emission Security (EMSEC)
TR: AFSSI 7700; AFPD 33-2
98.4. Physical Security
TR: AFI 31-101; AFPD 31-1
99. SAFETY/RISK MANAGEMENT (RM)
TR: AFIs 90-802, 91-202, 91-203, 91-302
99.9. Practice Safety Precautions:
98.2. Information Security (INFOSEC)
TR: AFI 31-401 and AFPDs 31-4, 33-2
98.2.2. Information Safeguards
1D7XX/X STS (Legacy)
72
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
99.9.3. High Voltage Equipment
----
100.1.1. US Codes (e.g. Titles 10,
15, 18, 32, 50)
----
100.1.2. US Telecommunications
Laws
----
100.1.3. International Laws
Affecting Electronic
Communications
----
101.1. Department of Defense
(DOD)/Joint Publications
TR:
http://www.dtic.mil/whs/directives/co
rres/pub1.html
----
101.2. Air Force Publications
TR: AFI 33-360; AFPD 33-4
----
101.3.1. Instructions
----
101.3.2. Manuals
----
101.3.3. Policy Directives
----
101.3.4. Pamphlets
----
101.3.5. Guidance Memorandums
----
101.4. Locate AF Publications
TR: http://www.e-publishing.af.mil/
----
101.5. Prepare Local Instructions
TR: AFI 33-360 and CCC
SharePoint site
https://usaf.dps.mil/teams/ccc/SiteP
ages/Home.aspx
----
101.6. Report Publication Errors,
Form Deficiencies, and
Improvements
TR: AFI 33-360
----
101.7. Allied Communication
Publications (ACP)
TR: http://www.jcs.mil/Portals/
36/Documents/Doctrine/pubs/jp6_0.
pdf
----
101.8. Commercial/Vendor
Publications
----
100.1. Laws and Ethics
101. UTILIZE PUBLICATIONS AND DIRECTIVES
TR: AFIs 33-360 and 17-series; TOs 00-5-1, 00-33A-1001-WA-1, and other Applicable TO 00-series: https://www.my.af.mil/etims/ETIMS/index.jsp
101.3. AF Publication Types
100. AUTHORITY AND USER RESPONSIBILITIES
TR: AFDD 3-13, Information Operations; Health Insurance Portability and Accountability Act (HIPAA), http://www.dtic.mil/docine/new_pubs/jp3_13.pdf, USC TITLE 10,
18 and 50
1D7XX/X STS (Legacy)
73
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
101.9. DISA Publications
TR: http://www.disa.mil/About/DISA
-
Issuances
----
101.10. Use Publications When
Performing Work
2b---
101.11.1. Describe Technical
Orders
----
101.11.2. Describe Technical
OrderSystem
----
101.11.3. Locate TO Numbers and
Titles in each TO Index
----
101.11.4. Identify Time Compliance
Technical Orders (TCTO)
Procedures and Document
Completion
TR:
https://www.my.af.mil/etims/ETIMS/i
ndex.jsp; AFI 33-150; TO 00-5-15-
WA-1, TO 00-33A-1001-
WA-1; and applicable TCTOs
----
101.11.5. Prepare Local Work
Cards and Checklist
----
101.11.6. Report Technical Order
Improvements
----
101.11.7. Standard Installation
Practices Technical Order (SIPTO)
TR: TO 00-5-1-WA-1
----
101.12. Telecommunications
Industry Association (TIA)
Standards
TR: https://www.tiaonline.org
----
101.13. Building Industry Consulting
Services, International (BICSI)
Standards
----
101.14. Military Standard (MIL STD)
TR:
http://www.dsp.dla.mil/AP_UIL/displ
ayPage.aspx?action=content&conte
ntid= 66
----
102.1.1. Multimeter
A---
102.1.2. Optical Time Domain
Reflectometer (OTDR)
A---
102.1. Identify Principles, Capabilities, Limitations of the Following Test Equipment
101.11. Technical Orders (TO)
102. TEST EQUIPMENT/SPECIALIZED TOOLS
TR: Applicable Equipment Commercial Manual
1D7XX/X STS (Legacy)
74
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
102.1.3. Time Domain
Reflectometer (TDR)
A---
102.1.4. Bit Error Rate Test (BERT)
Set
----
102.1.5. Frequency Counter
----
102.1.6. Network Analyzer
----
102.1.7. Protocol Analyzer
----
102.1.8. Spectrum Analyzer
----
102.1.9. Power Meter
----
102.1.10. RF Signal Generator
----
102.1.11. Insulation Test Set
----
102.1.12. Megaohmeter
----
102.1.13. Built-In Test Equipment
----
102.1.14. Wattmeter
----
102.1.15. Dummy Load
----
102.1.16. Earth Ground Tester
----
102.1.17. Cable and Fault Locator
----
102.1.18. Audible Test Set
----
102.1.19. Premise wire Tester
----
102.1.20. Subscriber Loop Analyzer
----
102.2.1. Multimeter
2b---
102.2.2. OTDR
2b---
102.2.3. TDR
2b---
102.2.4. BERT Set
----
102.2.5. Frequency Counter
----
102.2.6. Network Analyzer
----
102.2.7. Protocol Analyzer
----
102.2.8. Spectrum Analyzer
----
102.2.9. Power Meter
----
102.2.10. RF Signal Generator
----
102.2.11. Insulation Test Set
----
102.2.12. Megaohmeter
----
102.2. Use the Following Test Equipment
1D7XX/X STS (Legacy)
75
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
102.2.13. Built-in Test Equipment
----
102.2.14. Wattmeter
----
102.2.15. Dummy Load
----
102.2.16. Earth Ground Tester
(Ground Resistance)
----
102.2.17. Cable and Fault Locator
----
102.2.18. Audible Test Set
----
102.2.19. Premise Wire Tester
----
102.2.20. Subscriber Loop Analyzer
----
102.3.1. Tone Generator
----
102.3.2. Inductive Amplifier
----
102.3.3. Local Area Network (LAN)
Tester
----
102.3.4. Light Source
----
102.3.5. Transit
----
102.3.6. Fusion Splicer
----
102.3.7. Fiber Optic Source
andMeter
----
102.3.8. Pressure Testing Gauge
----
102.3.9. Multigas Monitor
2b---
102.3.10. Modular Splicing System
----
102.3.11. Tension Meter
----
102.3.12. Receiver and Exploring
Coil
----
103.1.1.1. Patch Panels
----
103.1.1.2. Cabling
----
103.1.1.3. Equipment
----
103.1.1.4. Antennas
--
103.1.1. Installation
102.3. Identify and use the Following Specialized Tools
103. STANDARD PRACTICES
TR: TOs 00-25-234, 31-10-7, 31-10-13, 31-1-141-1; AFI 32-1065, MIL-STD 2000A, American Public Works Association Policy and American National St; TO to Comm
Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/ TO_to_Civilian_Std_X-Reference.xlsx
103.1. State Facts Related to the Following Practices
1D7XX/X STS (Legacy)
76
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
103.1.1.5. Fiber Optics Concepts
----
103.1.2. Configuration
B---
103.1.3. Interconnection
B---
103.1.4. Inspection
----
103.2. Locate Underground Utilities
