#CiscoLive

#CiscoLive
Mark Stephens, Global Cyber Security Architect
@216stephens
BRKSEC-2128
SASE the SOC’s new BFF

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Cisco Webex App
Enter your personal notes here
Questions?
Use Cisco Webex App to chat
with the speaker after the session
Find this session in the Cisco Live Mobile App
Click “Join the Discussion”
Install the Webex App or go directly to the Webex space
Enter messages/questions in the Webex space
How
Webex spaces will be moderated
by the speaker until June 17, 2022.
1
2
3
4
3
https://ciscolive.ciscoevents.com/ciscolivebot/#BRKSEC-2128
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-2128
3

Agenda
#CiscoLive
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
• Introduction
• Let’s get SASE
• Security Operations Center (SOC)
• Deception in the network
• Use Case
• Conclusion
BRKSEC-2128
4

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
About your speaker
• Cyber Technical Solutions Architect
• Global Security Architecture Team
• Focus on blue team (sometimes purple)
• SANS.edu MSISE student 1/3
rd
along the journey
• GPEN, GCIH, GSEC, GSTRT, CISSP, Former CCIE…
• 23+ year Cisco veteran (Joined September 1998)
• Grew up in Cornwall, England
• Live in Cleveland, Ohio, US
• Wife, Nadine and 4 children
• Dog Person {3 GSPs}
• Fun: Photography, reading, travel, and budding sailor
5
BRKSEC-2128
#216stephens
Mark Stephens: mstephen@cisco.com

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Richard Bejtlich
Tao of Network Security Monitoring
“Three words sums up my attitude
towards stopping intruders:
prevention eventually fails.”
6
BRKSEC-2128

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
The desired outcome
7
BRKSEC-2128

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Shift in IT landscape
Users, devices, and apps are everywhere
8
BRKSEC-2128
Remote users
Personal and
mobile devices
IoT devices
Hybrid
infrastructure
Cloud
infrastructure
Cloud
applications
Evolving
Perimeter

Let’s Get SASE

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Secure Access Service Edge:
Connectivity & Security offered as one single service from the cloud edge
Source: Gartner
SD-WAN Secure Web Gateway
(SWG)
Firewall as a Service
(FWaaS)
Cloud Access Security Broker
(CASB)
Zero Trust
Network Access
(ZTNA)
10
BRKSEC-2128

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
11
BRKSEC-2128
Secure web
gateway
(RBI|DLP))
Cloud access
security broker
(CASB)
S E C U R I T Y A S A S E R V I C E
Adaptive
MFA
C I S C O S A S E
DNS
security
Device posture
and health
Behavior
analytics
SaaS
Continuous
verification
SD- W A N
SD-WAN
fabric
Private/
public cloud
Telemetry
Integrated multi-
cloud access
Application
SLA
Analytics/
automation
Middle-mile
efficiency
SaaS
optimization
L7
firewall
(IPS)
SSO
R A a a S
Internet
Public / private apps
Remote access
Cisco
Secure
Client
DNS / HTTP / HTTPS
Secure TLS
Network edge
SD-WAN
router
SD-WAN mesh
Umbrella tunnel
All ports / protocols
Secure Access Service Edge (SASE)
Simplicity and ease of operation via a turnkey solution

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
12
Highly Flexible Branch Protection
BRKSEC-2128
Internet
DNS LAYER SECURITYSELECTIVE PROXY
DNS
NAT
SIG
DNS
CDFW
SWG
IPS
DNS
DNS DIRECT
Selective proxy
DLP
CASB
Internet Traffic
Public cloud/
SaaS
Internet
Private apps/nets
Co-location nets
Non- T u n n e l e d
I n t e r n e t T r a f f i c
• May be used for Guest Traffic
• DNS Only
• DNS + Selective Proxy
SIG
• DNS
• CDFW
• SWG
• CASB
Internet traffic
SD-WAN Traffic
Tunnel
Multi-layer, flexible protection to
meet each environments needs
Tunneled
Traffic
DIA & Split
Tunnel
RBI
Telemetry Application
SLA
Automation/
Orchestratio
n
Middle-mile
efficiency
SaaS
optimization
SD- W A N
SIG
Private SD-WAN Traffic
SD-WAN
SD- W A N
• Cloud On-Ramp
• Private WAN Apps