or Cabling
----
103.3. Identify Underground Utilities
----
103.4. Mark Underground Utilities
----
103.5. EMSEC Suppression
Techniques
----
103.6. Cable Labeling and
Installation Documentation
B---
103.7. Wire Color-Coding
Standards
B---
103.8.1. Copper Cables
----
103.8.2. Coaxial Cables
----
103.8.3. Fiber Optic Cable
----
103.8.4. Interfacing Considerations
(e.g., Pinouts, Signal Format)
----
103.9.1. Grounding
B---
103.9.2. Bonding
B---
103.9.3. Shielding
B---
103.9.4. Lightning Protection
B---
103.10.1. Fundamentals
----
103.10.2. Concepts
----
103.10.3. Handling, Packaging and
Storing
----
103.11.1. Install
----
103.11.2. Remove
----
103.11.3. Perform Inspection and
Maintenance
----
103.8. Explain Land Line Concepts:
103.9. Concepts Installation of:
TR: TO to Commercial X-Reference
103.10. Electrostatic Discharge:
103.11. Equipment Grounding and Lightning Protection:
1D7XX/X STS (Legacy)
77
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
103.12.1.1. Alphanumerics
----
103.12.1.2. Visual Inspection
----
103.13. Basic Troubleshooting
Techniques
----
103.14. Concepts of PMI Process
----
104.1. Amplitude Modulation (AM)
----
104.2. Frequency Modulation (FM)
----
104.3. Phase Modulation (PM)
----
104.4. Pulse Code Modulation
(PCM)
----
104.5. Bandwidth
----
104.6. Light Wave Communications
----
104.7. Asynchronous and
Synchronous Communication
Modes
----
104.8. Error Detection and
Correction
----
105.1. Switched Electrical Power
Systems
----
105.2. Uninterruptible Power
Supplies (UPS)
----
105.3. Batteries
----
105.4. Rectifiers
----
105.5. Inverters
----
105.6. Generators
----
106.1. Cable Plant Classification
B---
106.2. Cable Composition
B---
106.3. Conductor Identification
B---
103.12. Equipment Familiarization:
103.12.1. Locate Equipment Elements
104. COMMUNICATIONS PRINCIPLES
TR: TO 31-1-141 Series
105. ELECICAL POWER SYSTEMS
TR: Commercial Manuals
106. CABLE AND ANTENNA SYSTEMS FUNDAMENTALS
TR: TOs 31W3-10-21 and 31-10 Series; TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%
20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
1D7XX/X STS (Legacy)
78
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
106.4. Procedures to Label and Tag
Cable Systems
b---
106.5. Procedures to Label and Tag
Antenna Systems
b---
106.6. Types and Construction of
Antenna Systems
----
106.7.1. Wave Propagation
B---
106.7.2. Wave Length
B---
106.7.3. Wave Velocity
B---
106.7.4. Antenna Impedance
B---
106.7.5.1. Characteristics
----
106.7.5.2. VSWR Fundamentals
A---
106.8. Physical Characteristics of
Antennas
----
106.9. Frequency Characteristics of
Antennas
----
107.1. Splice Cables Using
ModularSplicing System
----
107.2.1. Straight Splice
----
107.2.2. Bridge Splice
----
107.2.3. Butt Splice
----
107.2.4. Foldback Method
----
107.3.1. Filled Cable
----
107.4.1. Setting Up Splice Point
----
107.4.2. Mechanical Splice Method
----
107.4.3. Fusion Splice Method
----
107.5. Install Fiber Optic Splice
Closures
----
107.6. Clear Cap Conductors
----
107.4. Splice Fiber Optic Cable by:
106.7. Antenna Fundamentals:
106.7.5. Transmission Lines:
107. CABLE SPLICING
TR: TO 31W3-101-21 and 31-10 Series; TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%
20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
107.2. Splice Plastic-Sheath Plastic-Insulated Cable
107.3. Splice Cable:
1D7XX/X STS (Legacy)
79
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
107.7. Install a Connector on a
Sanded Flexible Coaxial Cable
----
107.8. Install a Connector on a
Solid Center Conductor, Semi-
Flexible Coaxial Cable
----
107.9. Make a Cable Section
Replacement
----
107.10. Make a Cable Transfer
----
107.11. Repair Major/Minor Sheath
Damage on a Non- Pressurized
Plastic- Sheath Cable
----
107.12. Make Cable Count
Changes
----
107.13. Install Temporary Bonds
----
108.1.1. End Cap
----
108.1.2. Cured Rubber (CR) Tape
----
108.1.3. Stainless Steel Closure
----
108.2.1. Temporary Seal
----
108.2.2. Stainless Steel Closure
Method
----
109.1. Install Main Distribution
Frame (MDF)
----
109.2. Install Central Office Stubbed
Protectors
----
109.3. Install Central Office
Unstubbed Protectors
----
109.4. Install Tip Cables
----
109.5. Terminate Conductors on an
MDF
----
109.6. Stencil an MDF with the
Proper Information
----
109.7.1. Buried Distribution
Systems
----
109.7. Install Protected Terminals and Housings in:
108. CABLE SEALING
TR: TO 31W3-101-21
108.1. Seal Cable Ends
108.2. Seal Splice Opening
109. CABLE TERMINATION
TR: TO 31-10-7; TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%
20Systems/TO_to_Civilian_Std_X-Reference.xlsx
1D7XX/X STS (Legacy)
80
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
109.7.2. Aerial Distribution Systems
----
109.7.3. Building Distribution
Systems
----
109.8.1. Buried Distribution
Systems
----
109.8.2. Aerial Distribution Systems
----
109.8.3. Building Distribution
Systems
----
109.9.1. Splicer Support
Shelf/Patch Panel
----
109.9.2. Splice ay Configuration
----
109.10.1. Epoxy Connectors
----
109.10.2. Crimped Connectors
----
109.11. Label Terminals with the
Proper Information
----
109.12.1. Mechanical Method
----
109.12.2. Wire Wrap Method
----
109.12.3. Terminate Conductors
Using the Punch-Down Method
----
109.12.4. Crimp Method
----
109.12.5. Hot Melt Type Connector
----
110.1. Inspect Climbing Equipment
----
110.2. Adjust Climbing Equipment
----
110.3. Prepare Work Area by
Inspecting Poles and Surrounding
Area
----
110.4. Climb/Work Aloft on an
Unstepped Pole
----
110.5. Climb/Work Aloft on a
Stepped Pole
----
110. PRINCIPLES OF WORKING ALOFT
TR: TOs 31-10-3, 31-10-19, 31W3-101-21, 32-1-101; TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7% 20-
%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
109.8. Terminate Cable on Protected Terminals in:
109.9. Terminate Fiber Optic Cable Using:
109.10. Install Connectors on Fiber Optic Cable:
109.12. Perform Terminating Techniques Using the:
1D7XX/X STS (Legacy)
81
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
110.6. Climb/Work Aloft on a Tower
----
110.7.1. Pole top
----
110.7.2. Tower
----
110.8. Perform Standard Hand
Signals
----
111.1. Principles of an Aerial Cable
System
----
111.2.1. Install Continuous
Lightning Protection
----
111.2.2. Install Non- Continuous
Lightning Protection
----
111.3. Install Anchors
----
111.4.1. Temporary
----
111.4.2. Permanent
----
111.5. Install Poles Using the
Construction Vehicle (Crane, Low-
Pro, Mid- Pro) Method
----
111.6. Secure Tools and Equipment
at Working Height
----
111.7. Install Suspension Sand
----
111.8. Remove Suspension Sand
----
111.9. Remove Two Spans of Aerial
Cable and Associated Hardware
----
111.10. Install Cable Supports
----
111.11. Inventory Material for a Self-
Supporting Tower
----
111.12. Install Self- Supporting
Antenna Sections Using a
Construction Vehicle (Crane, Low-
Pro, Mid- Pro)
----
111.13. Remove Self- Supporting
Antenna Sections Using a
Construction Vehicle (Crane, Low-
Pro, Mid- Pro)
----
110.7. Perform Rescue Procedures
111. AERIAL CABLE SYSTEMS
TR: TOs 31-1-141 Series, 31-10-3, 31-10-14, 31W3-101-21, 31R2-2GRC-1232; EIDR-700-7; Applicable Commercial Manuals; TO to Comm Std X- Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X- Reference.xlsx
111.2. Installing Lightning Protection:
111.4. Install Antenna Support Guys:
1D7XX/X STS (Legacy)
82
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
111.14. Plumb Antenna Supports
Using the Plumb Bob Method
----
111.15. Safety Climb Device
Installation
----
112.1. Enter a Confined Space
b---
112.2.1. Place Warning Devices,
Manhole Guards and Personnel
2b---
112.2.2. Test Subterranean
Atmosphere
2b---
112.2.3. Identify Manhole
Classification
----
112.2.4. Prevent Entrance of Water
b---
112.2.5. Ventilate Subterranean
Structures
2b---
112.2.6. Monitor the Air Quality at
Required Intervals While Working in
a Confined Space
2b---
112.2.7. Set Up Ground Tents
----
112.2.8. Perform Manhole Rescue
Procedures
2b---
112.2.9.1. MEP Principles
B---
112.2.9.2. Describe MEP Elements
----
112.2.9.3. Develop MEP
----
112.3. Install a Continuous Duct
Rod in Conduit Between Runs
----
112.4. Clean Cable Ducts
----
112.5. Install Pulling-In Rope
----
112.6.1. Core Hitch
----
112.6.2. Cable Grip
----
112.7. Prepare Cable-Pulling
Apparatus at Manhole Opening
----
112. UNDERGROUND CABLE SYSTEMS
TR: TO 31-10-3; TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%
20Systems/TO_to_Civilian_Std_X-Reference.xlsx
112.2. Prepare Subterranean Work Area
112.2.9. Master Entry Plan (MEP)
TR: AFI 91-203, chap 23
112.6. Prepare Cable Ends For Pulling Using a:
1D7XX/X STS (Legacy)
83
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
112.8. Test the Length of Cable on
a Reel
----
112.9. Match a Specified Pulling
Length of Cable to an Engineered
Project Drawing
----
112.10. Install Cable Racks
----
112.11. Install Copper Core Cable
----
112.12. Remove Copper Core
Cable
----
112.13. Install an Underground
Fiber Optic Inner Duct/ Mesh Fabric
----
112.14. Install an Underground
Fiber Optic Cable
----
112.15. Remove Fiber Optic Cable
----
112.16. Install a Pulling Frame,
Sheave and Sheave Shackle over a
Manhole Opening
----
112.17. Install a Cable Through Two
Manhole Runs With One 90-
Degree Turn using a Cable Reel
Truck
----
112.18. Remove Cable From Two
Manhole Runs With One 90-Degree
Turn using a Cable Reel Truck
----
112.19.1. Hand
----
112.19.2. Using Cable Jacks
----
112.19.3. Using Bending Springs
----
112.20.1. Permanent Method
----
112.20.2. Temporary Method
----
112.21. Install Bonding Ribbon in
Subterranean Structures
----
112.22. Bond Cable in
Subterranean Structures
----
112.23. Bond a Stainless Steel
Closure in a Manhole
----
112.24. Tag Cable in Subterranean
Structures
----
112.20. Rack Cable in Subterranean Structures Using the:
112.19. Form Cable in Subterranean Structures by:
1D7XX/X STS (Legacy)
84
Atch 7
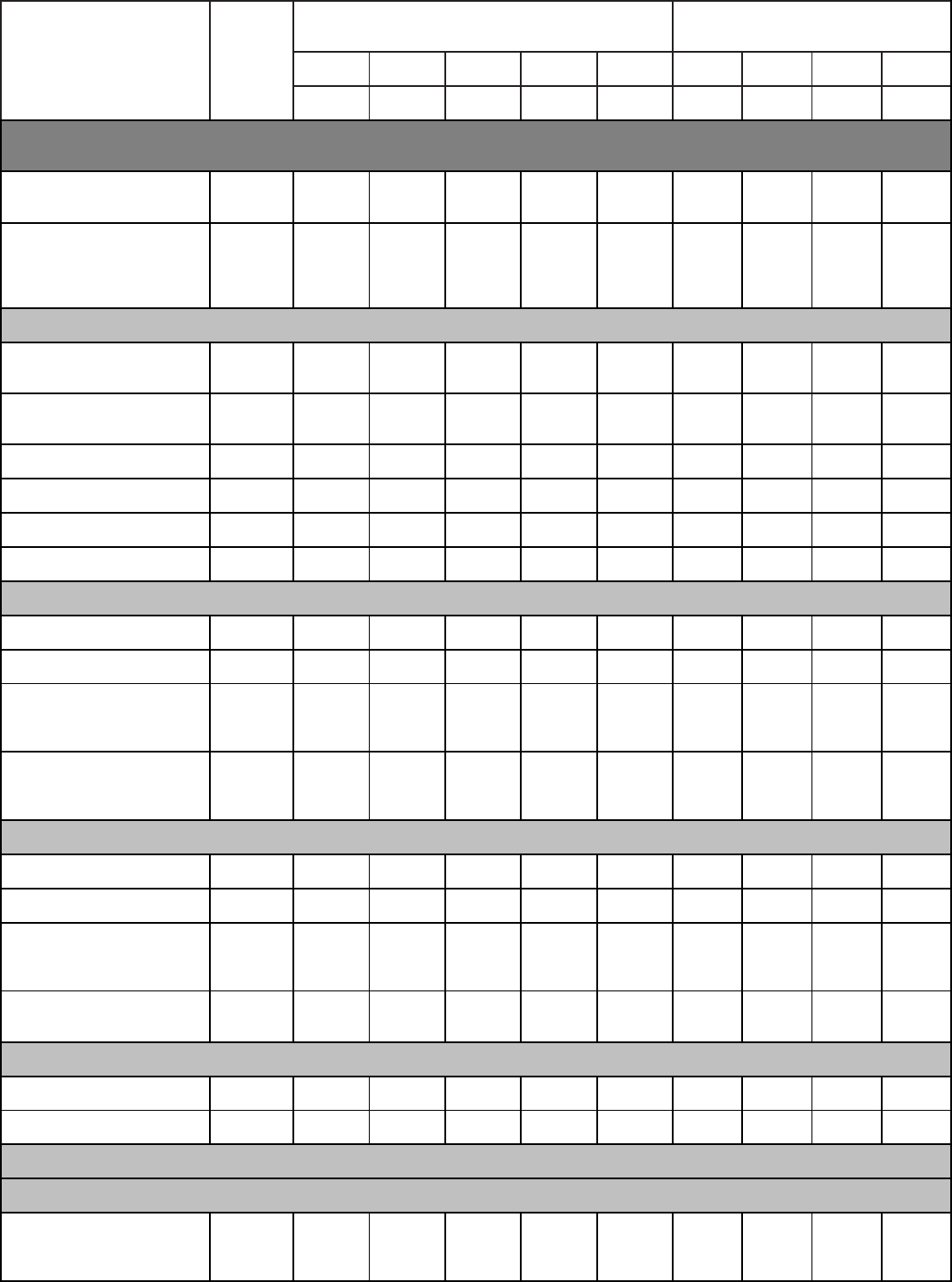
ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
113.1. Mark Buried Cable Path Prior
to Digging
2b---
113.2. AF Form 103 Clearance
Permit Through Base Civil
Engineering (BCE) Prior to Digging
b---
113.3.1. Locate an Existing Cable
----
113.3.2. Determine the Depth of a
Cable
----
113.4. Excavate Cable
----
113.5. Set Up Cable for Splicing
----
113.6. Set Up a Ground Tent
----
113.7. Protect Cable Plant
----
113.8.1. Copper Core Cable
----
113.8.2. Fiber Optic Cable
----
113.9. Prepare a Splice Pit for
Splicing a Cable using the Single-
Offset Method
----
113.10. Prepare a Splice Pit for
Splicing a Cable using the Double-
Offset Method
----
113.11.1. Manual Method
----
113.11.2. Mechanical Method
----
113.11.3. Backfill a Cable Trench
for a Base Distribution System
----
113.11.4. Backfill a Splice Pit for a
Base Distribution System
----
113.12.1. Manual Method
----
113.12.2. Mechanical Method
----
113.13.1.1. Install a Copper Core
Cable using the Open Trench
Method
----
113.12. Install Cables Using the:
113.13. Install Buried Cables to Include:
113.13.1. Copper Core
113. BURIED CABLE SYSTEMS
TR: TO 32-1-101-WA-1
113.3. Locate Existing Buried Cables Using Test Equipment
113.8. Prepare Splice Pit and Trench for:
113.11. Backfill Splice Pits and Trenches using the:
1D7XX/X STS (Legacy)
85
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
113.13.1.2. Install a Copper Core
Cable using the Cable Plow Method
----
113.13.2.1. Flexible
----
113.13.3. Control Cable
----
113.13.4.1. Install a Buried Fiber