Security
Operations
Center (SOC)

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
14
What’s a SOC?
BRKSEC-2128
Reactive to alerts (play books)
Patrol the network looking for incidents
Security Analysts/Incident Responders
An absence of alert
Search for abnormalities
Hunt for TTPs
Presumption of compromise
Threat hunters

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Detection verses Visibility
15
BRKSEC-2128
Detection>alert>response
Anomaly Detection

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
16
Hunting the Known, Knowns
https://blog.talosintelligence.com/2022
/04/threat-roundup-0422-0429.html
https://blog.google/threat-analysis-
group/tracking-cyber-activity-eastern-europe/
https://www.kennasecurity.com/blog/april-
vuln-of-the-month-cve-2022-1096/
National Vulnerability Database
BRKSEC-2128

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Hunting the unknown, unknowns
Log Sources
17
BRKSEC-2128
https://twitter.com/cyb3rops/status/1221580082667499522?s=20
Log Sources
- ordered by priority
- with ratings in different
categories
- personal and highly
subjective assessment
- from my most recent
slide deck on low hanging
fruits in security
monitoring

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Log Details
18
BRKSEC-2128
EDR/EPP

Threat Hunting

ACT
Can you deploy proven countermeasures to evict and recover?
TRACK
During an intrusion, can you observe adversary activity in real time?
HUNT
Can you detect an adversary that is already embedded?
BEHAVIORS
Can you detect adversary activity within your environment?
THREATS
Who are your adversaries? What are their capabilities?
TRIAGE
Can you accurately classify detection results?
DETECTION
Can you detect unauthorized activity?
TELEMETRY
Do you have visibility across your assets?
INVENTORY
Can you name the assets you are defending?
Can you collaborate with trusted partners to disrupt adversary campaigns?
Matt Swann
linkedin.com/in/swannman
BRKSEC-2128 21

TRACK
HUNT
BEHAVIORS
THREATS
TRIAGE
DETECTION
TELEMETRY
INVENTORY
ACT
“During incident response,
I operate at the same tempo
as the adversary to protect
my business assets.”
“When my red team emulates
a real-world adversary, I detect
their intrusion at multiple
points along the kill chain.”
“I detect hygiene issues and
operator activity that does not
follow best practices.”
BRKSEC-2128 22

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
The Threat Hunting Loop
23
BRKSEC-2128
Create
Hypotheses
Investigate via
tools and
techniques
Uncover New
Patterns &
TTPs
Inform &
Enrich
Analytics
Threat Hunting begins with hunters
asking questions:
How would a threat actor infiltrate
our network?
What are the crown jewels
(situational awareness)?
Cannot be
generated by
a tool
Data visibility:
IOC or TTPs?
Test the
theory in
the lab?