Optic Inner- Duct
----
113.13.4.2. Install a Buried Fiber
Optic Cable using the Plow Method
----
113.13.4.3. Install a Buried Fiber
Optic Cable using the Trench
Method
----
113.14. Install Cable Markers
----
113.15.1. Types of Cable Route
Markers
----
113.15.2. Marking Standards of a
Cable Route Marker
----
113.15.3. Placement Requirements
of a Cable Route Marker
----
113.16.1. Place a Cable using
Cable Reel Jacks
----
113.16.2. Place a Cable using
Cable Reel Stands
----
113.16.3. Use a Cable Trailer to
Place a Cable Reel
----
114.1. Theory of Fiber Optic
Lightwave Communication
B---
114.2.1. Single Mode Fibers
----
114.2.2. Multimode Fibers
----
114.2.3. Tight-Tube
----
114.2.4. Loose-Tube
----
114.2.5. Hybrid Fiber Optic Cable
----
113.15. Cable Route Markers
113.16. Cable Reel
114. FIBER OPTICS
TR: TO 31-10-34; TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%
20Systems/TO_to_Civilian_Std_X-Reference.xlsx
114.2. Characteristics of Fiber Optic Cable Types
113.13.2. Coaxial:
113.13.4. Fiber Optic
1D7XX/X STS (Legacy)
86
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
114.3.1.1. Measure the Length of a
Fiber Optic Cable
----
114.3.1.2. Measure the Db Loss of
a Fiber Optic Cable
----
114.3.2.1. Measure the Db Loss of
an Optical Fiber
----
114.4.1. Interior Building Fiber Optic
Cable
----
114.4.2. Fiber Optic Splice
Enclosure
----
114.5.1. Mechanical Splices
----
114.5.2. Optical Fusion Splicer
----
114.5.3. Arrange Fiber Optic
Splices in a Splice tray
----
114.6.1. Terminate at Patch Panel
----
114.6.2. No Polish-Type Pre-
Polished Connector
----
114.6.3. Small Form Connectors
----
115.1. Wire Transmission Principles
----
115.2. Measure Insulation
Resistance
2b---
115.3.1. Loop Resistance
----
115.3.2. Say Voltage
----
115.4.1. Multimeter
----
115.4.2. Cable Fault Detector
----
115.5.1. Multimeter
----
115. CABLE TESTING
TR: TOs 31-1-141-1, 33A1-12-1300-1, 33A1-12-310-1; Applicable Commercial Manuals
115.3. Use a Multimeter to Measure:
115.4. Detect Cable Faults Using a:
115.5. Detect Splicer’s Errors Using a:
114.3.1. OTDR
114.3.2. Optical Power Meter
114.4. Install Fiber Optic Cable
114.5. Splice Fiber Optic Cable
114.6. Install Fiber Optic Connections
114.3. Test Cables Using:
1D7XX/X STS (Legacy)
87
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
115.5.2. Tone Set
----
115.6.1. Multimeter
----
115.6.2. Tone Set
----
115.7. Locate Earth Return Faults in
Non- Working Cable using the
Cable and Fault Locator Test Set
----
115.8. Locate Non- Resistive Cable
Faults on Non-Working Cable using
a Subscriber Loop Analyzer Test
Set
----
115.9. Locate Resistive- Type
Faults on a Non- Working Cable
using a Subscriber Loop Analyzer
Test Set
----
115.10. Locate Split Pairs Faults
using a Subscriber Loop Analyzer
Test Set
----
115.11.1. Tone Set and Amplifier
----
115.11.2. Multimeter
----
115.12.1. Tone Set, Exploring Coil
and Amplifier
----
115.12.2. Fault Locator
----
115.12.3. Open Fault Locator
----
115.12.4. TDR
----
115.13. Locate Cable Faults in a
Working Cable Section using a
Subscriber Loop Analyzer Test Set
----
115.14. Types of Splice Errors
B---
115.15. Measure Resistance of
Station Grounds
----
115.16. Record Station Ground Test
Data on Applicable Forms
----
116.1.1. International Standards
Organization (ISO) Open Systems
Interconnect (OSI) Model
----
115.11. Identify Conductors in Working Cable using a:
115.12. Locate Cable Faults Using a:
116. LOCAL AREA NETWORK/WIDE AREA NETWORK (LAN/WAN) DISIBUTION SYSTEMS
TR: Commercial Manuals, EIA/TIA 569, 570; TIA/EIA 568A, 606, 607, TSB 67, TSB 72, AF e-Learning
116.1. Theory of the Following LAN/WAN Distribution Systems:
115.6. Identify Conductors in Non-Working Cable Using a:
1D7XX/X STS (Legacy)
88
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
116.1.2. Topology of LAN/WAN
Distribution Systems
----
116.1.3. Use of Multiplexers in
LAN/WAN Distribution Systems
----
116.1.4. Use of Modems in
LAN/WAN Distribution Systems
----
116.1.5. Use of Routers, Hubs and
Servers in LAN/WAN Distribution
Systems
----
116.2.1. Single Mode Fiber Optics
----
116.2.2. Multimode Fiber Optics
----
116.2.3. Unshielded Twisted
Pair\Shielded Twisted Pair
(UTP\STP) (Intra-Building Wiring)
----
116.3.1. Single Mode Fiber Optics
----
116.3.2. Multimode Fiber Optics
----
116.3.3. UTP\STP (Intra- Building
Wiring)
----
116.3.4. Patch Panels and
Associated Hardware
----
116.4.1. Single Mode Fiber Optics
----
116.4.2. Multimode Fiber Optics
----
116.4.3. Patch Panels and
Associated Hardware
----
116.4.4. UTP\STP (Intra- Building
Wiring)
----
116.5.1. Installing Twisted Pair
Connectors
----
116.5.2. Installing Work Area
Outlets
----
116.5.3. Fabricating Patch Cords
----
116.5.4. Installing Cable Methods
in/through Protected Distribution
System (PDS)
TR: NSTISSI_7003,
https://www.cnss.gov/CNSS/
----
116.3. Install LAN/WAN Distribution Systems to include:
116.4. Maintain LAN/WAN Distribution Systems to include:
116.5. Terminate LAN/WAN Cables by:
116.2. Types of LAN/WAN Transmission Methods:
1D7XX/X STS (Legacy)
89
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
117.1. Install Cross-Connects on
Distribution Frames
----
117.2. Terminate Sapping
Connections
----
117.3. Install Cross-Connects for
Premise
----
117.4. Perform System Operational
Test to Validate Installation
----
117.5. Perform System Corrective
Maintenance
----
118.1. Principles of Intra-Building
Wiring Distribution System
B---
118.2. Installation Principles and
Associated Hardware
B---
118.3. Install, Route, Form,
Terminate and Label
Cables/Associated Wiring
----
118.4. Test Distribution System
----
118.5. Install Racks, Patch Panels
and Wire Management Systems
----
118.6. Principles of-Certify and
Document Distribution System
----
118.7. Install, Route, Form,
Terminate and Label
Cables/Associated Wiring in a
Protected Distributions System
----
119.1. Driver Safety Practices
----
119.2. Inspect for Proper
Configuration of Tools, Parts and
Materials
----
119.3. Purpose and Use of Special
Purpose/ Construction Vehicles
----
119.4.1. Line Trucks
----
119.4.2. Low Profile
----
119. OPERATE AND MAINTAIN SPECIAL PURPOSE VEHICLES
TR: AFI 24-301; AFI 91- Series; TO36A11-18 Series
119.4. Perform Operator Maintenance on Special Purpose Vehicles and Accessories to include:
117. TELEPHONY DEVICES INSTALLATION AND MAINTENANCE
TR: TOs 31-10-7, 31-10-13, TIA/EIA 568A & 569; TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7% 20-
%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
118. INTRA-BUILDING DISIBUTION SYSTEMS
TR: EIA/TIA 568 Series, TIA/EIA 606, Tele-communications System Bulletin (TSB) – 67, 606 Standard; TO 00-33D-3003-WA-1; TO to Comm Std X-Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X- Reference.xlsx
1D7XX/X STS (Legacy)
90
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
119.4.3. Cable Reel Truck
----
119.4.4. Trenchers
----
119.4.5.1. Hydraulic
----
119.4.5.2. Non-Hydraulic
----
119.4.6. Forklift
----
119.4.7. Backhoes
----
119.4.8. Pole Trailers
----
119.4.9. Tractor and Trailer
----
119.4.10. Cable Plow
----
119.4.11. Combination Pole and
Cable Trailer
----
119.4.12. Fiber Optic Splicing
Trailer
----
119.4.13. General Power
Component (GPC) Utility Trailer
----
119.5.1. Line Trucks
----
119.5.2. Low Profile
----
119.5.3. Cable Reel Truck
----
119.5.4. Trenchers
----
119.5.5.1. Hydraulic
----
119.5.5.2. Non-Hydraulic
----
119.5.6. Forklift
----
119.5.7. Backhoes
----
119.5.8. Pole Trailers
----
119.5.9. actor and Trailer
----
119.5.10. Cable Plow
----
119.5.11. Combination Pole and
Cable Trailer
----
119.5.12. Fiber Optic Splicing
Trailer
----
119.5.13. General Power
Component (GPC) Utility Trailer
----
120. CABLE AND ANTENNA SYSTEMS COMMON MAINTENANCE PRACTICES
TR: AFI 91-203; TOs 31-10-3, 31W3-10-21, 36A11-18 series; TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-
%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
119.4.5. Cable Trailers:
119.5. Operate Special Purpose Vehicles and Accessories to include:
119.5.5. Cable Trailers:
1D7XX/X STS (Legacy)
91
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
120.1.1.1. Electrical
----
120.1.1.2. Mechanical
----
120.1.2. Generators
----
120.1.3. Blowers
----
120.1.4. Heaters
----
120.2.1. Pneumatic
----
120.2.2. Powder
----
120.2.3. Electric
----
120.3. Types of Fiber Ropes
B---
120.4. Care of Fiber Ropes
b---
120.5. Explain how Fiber Ropes are
used in this AFSC
----
120.6.1. Crown
----
120.6.2. Eye
----
120.6.3. Long
----
120.6.4. Short
----
120.7.1. Square
----
120.7.2. Bowline-on-a-Bight
----
120.7.3. Sheetbend
----
120.7.4. Bowline
2b---
120.7.5. Double Bowline
2b---
120.7.6. Intermediate Bowline
----
120.8.1. Clove
2b---
120.8.2. Timber
----
120.8.3. Snubbing
----
120.9. Rolled Eye Wire Rope Splice
----
120.10.1. Most Common Types
----
120.7. Tie Knots in Fiber Ropes
120.8. Tie Hitches in Fiber Ropes
120.10. Wire Rope
120.1. Utilize Auxiliary Equipment to include:
120.1.1. Water Pumps:
120.2. Use Power Actuated Tools to include:
120.6. Splice Fiber Ropes
1D7XX/X STS (Legacy)
92
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
120.10.2. Most Common Uses
----
120.10.3. Caring For
----
120.11. Use Rigging Techniques to
Install Antenna and Cable Systems
----
120.12. Load and Unload Cable
Reels
----
120.13.1. Aerial Construction
----
120.13.2. Buried Construction
----
120.13.3. Underground
Construction
----
120.13.4. Cable Reel Jacks
----
120.13.5. Cable Reel Stand
----
120.13.6. Cable Trailer
----
120.14. Identify the Purpose and
Use of Common Hand Tools
----
120.15. Maintain Common Hand
Tools for Safe Use
b---
120.16. Identify the Purpose and
Use of Construction Tools
----
120.17. Maintain Construction Tools
----
120.18. Identify Purpose of
Construction Equipment
----
120.19. Maintain Construction
Equipment
----
121.1. Antenna Fundamentals
B---
121.2. Transmission Line
Fundamentals
B---
121.3. Antenna Types and
Characteristics
B---
121.4.1. Maintain Guys
----
121.4.2. Maintain Anchors
----
121.5.1. Hazard Lights
----
121.4. Non-Self-Supporting Antenna Systems
121.5. Maintain Hazard Markings:
120.13. Position Cable Trucks/Reels for:
121. ANTENNA SYSTEMS
TR: TOs 31-1-141 Series, 31-10-14, 31R2-2GRC-1232, 31-10-3, 31R5-4-142-2; TO to Comm Std X-Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
1D7XX/X STS (Legacy)
93
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
121.5.2. Warning Signs, Symbols
and Markings
----
121.6.1. Site Anchor Locations
----
121.6.2. Establish Datum Lines
----
121.7.1. Radiators
----
121.7.2. Reflectors
----
121.7.3. Rotator Controls
----
121.7.4. Azimuth Controls
----
121.7.5. Mechanical Controls
----
121.7.6. Antenna Support Hardware
----
121.8. Align Reflectors
----
121.9.1. Radiators
----
121.9.2. Reflectors
----
121.9.3. Rotator Controls
----
121.9.4. Azimuth Controls
----
121.9.5. Mechanical Controls
----
121.9.6. Antenna Support Hardware
----
121.10.1. Load and Unload
----
121.10.2. Transport Antenna
Support Poles
----
121.11.1. Construction Vehicle
----
121.11.2. Crane
----
121.12.1. Construction Vehicle
----
121.12.2. Crane
----
121.13.1. Radiators
----
121.13.2. Reflectors
----
121.13.3. Rotator Controls
----
121.10. Antenna Support Poles:
121.11. Install Antenna Support Pole:
121.12. Remove Antenna Support Pole:
121.13. Remove the Following Antenna Components:
121.6. Use a Transit to:
121.7. Install the Following Antenna Components:
121.9. Maintain Antenna Components:
1D7XX/X STS (Legacy)
94
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