Deception in the
network

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
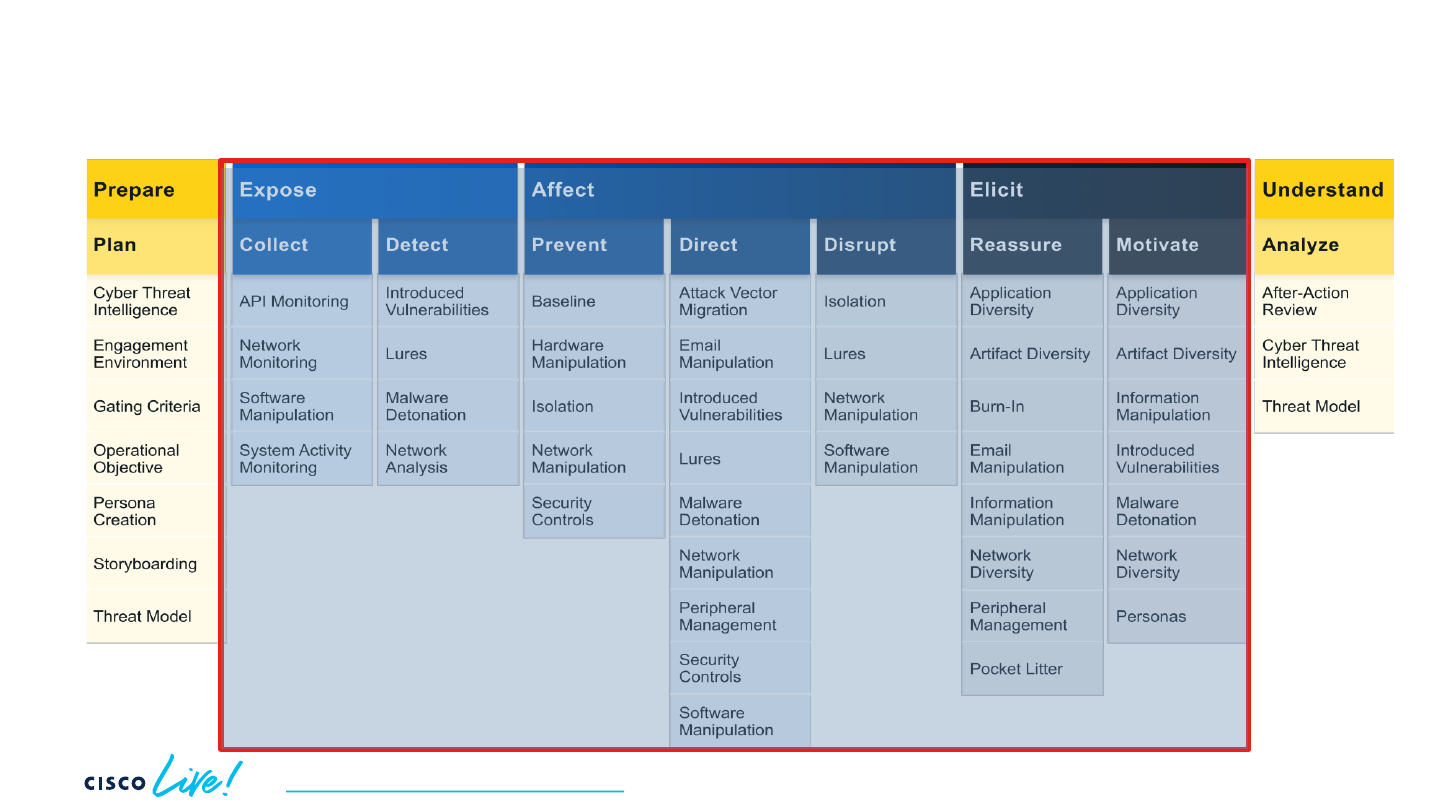
Deploy tripwires and traps - Techniques
Using Engage for Detection - Lures
26
BRKSEC-2128
Decoy Files Honeypots
• Determine the desired outcome
• Select and deploy the techniques that helps achieve that outcome
Darknets
LURES
ID: EAC0005
Deceptive systems and artifacts intended to serve as decoys, or bait to elicit a specific response.
Specific network ranges
not deployed in the
production network for
legitimate traffic
Hidden directories and
files deployed on
managed endpoints with
auditing enabled (logs
generated on access)
Specific hosts or container
deployed to alert if
connections are made,
etc.

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Snort Signature
Zero Trust Tenet: Assume compromise
27
BRKSEC-2128
Alert ip $inside-net any -> $lure_network any (msg:”Lure 1 traffic
detected from an inside network”; sid:5300100;rev:1;)
Alert ip $inside-net any -> $lure_network2 any (msg:”Lure 2 traffic
detected from an inside network”; sid:5300101;rev:1;)

The SASE
architecture

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Umbrella
Secure web
gateway
(RBI|DLP))
DNS
security
L7
firewall
(IPS)
Internet
Private Cloud
10.2.2.0/24
10.3.3.0/24
192.168.200.4
30
A SASE Architecture
BRKSEC-2128

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
On-prem Employee:
Accessing Internet
Employee
Internet
Anti-
Virus
Anti-
Malware
DNS
Security
Connector
Device
Health
Connector
Web
Security
Connector
Mobile
Device
Management
Endpoint Security
Network
Anti-
Malware
Remote
Browser
Isolation
Application
Visibility
Control (AVC)
Intrusion
Prevention
Web
Category
Filtering
Data Loss
Prevention
(DLP)
Cloud
Access
Security
Broker
DNS
Security
Web
Reputation
Filtering
Firewall
Cloud Security
TLS/SSL
Decryption
Malware
Sandboxing
SD-WAN
Identity
Identity
Access
Policy
Tagging
Architectural
SASE Integrated
BRKSEC-2128
31