121.13.4. Azimuth Controls
----
121.13.5. Mechanical Controls
----
121.13.6. Antenna Support
Hardware
----
121.14. Install Antenna Ground
Reflector Systems
----
121.15. Maintain Open Wire
Transmission Lines
----
121.16.1. Install and Remove
----
121.16.2. Align
----
121.16.3. Perform a Scheduled PMI
----
122.1. Tower Climbing
----
122.2. Unstepped Pole
----
122.3. Pole Top Rescue
----
122.4. Tower Rescue
----
122.5. Manhole Rescue
----
122.6. Confined Space Certification
----
123.1.1. Flexible
----
123.1.2. Rigid
----
123.2.1. Flexible Coaxial Cable
----
123.2.2. Flexible Waveguide
----
123.3.1. Flexible
----
123.3.2. Rigid
----
123.4.1. Flexible
----
123.4.2. Rigid
----
123.4. Maintain Waveguides:
122. CLIMBING CERTIFICATIONS/ RESCUE PROCEDURES
TR: AFI 91-203, OSHA 1910.146, 1926; TOs 31-10-3, 31-10-19, 31W3-10-21; TO to Comm Std X-Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
123. ANTENNA SYSTEMS INSTALLATION AND MAINTENANCE
TR: AFI 33 Series; TOs 31-1-141 Series, 31-10 Series, 33A1-15-39-1, 00-33D-3004-WA-1 and Applicable Technical Data; TO to Comm Std X-Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
123.1. Maintain RF Coaxial Cables:
123.2. Install Connectors on:
123.3. Install Waveguides:
121.16. Parabolic Microwave Dish:
1D7XX/X STS (Legacy)
95
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
123.5.1. Flexible
----
123.5.2. Rigid
----
123.6.1. Coaxial cables
----
123.6.2. Antennas
----
123.6.3. Support Structures
----
123.6.4. Antenna Hardware
----
123.6.5. Grounding Systems
----
123.7.1. Install Antenna Systems
----
123.7.2. Maintain Antenna Systems
----
124.1. Update a Communications
Mission Data Set
2b---
124.2. Configuration Accounting
Information Retrieval System
(CAIRS)
TR: Commercial Publications
----
125.1.1. Direct Current (DC)
----
125.1.2. Alternating Current (AC)
----
125.1.3. Inductors and Capacitors
----
126.1. Housekeeping
----
126.2.1. Manhole
----
126.2.2. Conduit
----
126.3. Prevention of Water
Entrance
----
126.4. Rodding and Cleaning
----
125. ELECTRONIC PRINCIPLES
TR: TO 31-1-141-2-WA-1 Ch. 7, 9, and 10
125.1. Identify Relationships of Basic Facts Associated with:
126. MANHOLE PREVENTIVE MAINTENANCE INSPECTION (PMI)
TR: AFI 91-203; TOs 31W3-10-21, 31-10-6, 31-10-13, 31-10-12, 31-10-3; TO to Comm Std X-Reference:
https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
126.2. Minor Repairs
123.5. Remove Waveguides:
123.6. Perform Scheduled PMIs on:
123.7. Use Project Support Documentation and CSIRs to:
124. COMMUNICATIONS DISIBUTION MAPS, RECORDS AND DIAGRAMS
TR: TOs 00-33D-3004-WA-1 and 00-33D-3003-WA-1
1D7XX/X STS (Legacy)
96
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
126.5.1. Grounding
----
126.6. Detection/ Prevention of
Corrosion in Underground Plant
----
126.7. Update CSIR Drawings
----
126.8.1. Racks/Supports
----
126.8.2. Conduits
----
126.8.3. Tags/Markings
----
126.9. Safety
----
127.1. Pole Condition
----
127.2. Pole Grounding
----
127.3. Corrosion Prevention
----
127.4. Install Pole
----
127.5. Pole Attachments
----
127.6. Pole Guyed Attachments
----
127.7. Markings
----
127.8. Tower Condition
----
127.9. Tower Grounding
----
127.10. Corrosion Prevention
----
127.11. Tower Attachments
----
127.12. Tower Guyed Attachments
----
127.13. Anchors
----
127.14. Markings
----
127.15. Transmission Lines
----
127.16. Antenna Testing
----
127.17. Safety
----
128.1. Equipment Location
----
128.2. Racks/Cabinets
----
126.8. Quality Assurance
127. TOWER/POLE PREVENTIVE MAINTENANCE INSPECTION (PMI)
TR: T.O. 31-10-19, 31-10-21,1-1-700, 31-10-21, 31-10-19, 31-10-28, 31R-10-5, 31-1-141-11, 31-1-141-12, 31-10-3, National Electric Code (NEC); TO to
Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-%20Cable%20and%20Antenna%20Systems/ TO_to_Civilian_Std_X-
Reference.xlsx
128. CABLE MANAGEMENT
TR: T.O. 31-10-19, 31-1-75, 31-10-6, 31-10-13, 31-10-12, 31W3-10-22, 31-10-13, 00-25-245, 31-10-14, 31-10-34, 31-10-7, 31-10-7; ANSI/EIA/TIA 568B,
BITSEP Handbook, National Electric Code (NEC); TO to Comm Std X-Reference: https://cs2.eis.af.mil/sites/10445/AFKN_Docs/CFETP/3D1X7%20-
%20Cable%20and%20Antenna%20Systems/TO_to_Civilian_Std_X-Reference.xlsx
126.5. Maintenance and Repair of Cable Bonds
1D7XX/X STS (Legacy)
97
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
128.3. Grounding
----
128.4. Conduit
----
128.5. Marking
----
128.6. Fanning/Forming
----
128.7. Cable for Fixed Ground C-E
Equipment
----
128.8. Terminations
----
129.1.1. Report Resources Status
----
129.1.2. Document Actions
----
129.1.3. Develop Work Schedules
----
129.1.4. Equipment Readiness
----
129.1.5. Staffing and Utilization
----
129.2.1. Evaluate Newly Assigned
Personnel and Identify Individual
Training Requirements
TR: AFI 36-2651; AFI 33-150;
Applicable CFETP; Unit Training
Manual
----
129.2.2. Conduct On-the- Job
Training (OJT)
TR: AFI 36-2651; Local Directives
----
129.2.3. Evaluate Quality of OJT
and Provide Trainee Feedback:
TR: AFI 36-2651
----
129.2.4. Develop Master Training
Plan
----
129.3.1. Describe the QA Function
----
129.4.1. Unit Effectiveness
Inspection
----
129.4.2.1. Work Center Role
----
129.2. Training
129.3. Quality Assurance (QA)
129.4. Air Force Inspection System (AFIS)
TR: AFI 90-201, MPTO 00-33A-1001-WA-1
129.4.2. Self-Assessment Program
129. WORK CENTER MANAGEMENT
TR: AFJQS XXXXX-212S, AFI 10-201, AFI 21- 103, AFI 36-807, Ch 4. and TO 00-33A-1001
129.1. Management Policies
1D7XX/X STS (Legacy)
98
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
129.4.2.2. QA Role
----
129.4.2.3. Self- Assessment
Checklist (SACS)
----
129.4.2.4. Management Internal
Control Toolset (MICT)
----
129.5.1. Integrated Maintenance
Data System (IMDS)
----
129.5.2. Remedy
----
129.5.3. Defense Property
Accountability System (DPAS)
----
129.5.4. myTraining
----
129.6.1. Submit Price Challenges
----
129.6.2. Report Item and Packaging
Discrepancies
TR: AFJAM 23-215
----
129.6.3. Report Uniform Source,
Maintenance and Recoverability
Code and Air Force Expendability,
Recoverability, Reparability
Category Code Discrepancies
----
129.6.4. Submit Deficiency Reports
TR: TO 00-35D-54-WA-1, chap 3
----
129.6.5. Research and Identify Part
and Stock Numbers
----
129.6.6. Maintain Supply Listings
and Reports (D04, D18, M30, D23,
or equivalent IMDS)
----
129.6.7. Maintain Bench Stock
----
129.6.8. Maintain Supply Point
Stock
----
129.6.9. Request and Validate
Adjusted Stock Levels
----
129.6.10. Describe Procedures for
Recovering and Turning in Precious
Metals
----
129.6.11. Process and Control
Repair Cycle Assets Due in For
Maintenance (DIFM)
----
129.6.12. Initiate Not Repairable
This Station (NRTS) Actions
----
129.6. Logistic Support
TR: AFI 23-101
129.5. Automated Information Systems (AIS)
1D7XX/X STS (Legacy)
99
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
129.6.13. Initiate Contract Repair
(AF Form 9)
----
129.6.14. Maintain Custodian
Authorization/Custody Receipt
Listing (CA/CRL) Equipment
Accounts
----
130.1.1. AF Career Field Manager
TR: CFM Handbook
----
130.1.2. MAJCOM Functional
Manager
TR: MFM Handbook
----
130.1.3. Base Functional Manager
----
130.2.1. Roles and Responsibilities
of Supervising Gov't, Civ, or
Contract Personnel
----
130.2.2. Roles and Responsibilities
of each Communications Squadron
Work Center
----
130.2.3. Principles of Retraining
Programs
----
130.2.4. Plan and Organize
Maintenance Activities
----
130.2.5. Direct Systems Analysis,
Design, Programming, Operations
and Maintenance
----
130.2.6. Direct Systems
Management, Technical Support,
and Resource Management
----
130.2.7. Manage Plans and Provide
Implementation and Development
Functions in a Maintenance
Environment
----
130.3.1. Utilization and Training
Workshop (U&TW)
----
130.3.2. Occupational Survey
----
130.3.3. Specialty Training
Requirements Team (ST)
----
130.4. Awards and Recognition
130. FUNCTIONAL MANAGEMENT
TR: AFECD; AFIs 33-101, 36-2651, 36-2845, 38-101; AFMAN 37-104 (will convert to AFI 33-396); AFQTP 1D7XX-225E
130.1. Career Field Supervision and Leadership
130.2. Superintendent Duties
130.3. Force Management
1D7XX/X STS (Legacy)
100
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
130.4.1. Unit/Installation Awards
----
130.4.2. A2/6 Special Trophies and
Awards
TR: AFI 36-2845
----
131.1.1. Principles of Financial
Management
----
131.1.2. Program Objective
Memorandum (POM) Cycle
----
131.1.3. Government Purchase
Card Program Oversight
----
131.1.4. Shortfall Procedures
----
131.2.1. Responsibilities
----
131.2.2. Funding Process
----
131.3.1. Responsibilities
----
131.3.2. Funding Process
----
131.3.3. Develop Requirements
----
131.4. Funding Types
----
131.5. Primary and Alternate
Funding Sources
----
131.6. Financial Planning
(FINPLAN)
----
132.1. Manpower Requirements
----
132.2. Air Force Manpower
Standard (AFMS) Application
----
132.3. Manpower Studies
----
132.4.1. Unit Manpower Document
(UMD)
----
132.4.2. Authorization Change
Request (ACR)
----
132.4.3. Organizational Change
Request (OCR)
----
132. MANPOWER AND ORGANIZATION
TR: AFPD 38-2, AFI 38-101, 38-201
132.4. Manpower Products
131. RESOURCE MANAGEMENT
TR: AFPDs 16-5, 33-1, 10-6, 65-6; AFIs 16-501, 10-601, 65-601 V(3)
131.1. Financial Management
131.2. Funded Requirements
131.3. Unfunded Requirements
1D7XX/X STS (Legacy)
101
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
132.4.4. Program Element Code
(PEC)
----
132.4.5. Unit Personnel
Management Roster (UPMR)
----
132.5. Allocating Personnel
----
133.1.1. Lifecycle
----
133.1.2. Procurement
----
133.1.3. Integrated Technical
Reference Model (i-M)
----
133.2.1. Principles of Project
Management
----
133.2.2. Complete AF e- Learning
1D7X3C Project Management
Training Track
TR: https://www.my.af.mil (under
AF e-Learning site)
----
133.2.3.1.
Project/ProgramDocumentation
----
133.2.3.2. Responsibilities
----
133.2.4.1. Project Documentation
Content
----
133.2.4.2. Project Documentation
Review
----
133.2.4.3. Site Surveys
----
133.2.5. System Accreditation
----
133.2.6.1. Characteristics and
Responsibilities Concerning
Support Agreements,
Memorandums of Agreements and
Memorandums of Understanding
----
133.2.6.2. Scheduling Management
----
133.2.6.3. Critical Path
----
133.2.3. Implementing Command/Organization
133.2.4. Requiring Organization
133.2.6. Support Agreements
133. PROJECTS AND REQUIREMENTS FUNCTION
TR: T.O. MPTOs 00-33A-1001-WA-1, 00-33D-3003-WA-1
133.1. IT Requirements
TR: AFI 33-401 and 33-210
133.2. IT/NSS Project Management
TR: AFPDs 33-1, 32-90; AFIs, 32-1021, 32-1022, 32-1023, 32-1032, 33-101, 10-501, 32-9005, 65-106; MPTO 00-33A-1001-WA-1, 00-33D-2002-WA-1, 00- 33D-3003-
WA-1, 00-33D-3004-WA-1
1D7XX/X STS (Legacy)
102
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
133.2.6.4. Project Support
Requirements
----
133.2.6.5. Host
Nation/Federal/State/Local
Requirements/Coordination
----
133.2.6.6.1. Prepare Base Civil
Engineering (BCE) Work Request
----
133.2.6.6.2. Military Construction
Program (MCP)
TR: EIA/TIA 568A, 569A, 606, 607,
ETL 02-12
----
133.2.6.6.3.1. DD Form 1391
Review
----
133.2.6.6.3.2. Review MCP Design
Package
----
133.2.6.6.3.3. MCP Design Drawing
Symbolism
----
133.2.6.6.3.4. Compliance with ETL
02-12
----
133.2.6.6.3.5. Joint Occupancy
----
133.2.6.6.3.6. Maintenance Work
Center Roles
----
133.2.7. Initial Logistic Support
Actions
----
133.2.8.1. Liaison with Base
Agencies
----
133.2.8.2. Support Documentation
----
133.2.8.3. Project Material
----