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Umbrella
Secure web
gateway
(RBI|DLP))
DNS
security
L7
firewall
(IPS)
Internet
Private Cloud
10.2.2.0/24
10.3.3.0/24
192.168.200.4
32
A SASE Architecture
BRKSEC-2128
Discovery
Telemetry
Policy
Logging
enforcement
Policy
Logging
enforcement
Management Consoles

Story Line

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Red Team Persona
34
BRKSEC-2128
• Not following the rules
• Need to be right only once
• Already on the inside

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Red Team Tool
35
BRKSEC-2128
https://github.com/secgroundzero/warberry
Note: This project is no longer being maintained
This is a very dangerous tool. Do not use
it untested in a production environment, it
should be used to train blue teams in a
controlled environment.

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
An insider threat scenario
36
BRKSEC-2128
Visibility and Logs
Action and Vector
Adversary
Connect the WarberryPI to the network
No Unusual
behavior
detected the
adversary is now
positioned to
pivot laterally
The steps of the
adversary (tester)
Network access granted –
profiled as Video Endpoint
Tcp:8884
Miredo -Teredo
Tunnel outbound
Inbound SSHo v6
Open Listening Service (netcat)
Social Engineering
Auctioned Domain
Switch state change logs
Firewall logs
https://autions.godaddy.com
Policy Auth & authz logs
Netflow logs
Netflow logs

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
No Alerts so not on
the SOC’s radar
37
BRKSEC-2128

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Threat Hunting Routine
38
BRKSEC-2128
• Think like an adversary
• How would data be exfiltrated
• Where are the “crown jewels”
• Investigate top talkers
• Low and slow

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
An insider threat scenario – part 2
39
BRKSEC-2128
SOC
Action and Vector
Adversary
While a level of
compromise
occurs, damaged
is limited and the
time for defense
systems to detect
and respond is
greatly restricted
An example of
the steps of the
adversary and
the defender
Tcp:8884
Inbound SSHo v6
Open Listening
Service (netcat)
HoneyWhale
Internal DNS
Collect Endpoint info
Netflow logs
Firewall logs
DNS logs
Netflow logs
Active Defense Log
IP Address
Physical location
Out bound and inbound services/traffic
Declare incident….
?

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Revealed Bad Actor in Every Scooby-doo episode
“ And I would have gotten away with it
too, if it wasn’t for you meddling kids.”
40
BRKSEC-2128

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Why is SASE the SOCs New BFF?
41
BRKSEC-2128
• Security is an integrated part of the architecture
• SASE is policy based by default
• Detailed traffic and access logs
• Easy to add low risk active defense components
• Operational advantages due to low maintenance (no code
upgrades)

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Where next?
• Combine SASE network and security architecture team
• MFA + risk-based assessment when you can
• Log and flow analysis
• Hunt for the unusual
• Change the mindset to one of assumed compromised
42
BRKSEC-2128
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Continuous Learning
43
BRKSEC-2128
https://www.sans.org/cyber-security-courses/defensible-security-architecture-and-engineering/
https://detectionlab.network
DetectionLab was built with defenders in mind. Offensive
security practitioners have entire Linux distributions
dedicated to streamline their work, so DetectionLab is my
effort to simplify testing, analysis, research for defensive
security practitioners.