133.2.8.4. Integrated Logistics
Support Completion
----
133.2.9.1. Focal Point for
Implementation Teams
----
133.2.9.2. Project Monitor
Responsibilities
----
133.2.10.1. Schedule Systems
Acceptance Inspections
----
133.2.8. Implementation
133.2.9. Implementation Support
133.2.10. Project Acceptance and Completion Actions
133.2.6.6. Support Construction
133.2.6.6.3. Construction Design Reviews
1D7XX/X STS (Legacy)
103
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
133.2.10.2. Material Accountability
----
133.2.10.3. Material Disposition
----
133.2.10.4. Real Property Transfer
----
133.2.10.5. Acceptance
Documentation
----
133.2.11. Exceptions
----
134.1.1.1. Purpose
----
134.1.1.2.1. Locate Information
within Architecture Views
----
134.1.1.2.2. DOD IT Standards
Registry (DISR)
----
134.1.1.2.3. Air Force
Communications and Information
Info-structure Technical Reference
Model (I -M)
----
134.1.2. Cyberspace Systems
Integrator (CSI) Concept
TR: MPTO 00- 33D-2002
----
134.1.3.1. Purpose
----
134.1.3.2. Process
----
134.1.3.3. Maintain CIPS
Visualization Components
----
134.1.3.4. track Project in CIPS
----
134.1.3.5. CIPS CVC tool
----
134.1.3.6. Legacy CSIRs
----
134.1.4. Lead Command
TR: AFI 10-901
----
134.1.5.1. Purpose
----
134.1.1. Architecture
TR: AFPD 33-1; AFIs 33-108, 33-210, 33-401; AFPD 33-4; CJCSI 6212.01;C4ISRDODAF 4630.8; GIG/CRD; MPTOs 00-33A- 1001-WA-1, 00-33D-2002-
134.1.1.2. Department of Defense Architecture Framework
TR: DoDAF Version 2.02 https://dodcio.defense.gov/Library/DoD-Architecture-Framework/
134.1.3. Cyberspace Infrastructure Planning System (CIPS) (e.g. Base IT/NSS Blueprints)
TR: MPTO 00-33A-1001- WA-1, 00-33D-2002-WA-1, 00-33D-3003-WA-1, 00-33D-3004-WA-1; AFPD 33-1
134.1.5. IT/NSS Requirements
TR: AFPDs 10-6 and 33-1; AFIs, 10-601; MPTOs 00- 33A-1001-WA-1,00-33D-2002-WA-1, 00-33D-3003- WA-1, 00-33D-3004-WA-1
134. PLANS, PLANNING AND AGREEMENTS
TR: AFIs, 33-150, 36-2651, 63-501, 63-131, 64-102; AFPD 36-5, 64-1; Federal Acquisition Regulation (FAR) Part 39; OMB Circular A-130; TO 00-33A- 1001-WA-1 and
00-33D-3003-WA-1
134.1. IT/National Security System (NSS) Planning
TR: AFIs 10-501, 10-601, 16-501, ; AFMAN 10-401 (V) 2; AFPDs 10-4, 16-5, 33-1
1D7XX/X STS (Legacy)
104
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
134.1.5.2.1. Purpose
----
134.1.5.2.2. Content
----
134.1.5.2.3. Develop IT/NSS
Requirement Document
----
134.1.5.2.4. Process IT/NSS
Requirements
----
134.1.5.2.5.1. Technical Solutions
----
134.1.5.2.5.2. Identify Provisions for
Logistic Support
----
134.1.5.2.5.3. Types (ICD, CDDP-
Plan, etc)
----
134.1.5.3.1. Purpose
----
134.1.5.3.2. Content
----
134.1.5.3.3. Validate Technical
Solutions Against Applicable
Contracts
----
134.1.5.3.4. Commercial Off-the-
Shelf (COTS) (GSA, DoD,Contracts,
1218)
----
134.1.5.3.5. Government Off-the-
Shelf (GOTS)
----
134.1.5.4. Host Nation Approval
TR: Local Procedures
----
134.1.6.1. Types
----
134.1.6.2. Impacts
----
134.2.1.1. Purpose
----
134.2.1.2. Content
----
134.2.1.3. Develop Plans Annex
----
134.2.2. IT/NSS Point of Contact (POC) for Plans
134.1.5.2.5. Risk Identification
TR: AFPAM 90-902; OMB Circular No. A-130; MPTO 00-33A-1001-WA-1 http://www.whitehouse.gov/omb/
134.1.5.3. IT/NSS Contracts
TR: AFPD 33-1
134.1.6. Planning Meetings
TR: AFPD 33-1; AFI 33-101; T.O. 00-33D-3003-WA-1
134.2. Plans Management
TR: AFPDs 10-4, 10-5; AFIs 10-402, 10-403, 10-404, 10-501, 25-101, 10-201; MPTO 00-33A-1001-WA-1
134.2.1. Types of Plans
134.1.5.2. IT/NSS Documentation
TR: AFPD 33-1; AFIs 33-580, 10-601
1D7XX/X STS (Legacy)
105
Atch 7

ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
134.2.2.1. Evaluate Plans to
Determine IT/NSS Resource Impact
----
134.2.2.2. Adminisatively Manage
Plans
----
134.3.1. Purpose
----
134.3.2. Content
----
134.3.3.1. Base IT/NSS Installation
Records Manager
----
134.3.3.2. Work Centers
----
134.3.4.1. Processing
----
134.3.4.2. Reviews
----
134.3.4.3. Index
----
134.4.1. Purpose
----
134.4.2. Types
----
134.4.3. Content
----
134.4.4. Reviews
----
134.5.1. Control Configuration
----
134.5.2. Initiate Modification
Proposals
TR: AFI 63-131
----
134.6.1. Establishing and Managing
a Contract
----
134.6.2.1. Time and Material
----
134.6.2.2. Firm Fixed Price
----
134.6.2.3. Sole Source
----
134.6.2.4. Performance Based
----
134.6.2.5. Indefinite Delivery
Indefinite Quantity
----
134.5. Modification Management
134.6. Adminisative Contract Management
TR: Federal Acquisition Regulation (FAR), Part 16
134.6.2. Types of Contracts
134.3. IT/NSS Installation Records
TR: MPTOs 00-33A-1001- WA-1, 00-33D-3003-WA-1, 00-33D-3004-WA-1
134.3.3. Responsibilities
134.3.4. Drawing Records
134.4. Agreements
TR: AFIs 25-201, 33-115 (V) 1, 65-601 (V)1, AFPD 25-2; DODI 4000.19; MPTO 00-33A-1001-WA-1
1D7XX/X STS (Legacy)
106
Atch 7
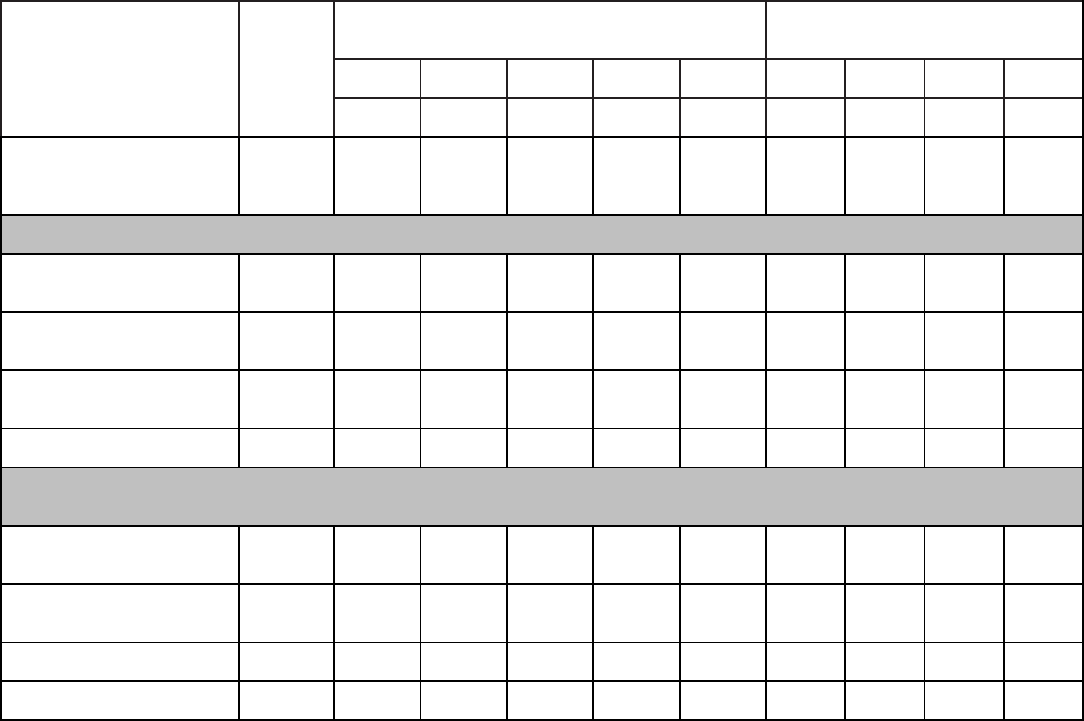
ABCDE
3 SKILL
LEVEL
5 SKILL
LEVEL
7 SKILL
LEVEL
9 SKILL
LEVEL
START
DATE
STOP
DATE
TRAINEE
INITIALS
TRAINER
INITIALS
CERTIFIER
INITIALS
COURSE COURSE COURSE COURSE
1. TASKS, KNOWLEDGE AND
TECHNICAL REFERENCES
2. CORE &
WARTIME
TASKS
3. CERTIFICATION FOR OJT
4. PROFICIENCY CODES USED TO
INDICATE TRAINING/INFORMATION
PROVIDED
134.6.2.6. Blanket Purchase
Agreement (e.g. AFWAY, PCOE)
----
134.6.3.1. Quality Assurance
Program Coordinator
----
134.6.3.2. Functional
Director/Commander
----
134.6.3.3. Quality Assurance
Personnel
----
134.6.3.4. Unit Contract Monitor
----
134.7.1. Unit Focal Point
Responsibilities
----
134.7.2. BCE Work Request
Processing
----
134.7.3. BCE Planning
----
134.7.4. Environmental Impacts
----
134.6.3. Responsibilities
134.7. Base Civil Engineer (BCE) Interface
TR: AFIs 32-1001, 32-1021, 32-9002; AFPD 32-90; MPTO 00-33A-1001-WA-1
1D7XX/X STS (Legacy)
107
Atch 7