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Technical Session Surveys
• Attendees who fill out a minimum of four
session surveys and the overall event
survey will get Cisco Live branded socks!
• Attendees will also earn 100 points
in the Cisco Live Game for every
survey completed.
• These points help you get on the
leaderboard and increase your chances
of winning daily and grand prizes.
BRKSEC-2128
44

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Threat Intelligence | Malware Analytics | Actionable Intelligence | Unmatched Visibility | Collective Responses
Security Operations
(XDR)
Threat Visibility & Hunting
Managed Detection
and Response Services
3rd Party Integrations
Security, Orchestration, Automation and Response Incident Response and Remediation Services
Secure Cloud InsightsKenna Vuln MgmtDevice Insights
Security Reference Architecture
User/Device Security
Adaptive MFA | Passwordless | Trust
ZERO TRUST
Secure
E-mail
Duo Secure
Access
SASE/REMOTE WORKER
Unified Client | EDR | Cloud Managed
Network Security
DNS-layer
security
L7 firewall
+ IPS
Secure web
gateway
Cloud access
security broker/
shadow IT
SSL
decryption
Remote
browser
Isolation
Data loss
prevention
Cloud
malware
detection
RAaaS
ZTNA
Umbrella/Duo
Threat Protection | Secure Access Control | Managed Remote Access
Cloud Edge
SECURE ACCESS SERVICE EDGE (SASE) PRIVATE CLOUD EDGE (MSP or CUSTOMER)
Reliable | Scalable | Flexible
ThousandEyes
Secure
Firewall
SDWAN
by Viptela
SDWAN
SDWAN
Cloud
DDoS,WAF
IoT/OT SECURITY
Secure Critical Infrastructure | Unified IT and OT
Cyber
Vision
ISE
TrustSec
Industrial
Router
Industrial
Firewall
Industrial
Switch/AP
On-Premises
Scalable | Flexible | Visibility | Comprehensive Security
Network
Edge
ThousandEyes
Secure
Firewall
SDWAN
by Viptela
SDWAN
SASE/SDWAN
Segmentation | Identity and Context | Profiling | Containment | Encrypted Visibility
ZERO TRUST
Secure Firewall
DuoCloud
SSO+IDP
Secure Web
Appliance
Secure Network
Analytics
ISE
Cisco
DNA Center
TrustSec
Security
Analytics
and Logging
Full Stack
Secure
DDoS
Network
Gateway
Application Security
Policy | API Security
Application Segmentation
Run-time Application Security
ZERO TRUST
Application Security Stack
Cloud Native Security
Secure
Workload
Secure Application
by AppDynamics
APIC-DC
APIC
Hybrid
Private
Secure
Firewall
ThousandEyes
App Observability | Detection | Response
Secure
Cloud Analytics
Public
Cloud
Secure
DDoS, WAF/Bot
Posture
Telemetry
Threat
Query
VPN
ThousandEyes
(Visibility)
Cisco Secure Client
Meraki SM
OS, App Control
Device Mgmt
ZERO TRUST
BRKSEC-2128
45

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
From technology training and team development to Cisco certifications and learning
plans, let us help you empower your business and career. www.cisco.com/go/certs
Cisco Learning and Certifications
Here at the event? Visit us at The Learning and Certifications lounge at the World of Solutions
Pay for Learning with
Cisco Learning Credits
(CLCs) are prepaid training
vouchers redeemed directly
with Cisco.
Cisco Training Bootcamps
Intensive team & individual automation
and technology training programs
Cisco Learning Partner Program
Authorized training partners supporting
Cisco technology and career certifications
Cisco Instructor-led and
Virtual Instructor-led training
Accelerated curriculum of product,
technology, and certification courses
Cisco Certifications and
Specialist Certifications
Award-winning certification
program empowers students
and IT Professionals to advance
their technical careers
Cisco Guided Study Groups
180-day certification prep program
with learning and support
Cisco Continuing
Education Program
Recertification training options
for Cisco certified individuals
Learn
Cisco U.
IT learning hub that guides teams
and learners toward their goals
Cisco Digital Learning
Subscription-based product, technology,
and certification training
Cisco Modeling Labs
Network simulation platform for design,
testing, and troubleshooting
Cisco Learning Network
Resource community portal for
certifications and learning
Train Certify
BRKSEC-2128
46

© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
Continue
your education
• Visit the Cisco Showcase
for related demos
• Book your one-on-one
Meet the Engineer meeting
• Attend the interactive education
with DevNet, Capture the Flag,
and Walk-in Labs
• Visit the On-Demand Library
for more sessions at
www.CiscoLive.com/on-demand
BRKSEC-2128
47

Thank you
#CiscoLive

#CiscoLive